Speak directly to the analyst to clarify any post sales queries you may have.
An authoritative introduction to cognitive security as an adaptive, AI-driven discipline that integrates behavior and context to strengthen enterprise defenses
Cognitive security harnesses advanced artificial intelligence techniques to detect, interpret, and respond to complex cyber threats by emulating human-like reasoning and contextual awareness. This introduction frames the discipline as an evolution of traditional security paradigms, where deterministic rules yield to adaptive models that learn from behavior, language, and visual indicators. Practitioners increasingly combine computer vision, machine learning, and natural language processing to build systems that correlate disparate telemetry and surface high-fidelity signals for analysts.As organizations confront more sophisticated threat actors, cognitive security shifts the emphasis from isolated alerts to ecosystem-level context. Solutions that integrate behavioral analytics, security information and event management, and threat detection and response platforms create a layered defense that improves detection speed and reduces false positives. Meanwhile, services spanning deployment and integration, support and maintenance, and training and consulting play an essential role in operationalizing these capabilities and ensuring that models remain calibrated to evolving environments.
This introduction also underscores the importance of aligning technology choices with organizational needs, deployment constraints, and industry-specific risk profiles. Whether deployed on-premise or in cloud-based architectures, cognitive security requires clear governance, explainability, and ongoing oversight to maintain trust and regulatory compliance. Consequently, leaders must adopt a pragmatic roadmap that balances innovation with measurable outcomes and resilient operational practices.
How converging AI technologies and evolving operational models are reshaping cognitive security and redefining detection, response, and governance
The landscape for cognitive security is undergoing transformative shifts driven by converging technological advances, evolving threat methodologies, and changing enterprise architectures. Machine learning models now operate at scale to detect subtle anomalies, while natural language processing enables automated interpretation of threat intelligence and insider communications. Computer vision increasingly augments monitoring in physical and hybrid environments, creating new use cases for situational awareness. Together, these technologies enable security teams to move from reactive investigation toward proactive threat hunting and automated response.Concurrently, the security stack is consolidating: platforms that combine behavioral analytics, SIEM capabilities, and threat detection and response functions reduce friction between detection and remediation. The services ecosystem adapts by emphasizing deployment and integration expertise, sustained support and maintenance, and specialized training and consulting to bridge the skills gap. This transition demands that vendors and practitioners prioritize explainable AI, model governance, and privacy-preserving techniques to maintain stakeholder trust.
Finally, operational models are shifting with organizations embracing hybrid deployment modes. Cloud-based solutions accelerate innovation cycles and enable collaborative intelligence sharing, while on-premise deployments remain relevant where data sovereignty or latency concerns persist. As a result, strategy leaders must evaluate technology choices through a lens of interoperability, scalability, and long-term resilience to address both immediate threats and future uncertainties.
An analytical exploration of how trade policy shifts in 2025 influenced procurement, deployment choices, and vendor strategies across cognitive security solutions
The imposition of tariffs and trade measures by the United States in 2025 introduced layered supply-chain friction that affected procurement, pricing dynamics, and vendor route-to-market strategies for cognitive security technologies. Hardware-dependent offerings, particularly those requiring specialized accelerators or edge devices, experienced extended lead times and increased landed costs that motivated procurement diversification and closer scrutiny of total cost of ownership. In response, many organizations prioritized software-centric approaches and cloud-based alternatives to mitigate capital exposure.Moreover, the tariff environment accelerated the regionalization of sourcing strategies and encouraged strategic partnerships with local integrators and managed service providers to preserve deployment velocity. Vendors adapted by modularizing solutions to allow greater flexibility in component sourcing and by expanding services such as deployment and integration and support and maintenance to offset transactional procurement challenges. These strategic adaptations reduced operational disruption and enabled continuity of security posture evolution despite cross-border trade constraints.
At the same time, tariffs prompted renewed emphasis on interoperability and vendor-neutral architectures. Enterprises invested in cognitive security platforms, behavioral analytics, and SIEM integrations that could accommodate heterogeneous infrastructure, enabling them to switch underlying components without wholesale platform migrations. In short, trade policy dynamics catalyzed pragmatic shifts in procurement behavior, accelerated software-led adoption patterns, and reinforced the strategic value of services that embed domain expertise into deployments.
Deep segmentation insights that connect components, security types, technologies, applications, deployment modes, end users, and enterprise size to strategic adoption levers
Segmentation insights reveal differentiated adoption drivers and operational priorities across components, security types, technologies, applications, deployment modes, end users, and enterprise sizes. When viewed through the prism of component composition, solutions such as behavioral analytics, cognitive security platforms, SIEM, and threat detection and response platforms anchor strategic capabilities, while services focused on deployment and integration, support and maintenance, and training and consulting are essential to translating sophisticated tooling into measurable security outcomes. This interplay underscores the necessity of pairing product innovation with robust services to sustain efficacy over time.Considering security types, organizations prioritize cloud security where workloads and data concentration demand adaptive controls, while endpoint and network security remain vital for real-time telemetry and containment. Application security continues to require contextual analysis that integrates code-level signals with runtime behavior. From a technology perspective, machine learning drives pattern recognition and predictive capabilities, natural language processing powers intelligence synthesis and automated triage, and computer vision expands detection into physical and hybrid domains, thereby broadening the surface for cognitive insights.
