Speak directly to the analyst to clarify any post sales queries you may have.
An essential executive introduction framing database encryption as a strategic enabler for secure digital transformation, regulatory alignment, and enterprise resilience
This executive summary introduces the strategic importance of database encryption for organizations operating in increasingly complex digital ecosystems. As data becomes more distributed across cloud, hybrid, and on-premises environments, the role of encryption shifts from a point control to an integral component of architecture and governance. In response, executives must assess encryption not merely as a defensive control but as a foundational enabler for secure digital transformation, privacy compliance, and resilient business continuity.The introduction also frames the interplay between technological innovation and regulatory pressures that drive encryption priorities. Cryptographic practices are evolving in step with changes in key management, hardware security modules, and software-based asymmetric and symmetric implementations. Decision-makers must therefore balance operational needs with cryptographic agility, ensuring that encryption strategies align with application requirements and enterprise risk tolerances. This context sets the stage for the deeper analysis that follows, which examines landscape shifts, policy impacts, segmentation insights, regional patterns, competitive positioning, and actionable recommendations to support informed executive decisions.
How converging trends in cloud migration, cryptographic agility, regulatory pressure, and evolving compute models are reshaping database encryption strategies
The landscape for database encryption is undergoing transformative shifts driven by converging forces: cloud-native adoption, service provider consolidation, rising regulatory expectations, and rapid advances in cryptography. Cloud migration is changing where sensitive data resides and who controls the underlying infrastructure, prompting organizations to rethink encryption boundaries and trust models. As a result, there is a pronounced move toward integrated key management solutions that operate seamlessly across public cloud, private cloud, and on-premises environments, ensuring consistent control regardless of workload location.Simultaneously, the proliferation of high-performance edge computing and containerized architectures requires more granular encryption models that protect data across ephemeral compute instances and persistent stores. Emerging cryptographic threats and the potential of quantum computing are also influencing roadmaps, with organizations planning for cryptographic agility to enable algorithm migration without disruptive rework. Finally, the increasing emphasis on data sovereignty and cross-border data flows is creating new demands for encryption controls tied to policy enforcement and auditability. These shifts collectively necessitate a strategic reinvestment in encryption architecture, operational tooling, and governance to maintain data confidentiality and support evolving business models.
Assessing the downstream effects of 2025 tariff measures on procurement, supply chains, and strategic vendor selection across the database encryption ecosystem
The cumulative effect of tariff actions in the United States in 2025 has fed through to procurement, supply chains, and strategic vendor relations in the database encryption ecosystem. Tariffs increased the landed cost of specialized hardware components, such as hardware security modules and secure processors, prompting many enterprises to reassess make-versus-buy decisions and to evaluate the total cost of ownership for on-premises versus cloud-based deployments. As vendors responded to higher component costs, some accelerated efforts to optimize firmware and software to reduce reliance on expensive imported parts, while others reconfigured supply chains to maintain competitive pricing.Beyond price impacts, tariffs influenced strategic partnerships and vendor selection behavior. Organizations prioritized vendor resilience and supply chain transparency, favoring providers with geographically diversified manufacturing, robust inventory management, and contractual safeguards. Procurement teams also increased scrutiny of long-term service agreements and warranties to mitigate potential disruption. In parallel, cloud-based key management services saw heightened interest as a way to shift hardware dependency to managed services, though this approach required careful analysis of control, compliance, and portability implications. Ultimately, the tariff environment served as a catalyst for more rigorous procurement governance and contingency planning within encryption programs.
