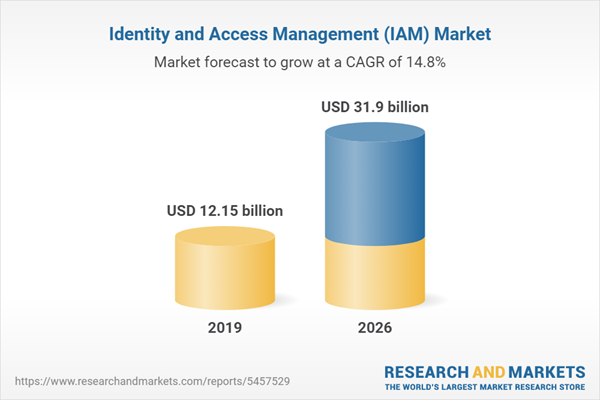
The identity and access management market was estimated at US$12.146 billion in the year 2019 and is projected to grow at a CAGR of 14.79% to reach a market size of US$31.898 billion by the year 2026. IAM (identity and access management) is a set of corporate procedures, rules, and technology that makes managing electronic or digital identities easier. Information technology (IT) administrators may limit user access to important information within their businesses using an IAM architecture. Single sign-on systems, two-factor authentication, multifactor authentication, and privileged access management are examples of IAM systems. These technologies also allow for the safe storage of identification and profile data, as well as data governance features that guarantee that only essential and relevant data is exchanged.
Increased digitization and the introduction of sophisticated technologies are driving the global Identity & Access Management (IAM) market. Furthermore, factors such as the growing need for security governance, enforcement issues, dispersed systems and workforce, and poorer quality security services inside businesses, among others, are projected to drive the market even further throughout the forecast period.
Blockchain technology is slowly making its way into the IAM space, intending to create a platform that protects people's identities from being stolen or becoming victims of different fraudulent acts. To cope with the difficulties of authentication and authorization, businesses have implemented blockchain technology into IAM. Blockchain technology allows users to store and verify the evidence of identity identifiers in a decentralized and relatively safe manner. In IAM systems, blockchain technology assists users in creating, proving, and registering their own identity and associated identifiers to access digital services. By removing the requirement for segregated or replicated identities, repositories, and data, blockchain-enabled IAM solutions in companies can help enterprises reduce operational risks and expenses. However, for blockchain technology to be widely adopted in IAM, it must be open-source, have simple financial models, adhere to privacy by design, and provide a satisfactory user experience.
Companies use identity and access management systems to control and reduce cybercrime by ensuring that the appropriate individuals have access to the right information. Several compliance requirements may be met using identity and access management solutions. If a company is audited and has a solid IAM program, it can readily demonstrate that it has taken steps to reduce the risk of data theft or abuse. It also aids in meeting the requirements of different regulations, such as Sarbanes-Oxley (SOX) and the Gramm-Leach-Bliley Act (GBLA).
To fulfill privacy compliance standards, identity and access management is constantly changing across multiple essential services such as authentication and data security. The use of artificial intelligence (AI) and machine learning in IAM is likely to become more common. As an expanding number of devices and systems interact with and learn from one another without human involvement, artificial intelligence in identity management is predicted to change security beyond people, places, and things. It gives both technical and non-technical personnel contextual information, allowing them to perform more efficiently. To strengthen security methods, IAM suppliers have begun to include behavioral data analysis using machine learning. As a result, AI and machine learning are having a significant influence on the security sector. These technologies have been highlighted by providers of identity access management solutions as major potential in the next years.
All authorizations and credentials must be stored in one centralized location when using identity and access management solutions or platforms. If data is not kept securely, there poses a significant danger of an attacker gaining access to the system. As a result, all digital identities have been hacked. Converting resources from an existing legacy system to IAM is also difficult, costly, and time-consuming. Furthermore, while the cloud-based system has many advantages, it has certain security concerns about the data it stores. Credential protection, data breaches, compromised interfaces and APIs, account hijacking, and hostile insiders are among the security problems mentioned.
Asia Pacific (APAC) has seen advanced and rapid adoption of new technologies, and the worldwide IAM market is anticipated to grow at the fastest rate over the forecast period. APAC is made up of key markets like China, Japan, Australia, and India, all of which are projected to have rapid development in the IAM industry. Financial institutions, government, healthcare, retail, education, telecommunications, manufacturing, energy and utilities, transportation and logistics, hospitality, and media and entertainment are projected to embrace IAM solutions at the fastest pace in the area. Flexible economic circumstances, industrialization-motivated policies, political transition, and rising digitization, all of which are projected to have a substantial influence on the business community, would benefit companies operating in the APAC region.
Increased digitization and the introduction of sophisticated technologies are driving the global Identity & Access Management (IAM) market. Furthermore, factors such as the growing need for security governance, enforcement issues, dispersed systems and workforce, and poorer quality security services inside businesses, among others, are projected to drive the market even further throughout the forecast period.