Application-driven use cases such as anomaly detection, fraud detection and prevention, risk and compliance management, and threat intelligence map to distinct operational workflows and stakeholder requirements. Deployment mode choices between cloud-based and on-premise architectures influence performance, governance, and integration complexity. End-user segmentation across industries including banking, financial services and insurance, energy and utilities, government and defense, healthcare, IT and telecommunication, manufacturing, and retail reveals sector-specific compliance and resilience expectations. Finally, enterprise size differentiates resource availability and procurement models: large enterprises invest in integrated platforms and internal centers of excellence, while SMEs often rely on managed services and packaged solutions to achieve strong outcomes with constrained budgets.
Regional dynamics and regulatory influences across the Americas, Europe Middle East & Africa, and Asia-Pacific that determine deployment preferences and sourcing strategies
Regional dynamics shape demand, regulatory requirements, and technology sourcing patterns across three macro regions: the Americas, Europe, Middle East & Africa, and Asia-Pacific. In the Americas, innovation clusters and mature security operations drive interest in cognitive platforms, behavioral analytics, and integrations with advanced SIEM capabilities, while regulatory emphasis on data protection fosters investment in explainable models and privacy-aware architectures. Organizations often pursue cloud-based offerings, but hybrid deployments remain common to balance control with agility.Across Europe, Middle East & Africa, regulatory complexity and data sovereignty concerns steer many institutions toward on-premise or hosted solutions that offer local control. Governments and defense sectors emphasize hardened deployments and compliance-focused applications such as risk and compliance management, whereas private-sector adoption follows sectoral patterns in financial services, healthcare, and telecommunications. Meanwhile, managed services and regional systems integrators play a pivotal role in bridging capability gaps and accelerating operational adoption.
Asia-Pacific presents a heterogeneous environment where rapid digital transformation fuels demand for AI-driven detection and fraud prevention capabilities, and where edge and hybrid deployments support large-scale, latency-sensitive use cases. Regional supply chains and local technology ecosystems also influence procurement choices, prompting vendors to tailor deployment and integration services to meet diverse regulatory and operational requirements. Collectively, these regional trends highlight the importance of adaptable delivery models and localized support for sustained adoption.
How leading and specialized companies differentiate through platform integration, vertical focus, and service-led delivery to accelerate cognitive security adoption
Company-level insights highlight how leading providers differentiate through platform integration, vertical specialization, and an expanded services portfolio to support end-to-end adoption. Market leaders combine core capabilities-behavioral analytics, SIEM integration, threat detection and response-with value-added modules such as explainability, model governance, and automated orchestration to streamline analyst workflows. Differentiation also emerges from sector-specific templates and prebuilt playbooks that accelerate time-to-value for industries with stringent compliance requirements.In addition, successful companies emphasize partnerships with system integrators and managed security service providers to extend reach and ensure operational continuity. They invest in professional services that span deployment and integration, ongoing support and maintenance, and training and consulting to close skill gaps and embed security practices across operational teams. Product roadmaps increasingly prioritize interoperability, modular licensing, and ease of deployment across cloud-based and on-premise environments.
Smaller and niche vendors compete by specializing in specific technology areas such as advanced NLP for intelligence synthesis or computer vision for physical security use cases, and by offering lightweight, managed offerings tailored to SMEs. Across the competitive landscape, companies that pair technological innovation with disciplined delivery models and clear proofs of efficacy tend to achieve stronger adoption and enduring customer relationships.
Actionable recommendations for leaders to operationalize cognitive security through pragmatic architectures, service investments, and accountable governance
Industry leaders should pursue a pragmatic, phased approach to embed cognitive security capabilities while preserving operational resilience. Start by aligning executive objectives with security use cases that offer clear operational impact, such as anomaly detection tied to fraud prevention or risk and compliance workflows that reduce manual overhead. In parallel, prioritize architectures that enable interoperability between cognitive security platforms, SIEM, and threat detection and response modules to avoid vendor lock-in and preserve flexibility.Invest in the services necessary to translate technology into outcomes: deployment and integration to ensure seamless telemetry ingestion, support and maintenance to sustain model performance, and training and consulting to upskill security teams. Emphasize explainability, transparency, and model governance to satisfy auditors and maintain stakeholder trust. Where tariffs or supply-chain constraints increase hardware costs, favor software-centric deployments and cloud-based delivery where permissible, while maintaining options for on-premise deployments in regulated contexts.
