A security appliance is made up of a variety of practices, tools, and strategies that are closely related to information security and operational technology security. By employing both proactive and reactive strategies, this strategy can prevent networks and information from being attacked and compromised. In addition, security appliances combine web filtering, classic malware prevention, and advanced threat defenses to protect consumers from Internet-borne dangers while also assisting companies in ensuring Internet policy compliance.
The increasing frequency of security attacks and destructive actions by professional cybercriminal groups has caused concern among companies of all sizes. As a result of these situations, enterprises have found that outsourcing network security to security equipment service providers is a lucrative option. Furthermore, network security services can be provided by either setting up the appropriate security infrastructure or permitting the service provider to control everything from a remote location.
Increasing cybercrime activities, growing own-device implementation, rising demand for cloud-based solutions, and strict government laws together influence the complete protection appliances market share. Factors such as the need for improved security management have influenced both developed and emerging nations in their attempts to safeguard themselves from unidentified organizations such as cyber-attacks, rivalry, or other disruptive activities.
Network security encompasses both the security of systems and the systems that support operations. Each device, software product, and application used in the network must be inspected and updated to avoid infiltration via a third-party network. By merging third-party systems and apps, Application security is the process of defending against any potential vulnerabilities by combining third-party systems and apps.
COVID-19 Impact Analysis
The COVID-19 pandemic has wreaked havoc on enterprises all over the world. The lockdown imposed by many governments has had a beneficial effect on the adoption of security appliances. Organizations are focused on sophisticated technology in the aftermath of COVID-19. It had an impact on the supply chain, import, and export, as well as the market for security appliances. These were aided by new government rules. Furthermore, due to the industry's ambiguous behavior, the pandemic has resulted in numerous market variations.
Furthermore, to provide security, security appliances are used. The rising use of security-related goods such as electronic and cloud-based locking in commercial, residential, and industrial spaces is propelling growth in the security appliance market.
Market Growth Factors
The increased demand for commercial security appliances
Large businesses encounter a variety of network and data security challenges. Cloud-based applications, mobile devices, and BYOD (bring your own device) laws, if not properly handled, might endanger crucial company data. Large enterprises can use security appliances like firewalls, UTM systems, and VPNs to protect themselves from modern attacks without disrupting business operations or productivity. In addition, many suppliers provide custom solutions for corporations by selling specialist products or services such IDP systems tailored exclusively for the demands of larger companies.
Advantages of the firewall as security appliances
A firewall's primary responsibility is to monitor traffic coming through it. The information that flows over a system is in the form of data packets. Each of these packets is inspected by the firewall for any potential risks. If the firewall finds them by chance, it is expected to start blocking them. Malware, particularly Trojans, are dangerous to consumers. A Trojan sits silently on computer, monitoring whatever consumer work. Whatever data they gather is expected to be transferred to a web application. Obviously, users is expected to not be aware of its presence until machine begins to behave strangely. In this case, a firewall is expected to quickly stop Trojans from causing damage to machine. Firewalls have access control policies that may be used to restrict access to specific hosts and services.
Market Restraining Factors
Drawbacks of utilizing Unified threat management
By merging all security features into one appliance, the system admin can create everything from a single dashboard. It also poses the risk of a single point of failure, exposing the entire network if the UTM device fails. This can be avoided by establishing high availability configurations with redundancy, however this is expected to raise installation and running costs. Components within a Unified threat management appliance may lack the precision and power of standalone appliances' settings and rules. When the UTM appliance maintains a large number of apps/clients with much functionality activated, performance may decrease. The efficiency hit may be less evident than with a dedicated appliance.
Deployment Type Outlook
Based on Deployment Type, the market is segmented into On-premise and Cloud. The on-premise segment procured the highest revenue share in the security appliances market in 2021. This is due to several advantages provided by the on-premise deployment, including increased data security and safety. The on-premise deployment model allows the software to be installed and applications to run on equipment located on the organization's premises rather than at a remote location like a server or the cloud. This paradigm is best suited to applications that require substantial data transfers and processes, such as financial services and health records containing sensitive data.
