Speak directly to the analyst to clarify any post sales queries you may have.
Setting the context for cloud-native application protection by outlining the converging demands of modern development practices and enterprise risk management
The increasing complexity of cloud-native architectures has made application protection a strategic imperative for technology leaders across industries. Modern software portfolios are shifting from monolithic servers to ephemeral workloads, and security programs must evolve accordingly to protect data, identities, network flows, and runtime behaviors in dynamic environments. As teams adopt containerization, microservices, and serverless functions to accelerate delivery, assurance of consistent security controls throughout the software development lifecycle and across heterogeneous clouds is now a primary determinant of resilience and regulatory compliance.
This introduction synthesizes the intersection of secure development practices, platform engineering, and the risk landscape that executives must navigate. It frames cloud-native application protection not merely as a set of point tools but as an integrated program that spans identity and access management, data-centric controls, network microsegmentation, and runtime protection. By establishing this context up front, decision-makers can align organizational priorities, investment roadmaps, and operational models to reduce vulnerability exposure while maintaining developer velocity.
Explaining the major transformative shifts reshaping cloud-native protection including architectural evolution, developer-centric security, and evolving threat tactics
The security landscape for cloud-native applications is undergoing transformative shifts driven by architectural, operational, and regulatory forces that change how protection is designed and delivered. First, adoption of microservices architectures and distributed telemetry has increased attack surface complexity and added new classes of vulnerabilities tied to service-to-service communications and configuration drift. Second, the DevSecOps movement has moved security left, promoting automation, policy-as-code, and shift-right observability, which together require protection platforms to embed seamlessly into CI/CD pipelines and runtime environments.
In addition, cloud providers are continuously expanding native security primitives, compelling vendors to provide value through cross-cloud consistency and advanced threat analytics rather than simply rebranding provider features. Threat actors are also adapting, using identity-based attacks and supply chain exploits that necessitate stronger identity and access governance as well as runtime anomaly detection. Finally, an operational shift toward platform engineering and internal developer platforms increases demand for developer-friendly security controls that are declarative, composable, and enforceable without blocking innovation. Taken together, these shifts require holistic security platforms that balance prevention, detection, and rapid response across diverse deployment patterns.
Analyzing how 2025 tariff developments and trade policy shifts are influencing procurement, supply chain resilience, and the preference for software-first security delivery
The imposition of tariffs and trade policy adjustments in 2025 has introduced a new layer of operational complexity for organizations procuring cloud-native security technologies and related hardware. Supply chain resilience has become a higher priority as procurement teams re-evaluate vendor relationships and total landed cost of security appliances, managed services, and integration support. In response, security architects are increasingly factoring geopolitical risk into vendor selection criteria and opting for software-centric solutions that reduce dependence on specialized hardware subject to cross-border duties.
Concurrently, procurement cycles have lengthened in some industries as legal and compliance teams expand scrutiny of contractual terms, export controls, and third-party risk assessments. This has accelerated interest in subscription and service-based delivery models that shift capital expenditures to operational spend and offer more predictable, tariff-insulated procurement paths. As organizations adapt, security programs that emphasize modular deployment, cloud-native delivery, and vendor-agnostic interoperability gain favor because they reduce exposure to tariff-driven cost variability while preserving the agility needed to respond to emergent threats.
Delivering nuanced segmentation-driven insights that map protection capabilities and deployment patterns to enterprise size, application archetypes, and industry-specific risk profiles
Insightful segmentation illuminates which protection capabilities and deployment patterns are most relevant to differing use cases and buyer profiles. Based on protection type the market divides into data protection, identity and access management, network protection, and runtime protection, with identity and access management further broken into multi-factor authentication, role-based access control, and single sign-on to reflect layered access controls. This protection-type view helps security architects prioritize controls for data-in-motion and data-at-rest as well as for managing human and machine identities across dynamic workloads.
Based on deployment model the landscape spans hybrid cloud, private cloud, and public cloud, each presenting distinct operational constraints and integration patterns, which makes cross-environment policy consistency and centralized observability essential. Based on application type the analysis covers containerized applications, microservices, serverless functions, and VM-based applications, and it drills into containerized workloads through Kubernetes distribution differences such as Amazon EKS, Azure AKS, Google GKE, Red Hat OpenShift, and Vanilla Kubernetes while also recognizing serverless vendor ecosystems including AWS Lambda, Azure Functions, Google Cloud Functions, and IBM Cloud Functions. This application-type segmentation exposes where runtime protections, identity controls, and network controls must be adapted for orchestration layer semantics and ephemeral compute models.