Key segmentation insights revealing how encryption type, application scope, enterprise profile, deployment mode, key management, and end-user requirements drive divergent solution choices
Segmentation-driven analysis reveals distinct technical and commercial dynamics across encryption type, application, enterprise size, deployment mode, key management approach, and end-user verticals that shape solution requirements and adoption pathways. When considering encryption type, hardware encryption-comprising hardware security modules and secure processors-tends to be preferred where tamper resistance and isolated key storage are paramount, whereas software encryption implemented as asymmetric or symmetric algorithms provides flexibility and rapid iteration for application-layer protections. Each approach carries trade-offs in performance, manageability, and threat resistance that influence architectural choices.Application segmentation highlights different design imperatives for protecting data at rest versus data in transit. Data at rest protections include database encryption, disk-level safeguards, and file-level protections, each suited to particular persistence and access patterns; by contrast, data in transit protections such as IPsec, SSL/TLS, and VPN focus on securing communication channels and minimizing exposure during transfer. Enterprise size also matters: large enterprises often require integrated, centralized key management and policy orchestration across diverse business units, while small and medium enterprises-comprising medium and small enterprises-prioritize ease of deployment and cost-efficiency. Deployment modes vary from cloud to hybrid to on premises, with public and private cloud options introducing differing trust and control implications. Key management type bifurcates into cloud-based key management and on-premise key management, with cloud-based variants supporting bring-your-own-key and hold-your-own-key models that offer differing levels of customer control. Finally, end-user verticals such as banking, energy, government, healthcare, IT and telecom, manufacturing, and retail impose sector-specific compliance, performance, and availability requirements that drive tailored encryption architectures and managed-service considerations.
Regional patterns and geopolitical considerations that influence encryption deployment preferences, regulatory compliance approaches, and vendor selection dynamics globally
Regional dynamics play a pivotal role in shaping encryption adoption, technology preferences, and compliance priorities across the Americas, Europe Middle East & Africa, and Asia-Pacific. In the Americas, organizations balance innovation with privacy obligations and law enforcement access considerations, resulting in widespread adoption of cloud-based encryption services coupled with enterprise-grade key governance. This region emphasizes integration with advanced analytics and scalable key management to support large, distributed environments.Europe Middle East & Africa exhibits heightened sensitivity to data localization and stringent regulatory frameworks, compelling enterprises and public agencies to favor cryptographic architectures that enable demonstrable data residency and auditability. This has encouraged investment in private cloud and hybrid deployments that maintain strong contractual and technical controls. In Asia-Pacific, rapid digital transformation and diverse regulatory regimes have driven a hybrid landscape in which both cloud-native and on-premises encryption models coexist, and where regional supply chain considerations influence hardware procurement strategies. Across all regions, interoperability, compliance traceability, and vendor resilience remain cross-cutting priorities that determine enterprise choices and deployment sequencing.
Competitive landscape analysis highlighting how incumbents, hyperscalers, hardware manufacturers, and startups differentiate through integration, certifications, and operational maturity
Competitive dynamics within the encryption ecosystem are characterized by a mix of legacy incumbents, hyperscale cloud providers, specialized hardware manufacturers, and agile startups focusing on niche cryptographic capabilities. Vendors differentiate through a combination of product depth, integration capabilities, and service models. Legacy security vendors often compete on breadth of portfolio and enterprise-grade support, while hyperscale providers emphasize native integrations, scale, and global footprint. Hardware manufacturers of secure processors and hardware security modules compete on tamper resistance, throughput, and certification profiles, and they increasingly collaborate with software vendors to deliver turnkey solutions.Startups contribute innovation in algorithmic flexibility, developer-friendly APIs, and lightweight key management tools that reduce friction for application teams. Partnerships and channel strategies are central to market positioning, as vendors seek integration with cloud platforms, managed security service providers, and systems integrators to accelerate deployment and provide holistic services. Strategic priorities among leading players include obtaining rigorous certifications, expanding regional manufacturing and distribution, and investing in cryptographic agility features to address emerging threats and regulatory mandates. For buyers, vendor selection hinges on interoperability, roadmap transparency, and demonstrable operational maturity in secure key lifecycle management.
Actionable recommendations for senior leadership to operationalize cryptographic governance, ensure agility, and align encryption strategy with business resilience objectives
Industry leaders should adopt a proactive, phased approach to strengthen encryption posture while aligning with broader business objectives. Start by establishing cryptographic governance that codifies algorithm standards, key lifecycle policies, and incident response playbooks; this foundation ensures consistent decision making across IT, security, legal, and procurement functions and reduces the risk of ad hoc implementations. Next, prioritize cryptographic agility by designing systems to support algorithm replacement and key rotation without disruptive refactoring, enabling rapid response to evolving threat landscapes and regulatory changes.Operationally, leaders should evaluate a hybrid trust model that blends cloud-based key management for scalability with selective on-premise controls for highly sensitive assets, ensuring that portability and control objectives are reconciled. Strengthening supply chain resilience is essential: insist on supplier transparency, diversified sourcing for critical components, and contractual clauses that mitigate tariff and logistic risks. Finally, integrate encryption considerations into application development lifecycles through secure-by-design practices and developer-focused tooling that reduce implementation errors while accelerating secure deployment. These steps collectively help organizations convert encryption from a compliance checkbox into an operational enabler for secure innovation.