Industry Outlook
Based on Industry, the market is segmented into BFSI, Energy & Utilities, Manufacturing, Telecom & IT, Aerospace & Defense, Healthcare & Life Sciences, Public Sector, Retail, and Others. The healthcare & life sciences segment recorded a significant revenue share in the security appliances market in 2021. It is because the security of healthcare systems can have a direct effect on the healthcare operational safety and productivity, as well as an indirect impact on services. In addition, the regularity and sophistication of cyber-attacks in the healthcare industry have increased. Moreover, the safety, security, and accuracy of data are critical for these firms, as they must comply with several legal obligations relating to documentation and intellectual property protection.
Type Outlook
Based on Type, the market is segmented into Content Management, Firewall, Virtual Private Network, Intrusion Detection & Prevention, and Unified Threat Management. The content management segment garnered the largest revenue share in the security appliances market in 2021. Due to the rising threat to company networks and data has created a market for a variety of network and information security solutions. The expansion of this category has been spurred by the rise of content data between end-user industries and the increasing complexity associated with critical data. Operators of content management systems must integrate data across all corporate activities, necessitating the deployment of more powerful security to prevent unwanted access and data breaches.
Regional Outlook
Based on Regions, the market is segmented into North America, Europe, Asia Pacific, and Latin America, Middle East & Africa. The North America segment garnered the highest revenue share in the security appliances market in 2021. Widespread technological adoption, a huge number of industry players, and new solutions are involved. Furthermore, factors such as the move to remote work and the increased threat of external threats are increasing the use of intrusion detection systems in this region, providing lucrative development potential.
The major strategies followed by the market participants are Acquisitions. Based on the Analysis presented in the Cardinal matrix; Intel Corporation are the forerunners in the Security Appliances Market. Companies such as Cisco Systems, Inc., Check Point Software Technologies Ltd., Fortinet, Inc. are some of the key innovators in the Market.
The market research report covers the analysis of key stake holders of the market. Key companies profiled in the report include Cisco Systems, Inc., Check Point Software Technologies Ltd., Broadcom, Inc., Intel Corporation, Fortinet, Inc., Palo Alto Networks, Inc., Bosch Security Systems GmbH, Honeywell International, Inc., Trend Micro, Inc., and Juniper Networks, Inc.
» Partnerships, Collaborations and Agreements:
- Mar-2022: Palo Alto Networks came into a partnership with Amazon Web Services, an online platform that provides scalable and cost-effective cloud computing solutions. This partnership aimed to launch Palo Alto Networks Cloud NGFW for AWS a controlled Next-Generation Firewall service developed to clarify securing AWS deployments allowing the enterprise to accelerate pace of innovation while outstanding safety.
- Feb-2022: Check Point Software Technologies came into a partnership with Redington India, the biggest IT software and products supplier in India. Together, the companies aimed to offer unbending security to the Small and Medium-Sized enterprise market in India.
- Nov-2021: Check Point Software Technologies came into a partnership with Eagle Tech Corp, a leading Managed Security Services supplier. Through this partnership, the companies aimed to offer a combined IT Security Suite bundle to international, commercial, government, and non-profit enterprises.
- Nov-2021: Palo Alto Networks formed a partnership with Siemens, a global powerhouse focusing on the areas of electrification, automation, and digitalization. Through this partnership, the companies aimed to combine Palo Alto Networks VM-Series Virtual Next-Generation Firewalls within Siemens Ruggedcom Multi-Service Platforms to allow constant ascendable hardware that is expected to enable consumers to prolong consistent security policy and transparency across crucial OT, IT, and industrial control systems architecture. Additionally, the partnership is expected to enhance the security of crucial networks and avoid the risk of cyberattacks on crucial architecture.
- Sep-2021: Juniper Networks signed a Technology Alliance Partner Connect agreement with Arqit Quantum, a leader in quantum encryption technology. This agreement aimed to deliver network security technology that is expected to secure against quantum security risks. Additionally, Arqit and Juniper is expected to examine how network suppliers can apply quantum-protected key-exchange mechanisms to limit interference and enhance organizational flexibility.
- Jul-2021: Palo Alto Networks came into a partnership with Google Cloud, a suite of public cloud computing services offered by Google. Through this partnership, the companies aimed to develop Cloud IDS, a combined designed network hazard tracking service to assist cloud consumers to solve crucial network safety difficulties. Additionally, the new service is a joint design and engineering attempt between Google and Palo Alto Networks, concentrated on integrating the dominant security of Palo Alto Networks with the clarity, protected, and scalable architecture of Google Cloud.