Based on enterprise size the segmentation recognizes large enterprises, midmarket enterprises, and small and medium enterprises, acknowledging that organizational scale influences governance frameworks, procurement sophistication, and integration capacity. Finally, based on industry vertical the analysis considers BFSI, energy and utilities, government and public sector, healthcare, IT and telecom, and retail and e-commerce, which highlights the role of regulatory requirements, vertical-specific threat vectors, and legacy modernization pressures in shaping protection priorities. Together, these segmentation lenses provide a comprehensive matrix for matching security capabilities to operational realities and risk appetite.
Highlighting how regional regulatory regimes, cloud adoption maturity, and talent dynamics shape divergent priorities for cloud-native protection across major global markets
Regional dynamics materially influence how organizations prioritize cloud-native protection, driven by differences in regulatory regimes, cloud adoption curves, and talent availability. In the Americas, large cloud service providers and a competitive vendor ecosystem have driven rapid innovation in developer-integrated security tooling, while a concentrated set of hyperscale cloud regions and mature managed service markets have enabled enterprises to operationalize security orchestration and observability at scale. North American and Latin American buyers also navigate diverse regulatory and privacy obligations that shape data protection and identity governance strategies.
Within Europe, Middle East & Africa, regulatory complexity and cross-border data transfer rules play a central role in shaping architecture and vendor selection, encouraging local data residency options and trusted third-party assurances. The region's blend of public sector modernization efforts and industry consolidation leads to demand for customizable, standards-aligned security solutions with strong compliance reporting. In the Asia-Pacific region, rapid cloud adoption and a proliferation of local cloud providers require solutions capable of operating across multiple provider ecosystems with minimal friction. Talent constraints in certain APAC markets amplify interest in managed detection and response offerings and in automation that reduces reliance on specialized security engineering resources. Taken together, these regional differences drive procurement strategies, sourcing decisions, and operational models for cloud-native protection.
Unpacking competitive dynamics and vendor archetypes to guide procurement decisions by balancing enterprise governance, cloud-native integration, and developer experience
Competitive dynamics in the cloud-native protection space reflect a balance between established security vendors, cloud provider-native capabilities, and innovative challengers focused on developer experience and runtime telemetry. Incumbent security vendors bring broad portfolios and enterprise-grade governance controls that appeal to organizations prioritizing centralized policy management and formal compliance workflows. These vendors typically excel at integrating with existing security operations centers and delivering mature incident response playbooks calibrated for complex environments.
Conversely, cloud providers and platform specialists offer tightly integrated primitives that simplify baseline protection for workloads hosted within their ecosystems, but enterprises often require supplementary cross-cloud controls to achieve consistent posture across heterogeneous environments. Challenger vendors contribute rapid innovation in areas such as behavior-based runtime detection, policy-as-code enforcement, and lightweight agent models that minimize performance impact. These vendors frequently prioritize developer ergonomics, offering SDKs, CLI tools, and infrastructure-as-code integrations that streamline adoption. Together, this competitive mix means procurement committees should evaluate providers for cross-environment interoperability, telemetry fidelity, total operational effort, and the ability to integrate with existing identity, logging, and orchestration systems.
Actionable strategic and operational recommendations that align identity-first controls, policy-as-code, and runtime telemetry to reduce exposure and accelerate secure delivery
Leaders seeking to strengthen cloud-native application protection should prioritize a pragmatic portfolio approach that aligns capability deployment with risk exposure and operational maturity. Begin by mapping critical applications to protection tiers and enforce identity-centric controls for both human and machine identities, establishing multi-factor authentication and role-based policies as a foundation. Next, integrate data protection controls into CI/CD pipelines and runtime environments to ensure that secrets management, encryption standards, and access policies travel with the application across development and production environments.