Finally, cultivate strategic partnerships with regional integrators and managed service providers to localize support and accelerate rollouts across diverse geographies. Establish metrics that measure detection quality, analyst efficiency, and mean time to response rather than binary adoption counts, and iterate based on operational feedback to drive continuous improvement.
A transparent, reproducible research methodology blending primary practitioner interviews and secondary technical validation to inform actionable intelligence
The research methodology combines qualitative and quantitative approaches to derive comprehensive insights into cognitive security adoption and operational dynamics. Primary research included structured interviews with security leaders, technology architects, and managed service providers to capture real-world deployment experiences, procurement considerations, and operational challenges. Secondary research encompassed a review of open-source technical literature, vendor whitepapers, regulatory guidance, and industry-focused reports to contextualize technological capabilities and governance trends.Analytical frameworks emphasized segmentation across components, security types, technologies, applications, deployment modes, end users, and enterprise size to ensure findings map to distinct stakeholder needs. The study applied rigorous validation techniques, triangulating interview feedback with documented product capabilities and deployment case studies. Attention to methodological transparency guided the treatment of sensitive or proprietary data, and all interpretations prioritized reproducibility and traceability to the original sources.
Ethical considerations and data privacy principles informed the assessment of cognitive approaches, with particular emphasis on explainability and model governance. While the methodology sought a broad and representative sample of practitioners, the analysis remained mindful of regional heterogeneity and industry-specific constraints that influence the generalizability of certain operational recommendations.
Concluding synthesis on how AI-driven cognitive security, paired with disciplined operational execution, yields resilient detection and response capabilities
In conclusion, cognitive security represents a strategic inflection point for organizations seeking to elevate their detection and response capabilities through AI-driven context and behavioral insight. The discipline fuses machine learning, natural language processing, and computer vision into integrated platforms that reduce noise, accelerate triage, and enable proactive defense. Services that support deployment, integration, and continuous tuning remain indispensable to realize promised outcomes and sustain resilience over time.External factors such as trade policy shifts have underscored the need for procurement agility and software-first strategies, while regional regulatory landscapes demand tailored deployment and governance postures. Segmentation across components, security types, technologies, applications, deployment modes, end users, and enterprise size illuminates diverse pathways to adoption, suggesting that no single approach fits all organizations. Ultimately, success hinges on pairing technological rigor with operational discipline: clear use cases, interoperable architectures, accountable governance, and iterative measurement of operational impact.
Leaders who combine strategic vision with disciplined execution will be best positioned to translate cognitive security capabilities into measurable risk reduction and operational efficiency, while maintaining the flexibility to adapt as threats and technologies evolve.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
19. China Cognitive Security Market
Companies Mentioned
The key companies profiled in this Cognitive Security market report include:- Acalvio Technologies, Inc.
- Amazon Web Services, Inc.
- BlackBerry Limited
- Broadcom, Inc.
- Capgemini
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- CrowdStrike Holdings, Inc.
- CY4GATE SpA
- Cyberark Software Ltd.
- Darktrace Holdings Limited
- Deep Instinct Ltd.
- DXC Technology Company
- Feedzai
- FireEye, Inc.
- Fortinet, Inc.
- Google LLC by Alphabet Inc.
- Infosys Limited
- International Business Machines Corporation
- LexisNexis Risk Solutions by RELX
- LogRhythm, Inc.
- Mastercard Incorporated
- McAfee LLC
- Microsoft Corporation
- NEOM Company
- Nozomi Networks Inc.
- NVIDIA Corporation
- Okta, Inc.
- Oracle Corporation
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- RSA Security LLC
- Samsung Electronics Co., Ltd.
- SAP SE
- Securonix, Inc.
- SparkCognition, Inc.
- Tenable, Inc.
- Vectra AI, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 186 |
| Published | January 2026 |
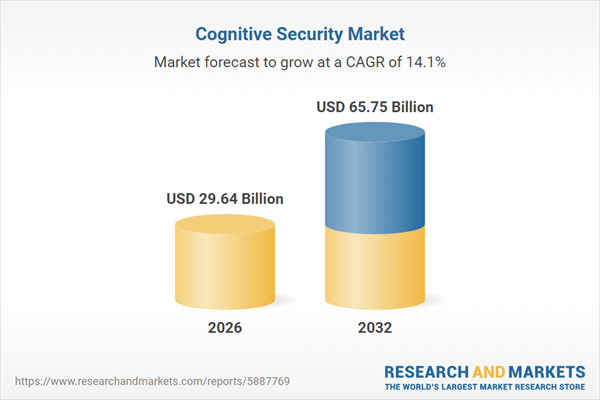
| Forecast Period | 2026 - 2032 |
| Estimated Market Value ( USD | $ 29.64 Billion |
| Forecasted Market Value ( USD | $ 65.75 Billion |
| Compound Annual Growth Rate | 14.0% |
| Regions Covered | Global |
| No. of Companies Mentioned | 40 |