- Jul-2021: Trend Micro Incorporated joined hands with Microsoft, an American multinational technology corporation. Through this collaboration, the companies aimed to provide new assistance in designing cloud-based cybersecurity solutions on Microsoft Azure and creating co-selling chances.
- Nov-2020: Honeywell came into a partnership with Nozomi Networks, the leader in OT and IoT security and visibility. Through this partnership, the companies aimed to provide complete solutions to control cybersecurity conformity and minimize the risk of intermission due to cyberattacks.
» Product Launches and Product Expansions:
- Feb-2022: Fortinet introduced FortiGate 3000F, the latest Next-Generation Firewall. FortiGate 3000F supports the enterprise in developing hybrid IT infrastructure to boost digital innovation and propel company growth. Additionally, FortiGate 3000F allows ultra expandable, security-operated networks that effortlessly assemble security and networking without affecting security performance.
- Feb -2022: Palo Alto Networks introduced Nebula, the latest advancement of its industry-leading PAN-OS software. The Nebula analyzes, interprets, and collects possible zero-day risk in actual time utilizing inline deep learning, network security first.
- Feb-2022: Juniper Networks introduced Juniper Secure Edge, the newest addition to its Secure Access Service Edge architecture. The juniper Secure Edge provides Firewall-as-a-Service as a single-stack software infrastructure, controlled by Security Director Cloud, to authorize enterprises to secure manpower, from anywhere.
- Jan-2022: Check Point Software Technologies expanded its Check Point Quantum offering with Quantum Lightspeed Firewalls. The expanded suite provides advanced firewall performance that enables an organization to support elephant stream and safely moves terabytes of data in minutes.
- Nov-2021: Juniper Networks unveiled Juniper Support Insights, two new Wi-Fi 6E access points. The Juniper Support Insights offers artificial intelligence and provides transparency and insights around the supplier Junos offering. Additionally, it is easier for service distributors, companies, and partners to advance the operation of networks.
- Sep-2021: Palo Alto Networks launched Prisma SASE, and combined Prisma Access and Prisma SD-WAN. The Prisma SASE assure the enterprise stay productive and secure while working smoothly between home offices and branch offices.
- Jun-2021: Cisco unveiled a new offering of Catalyst industrial routers. The new suite offers the power of the company network to the edge with the security, scalability, and flexibility required for IoT success. Moreover, presenting 5G abilities, the suite allows the enterprise to play connected working at scale with the option of administration tools appropriate for both operations and IT. Additionally, The consolidated infrastructure clarifies collaboration between operations and IT to simplify deployments from the organization to the edge.
- Nov-2020: Check Point Software Technologies unveiled Check Point R81, a next-generation unified cyber security platform. The Check Point R81 offers independent hazard avoidance developed for the complete dispense organization, allowing IT staff to control the most dynamic and complicated network ecosystem efficiently and easily.
- Sep-2020: Honeywell introduced Pro-Watch, a software platform designed to help protect people and property. The Pro-Watch delivers the entire transparency of all connected systems and the adaptability of the software makes it comfortable to advance with the changing demands of an enterprise.
» Acquisitions and Mergers:
- Mar-2022: Intel Corporation signed an agreement to acquire Granulate Cloud Solutions, a developer of real-time continuous optimization software. Through this acquisition, Granulate is expected to assist data and cloud center consumers to maximize compute assignment performance and minimize architecture and cloud price.
- Feb-2022: Check Point Software Technologies completed the acquisition of Spectral, Israel-based Spectral targets code safety and trust, fast code scanning, and delivering a simple developer experience. Together, the companies aimed to integrate Check Point’s cloud security abilities and risk intelligence tools within Spectral’s security equipment for designer is expected to make it achievable for companies to implant security earlier in the software growth life cycle.
- Feb-2022: Juniper Networks completed the acquisition of WiteSand, a pioneer of cloud-native zero trust Network Access Control solutions. This acquisition aimed to bring a highly skilled engineering group and extraordinary technology to Juniper, boosting the enterprise's ongoing efforts to provide a next-era NAC solution as a key element of the AI-driven company suite.
- Nov-2021: Check Point Software Technologies completed the acquisition of Avanan, a leader in cloud email security and collaboration portfolio. This acquisition aimed to deliver Avanan's dominating API-based security redefines cloud email safety and provides best-of-breed email virus protection.