Using blockchain technology to address issues in identity management to offer market opportunities.
Blockchain technology is slowly making its way into the IAM space, intending to create a platform that protects people's identities from being stolen or becoming victims of different fraudulent acts. To cope with the difficulties of authentication and authorization, businesses have implemented blockchain technology into IAM. Blockchain technology allows users to store and verify the evidence of identity identifiers in a decentralized and relatively safe manner. In IAM systems, blockchain technology assists users in creating, proving, and registering their own identity and associated identifiers to access digital services. By removing the requirement for segregated or replicated identities, repositories, and data, blockchain-enabled IAM solutions in companies can help enterprises reduce operational risks and expenses. However, for blockchain technology to be widely adopted in IAM, it must be open-source, have simple financial models, adhere to privacy by design, and provide a satisfactory user experience.
Increasing regulatory compliance awareness to propel adoption.
Companies use identity and access management systems to control and reduce cybercrime by ensuring that the appropriate individuals have access to the right information. Several compliance requirements may be met using identity and access management solutions. If a company is audited and has a solid IAM program, it can readily demonstrate that it has taken steps to reduce the risk of data theft or abuse. It also aids in meeting the requirements of different regulations, such as Sarbanes-Oxley (SOX) and the Gramm-Leach-Bliley Act (GBLA).
Machine learning and Artificial Intelligence to improve risk detection increasing market demand.
To fulfill privacy compliance standards, identity and access management is constantly changing across multiple essential services such as authentication and data security. The use of artificial intelligence (AI) and machine learning in IAM is likely to become more common. As an expanding number of devices and systems interact with and learn from one another without human involvement, artificial intelligence in identity management is predicted to change security beyond people, places, and things. It gives both technical and non-technical personnel contextual information, allowing them to perform more efficiently. To strengthen security methods, IAM suppliers have begun to include behavioral data analysis using machine learning. As a result, AI and machine learning are having a significant influence on the security sector. These technologies have been highlighted by providers of identity access management solutions as major potential in the next years.
Security concerns regarding the stored data to restrain the market growth.
All authorizations and credentials must be stored in one centralized location when using identity and access management solutions or platforms. If data is not kept securely, there poses a significant danger of an attacker gaining access to the system. As a result, all digital identities have been hacked. Converting resources from an existing legacy system to IAM is also difficult, costly, and time-consuming. Furthermore, while the cloud-based system has many advantages, it has certain security concerns about the data it stores. Credential protection, data breaches, compromised interfaces and APIs, account hijacking, and hostile insiders are among the security problems mentioned.
Asia Pacific (APAC) has seen advanced and rapid adoption of new technologies, and the worldwide IAM market is anticipated to grow at the fastest rate over the forecast period. APAC is made up of key markets like China, Japan, Australia, and India, all of which are projected to have rapid development in the IAM industry. Financial institutions, government, healthcare, retail, education, telecommunications, manufacturing, energy and utilities, transportation and logistics, hospitality, and media and entertainment are projected to embrace IAM solutions at the fastest pace in the area. Flexible economic circumstances, industrialization-motivated policies, political transition, and rising digitization, all of which are projected to have a substantial influence on the business community, would benefit companies operating in the APAC region.
Segmentation:
By Deployment Model
- On-Premise
- Cloud
By Service
- Integration & Implementation
- Consulting
- Others
By Vertical
- Travel and Transport
- Government
- Media & Entertainment
- Retail
- BFSI
- Communication and Technology
- Others
By Geography
- North America
- USA
- Canada
- Mexico
- South America
- Brazil
- Argentina
- Others
- Europe
- UK
- Germany
- France
- Spain
- Others
- Middle East and Africa
- Saudi Arabia
- UAE
- Israel
- Others
- Asia Pacific
- Japan
- China
- India
- South Korea
- Taiwan
- Thailand
- Indonesia
- Others
Table of Contents
1. Introduction
2. Research Methodology
3. Executive Summary
4. Market Dynamics
5. Identity And Access Management (IAM) Market Analysis, By Deployment Model
6. Identity And Access Management (IAM) Market Analysis, By Service
7. Identity And Access Management (IAM) Market Analysis, By Vertical
8. Identity And Access Management (IAM) Market Analysis, By Geography
9. Competitive Environment and Analysis
10. Company Profiles
Companies Mentioned
- Centrify Corporation
- Microsoft Corporation
- Dell
- Micro Focus
- Oracle
- Hitachi ID Systems, Inc
- IBM Corporation
- SailPoint Technologies, Inc.
- Okta, Inc.
- Forge Rock
Methodology

LOADING...
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 121 |
| Published | August 2021 |
| Forecast Period | 2019 - 2026 |
| Estimated Market Value ( USD | $ 12.15 billion |
| Forecasted Market Value ( USD | $ 31.9 billion |
| Compound Annual Growth Rate | 14.8% |
| Regions Covered | Global |
| No. of Companies Mentioned | 10 |