A transparent and repeatable research methodology combining primary interviews, secondary technical validation, segmentation mapping, and scenario analysis to ensure actionable insights
This research synthesizes qualitative and quantitative inputs using a transparent and repeatable methodology designed to surface practical insights for decision-makers. Primary research included structured interviews with security architects, procurement leaders, and operational technologists to capture firsthand perspectives on adoption drivers, implementation barriers, and vendor performance. Secondary research drew on technical whitepapers, industry standards, certification frameworks, and vendor documentation to validate technical characteristics and interoperability claims. Data triangulation combined these inputs to reconcile conflicting accounts and to surface robust themes across different stakeholder groups.The analysis also applied segmentation mapping to align technical capabilities with enterprise profiles, deployment modes, and sector-specific compliance requirements. Scenario analysis was used to simulate procurement and operational responses to supply chain disruptions and policy changes, ensuring that recommendations are resilient across plausible outcomes. Throughout, emphasis was placed on reproducibility and auditability: methodology notes document interview protocols, inclusion criteria for vendors, and the rationale for thematic prioritization so that readers can evaluate the evidence base underpinning conclusions and apply the findings to their unique operating environments.
Strategic conclusion stressing encryption as a foundational capability that aligns governance, architecture, and procurement to support secure innovation and regulatory compliance
In conclusion, database encryption is no longer a tactical control but a strategic capability that underpins secure digital transformation, regulatory compliance, and operational resilience. The interplay of cloud adoption, cryptographic innovation, regulatory pressures, and supply chain dynamics requires a holistic approach that integrates governance, technical architecture, and procurement discipline. Organizations that prioritize cryptographic agility, robust key management, and vendor resilience will be better positioned to protect sensitive data while enabling new business capabilities.Moving forward, leaders must view encryption as a cross-functional responsibility that touches development, operations, legal, and executive stakeholders. By aligning encryption strategies with broader risk management and business objectives, enterprises can reduce exposure, enhance trust with customers and partners, and create a foundation for secure innovation. The insights presented here are intended to guide pragmatic decision making and to support a phased transformation toward more resilient, auditable, and adaptable data protection practices.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
18. China Database Encryption Market
Companies Mentioned
- Broadcom Inc.
- Dell Technologies Inc.
- Imperva, Inc.
- International Business Machines Corporation
- McAfee LLC
- Micro Focus International plc
- Microsoft Corporation
- Opaque Systems, Inc.
- Open Text Corporation
- Oracle Corporation
- Paubox, Inc.
- Protegrity Corporation
- Proton AG
- Thales S.A.
- Vaultree Ltd.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 194 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
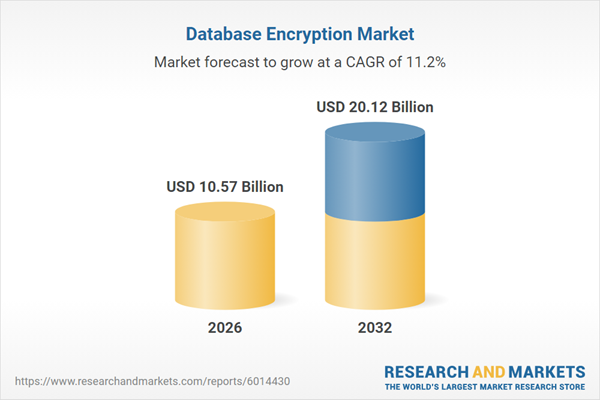
| Estimated Market Value ( USD | $ 10.57 Billion |
| Forecasted Market Value ( USD | $ 20.12 Billion |
| Compound Annual Growth Rate | 11.2% |
| Regions Covered | Global |
| No. of Companies Mentioned | 15 |