- Jun-2021: Cisco took over Kenna Security, a cybersecurity leader that provides a risk-based management platform. Through this acquisition, Cisco can link its threat administration with Kenna's risk-based accountability management to reinforce Cisco's entire platform.
- Mar-2021: Fortinet completed the acquisition of ShieldX, a cloud and network security startup. Under this acquisition, Fortinet and ShieldX has produced a combined portfolio to confront lateral movement precaution along with the intersection of campus, OT, and various cloud data center subdivisions.
- Feb-2021: Cisco completed the acquisition of IMImobile, which provides cloud communications software and services. This acquisition aimed to integrate IMImobile solution capability within All-New Webex Contact Center, Cisco is expected to be capable to offer a robust consumer Experience as a Service provider.
- Dec-2020: Fortinet completed the acquisition of Panopta, a SaaS monitoring platform. Through this acquisition, the company aimed to integrate Fortinet’s Security Fabric within the Panopta network monitoring and diagnostics platform, allowing Fortinet to provide the most extensive security and network operations administration solution for companies or service distributors.
- Jul-2020: Cisco acquired Fluidmesh Networks, a leader in resilient wireless backhaul systems. Under this acquisition, Cisco's scale is expected to integrate with Fluidmesh’s solution-based suite and relationships with systems integrators, boost Cisco’s factory IoT corporation, and allows wireless distribution within the industrial ecosystem.
- Jul-2020: Fortinet took over OPAQ Networks, a Secure Access Service Edge cloud provider. Through this acquisition, the company aimed to integrate Fortinet’s Security Fabric within the OPAQ ZTNA solution to improve Fortinet’s actual SASE suite to form the superior SASE cloud security platform with the enterprise only true Zero Trust entry and guard.
Scope of the Study
Market Segments Covered in the Report:
By Deployment Type
- On-premise
- Cloud
By Industry
- BFSI
- Energy & Utilities
- Manufacturing
- Telecom & IT
- Aerospace & Defense
- Healthcare & Life Sciences
- Public Sector
- Retail
- Others
By Type
- Content Management
- Firewall
- Virtual Private Network
- Intrusion Detection & Prevention
- Unified Threat Management
By Geography
- North America
- US
- Canada
- Mexico
- Rest of North America
- Europe
- Germany
- UK
- France
- Russia
- Spain
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Singapore
- Malaysia
- Rest of Asia Pacific
- LAMEA
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Key Market Players
List of Companies Profiled in the Report:
- Cisco Systems, Inc.
- Check Point Software Technologies Ltd.
- Broadcom, Inc.
- Intel Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- Bosch Security Systems GmbH
- Honeywell International, Inc.
- Trend Micro, Inc.
- Juniper Networks, Inc.
Unique Offerings from KBV Research
- Exhaustive coverage
- The highest number of Market tables and figures
- Subscription-based model available
- Guaranteed best price
- Assured post sales research support with 10% customization free
Table of Contents
Companies Mentioned
- Cisco Systems, Inc.
- Check Point Software Technologies Ltd.
- Broadcom, Inc.
- Intel Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- Bosch Security Systems GmbH
- Honeywell International, Inc.
- Trend Micro, Inc.
- Juniper Networks, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 270 |
| Published | May 2022 |
| Forecast Period | 2021 - 2028 |
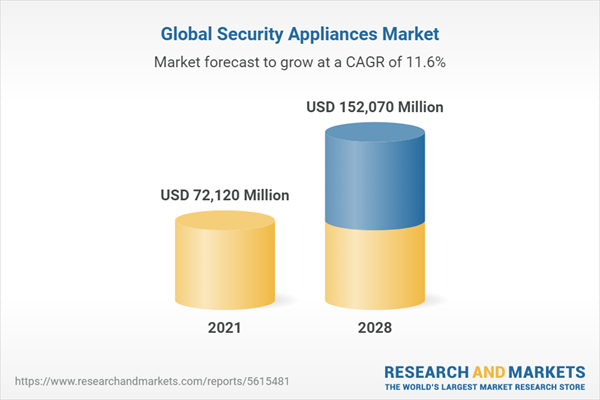
| Estimated Market Value ( USD | $ 72120 Million |
| Forecasted Market Value ( USD | $ 152070 Million |
| Compound Annual Growth Rate | 11.5% |
| Regions Covered | Global |
| No. of Companies Mentioned | 10 |