Simultaneously, invest in runtime detection and response that leverages behavioral telemetry and distributed tracing to detect anomalous inter-service activity. Adopt policy-as-code to enable reproducible governance and to accelerate auditability while ensuring policies are testable within developer workflows. For procurement, favor vendors that demonstrate cross-cloud consistency, provide strong APIs for automation, and offer clear integration pathways with existing identity providers and observability stacks. Finally, build organizational capabilities through targeted training for platform and security engineers, establish clear escalation paths between development and security teams, and measure progress using outcomes-focused metrics such as mean time to detect and mean time to remediate so that investments in tooling translate directly into reduced exposure and improved resilience.
Describing a robust mixed-methods research approach that integrates practitioner interviews, hands-on product assessments, and documentary synthesis to validate findings
The research methodology underpinning this analysis combines qualitative expert interviews, technical product assessments, and synthesis of public regulatory and vendor documentation to surface actionable insights. Primary research involved structured conversations with security architects, platform engineers, and procurement leaders across multiple industries to understand real-world operational constraints, integration challenges, and decision criteria. These conversations were complemented by hands-on product evaluations that measured integration approaches, API maturity, and observability fidelity across representative deployment patterns.
Secondary research included a systematic review of policy guidance, white papers, and open-source project documentation to validate technical claims and to align terminology across the study. Comparative analysis emphasized interoperability, telemetry richness, and the degree to which solutions accommodate developer workflows. Throughout the research, rigorous validation steps were applied including cross-referencing practitioner input and technical validation to ensure recommendations are grounded in operational reality and reflect contemporary threat patterns and adoption practices.
Concluding observations that emphasize integrated identity, data, and runtime controls as the foundation for resilient cloud-native application protection
In conclusion, protecting cloud-native applications demands an integrated strategy that reconciles developer velocity with rigorous security controls. Organizations that succeed will embed identity and data protections into the fabric of development and runtime environments, adopt policy-as-code for reproducible governance, and deploy runtime detection that is attuned to distributed system behaviors. Procurement and architecture teams must weigh the trade-offs between provider-native conveniences and the need for cross-cloud consistency, especially as supply chain and trade dynamics introduce new procurement considerations.
As threats evolve to exploit identities, supply chains, and ephemeral compute models, a programmatic approach to protection-one that couples developer-friendly controls with enterprise-grade governance-offers the best path to sustained resilience. The combination of targeted organizational investments, disciplined procurement choices, and prioritized technical controls will enable enterprises to maintain agility while reducing systemic exposure across the lifecycle of cloud-native applications.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
16. China Cloud-native Application Protection Platform Market
Companies Mentioned
The key companies profiled in this Cloud-native Application Protection Platform market report include:- Aqua Security Software Ltd.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- Fortinet, Inc.
- International Business Machines Corporation
- Jit.io Ltd.
- McAfee Corp.
- Microsoft Corporation
- Nukeware Technologies Private Limited
- Orca Security LTD
- Palo Alto Networks, Inc.
- SecPod Technologies
- SentinelOne, Inc.
- Sweet Security Inc.
- Sysdig, Inc.
- Trend Micro Incorporated
- Upwind Security, Inc.
- Wiz, Inc.
- Zscaler, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 194 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
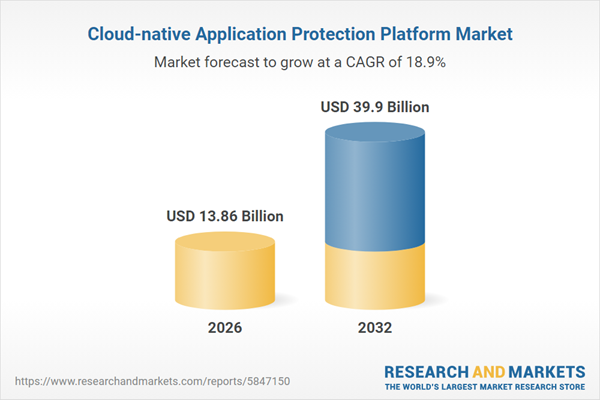
| Estimated Market Value ( USD | $ 13.86 Billion |
| Forecasted Market Value ( USD | $ 39.9 Billion |
| Compound Annual Growth Rate | 18.8% |
| Regions Covered | Global |
| No. of Companies Mentioned | 20 |