Speak directly to the analyst to clarify any post sales queries you may have.
An urgent strategic overview of how interconnected defense operations and expanding attack surfaces are redefining cybersecurity priorities for national security stakeholders
The accelerating pace of digitalization across defense organizations is reshaping how national security, operational readiness, and mission assurance are achieved. Military platforms, command-and-control systems, logistical networks, and defense industrial base suppliers are increasingly dependent on interconnected information systems, cloud services, and software-defined capabilities, which elevates the cyber risk profile at every layer of operations. As adversaries expand their capabilities and diversify attack vectors, stakeholders must reassess traditional assumptions about perimeter security and invest in adaptive strategies that protect data integrity, availability, and confidentiality.Recent operational demands have compelled defense leaders to pursue greater convergence of IT and operational technology, which creates complex integration challenges and widens the attack surface. Consequently, decision-makers are prioritizing solutions that provide continuous visibility, resilient architectures, and rapid incident response across hybrid environments. This introduction frames the report by emphasizing the strategic imperative for holistic cybersecurity governance, supply chain hardening, and cross-domain collaboration among services, contractors, and allied partners. By situating cyber risk within the broader context of force readiness and industrial resilience, readers can appreciate why investments in secure design, threat-informed defenses, and skilled workforce development are now mission-critical.
How technological innovation, adversary sophistication, and operational convergence are forcing a fundamental reorientation of defense cybersecurity strategy and procurement
The landscape of defense cybersecurity is undergoing transformative shifts driven by technological evolution, geopolitical tensions, and changing operational concepts. Artificial intelligence and machine learning are being embedded into defensive and offensive cyber tools, accelerating detection and response but also introducing new vectors of exploitation when models are trained or deployed without robust controls. Cloud-native operations and edge computing have enabled distributed mission capabilities, yet they demand new approaches to identity, encryption, and secure configuration management. Moreover, the proliferation of software-defined radios, unmanned systems, and integrated logistics platforms means adversaries can target not only enterprise networks but also critical mission systems and supply chains.Concurrently, regulatory frameworks and interoperability standards are evolving, pushing defense organizations to adopt composable architectures and DevSecOps practices to compress development cycles while preserving security. Zero Trust has moved from concept to operational necessity, as reliance on static perimeters proves untenable. Public-private collaboration is improving, with industry and government sharing threat intelligence more proactively, but trust and data classification challenges remain. These shifts require a reorientation of procurement, workforce development, and threat modeling, and they compel leaders to prioritize adaptive defenses that can scale across multi-domain operations and coalition environments.
Assessing how 2025 tariff adjustments have changed procurement dynamics and driven a strategic reconfiguration of trusted supplier networks and acquisition risk frameworks
Tariff policies implemented by the United States in 2025 have introduced additional complexity into defense supply chains and procurement planning, compounding long-standing concerns about dependency on foreign-sourced components and technologies. These tariffs have increased scrutiny of supplier baselines and lifecycle security practices, prompting defense acquisition authorities to intensify vetting of component provenance and to require demonstrable assurances about secure development and manufacturing processes. Procurement teams have responded by reassessing contract terms, adding security clauses related to provenance and traceability, and prioritizing vendors that can demonstrate domestic or trusted-source production pathways.The cumulative effect of these trade measures extends beyond immediate cost implications; they have reshaped supplier relationships and accelerated initiatives aimed at reducing single-source dependencies for critical hardware and software. Defense contractors and system integrators are diversifying vendor portfolios, investing in secure dual-sourcing strategies, and exploring onshoring or allied-region sourcing for sensitive components. These adaptations are generating longer procurement lead times in some cases, but they also enhance strategic resilience and reduce exposure to geopolitical supply shocks. In parallel, acquisition offices are revising risk frameworks to integrate trade policy impacts, ensuring that contracting decisions account for both cyber risk and supply chain stability over system lifecycles.
Detailed segmentation analysis revealing component, security type, threat, architecture, application, deployment, and end-user priorities that must guide tailored cybersecurity investments
A granular look across components, security types, threat vectors, architectures, applications, deployment models, and end-user segments reveals differentiated priorities that should inform capability roadmaps. When considering components, hardware elements such as data diodes, hardware security modules, and secure hardware systems carry heightened importance for high-assurance environments, while services ranging from consulting to integration and maintenance remain indispensable for operationalizing solutions; solutions focused on incident detection and response, security analytics, and vulnerability management form the backbone of defensive operations. Regarding security types, data security mechanisms including encryption and loss prevention are critical for protecting sensitive datasets, application and cloud security controls are essential for modern delivery models, and endpoint and network defenses such as endpoint detection and extended detection and response mechanisms, intrusion prevention systems, and next-generation firewalls are fundamental to layered defense.Examining threat types highlights the prominence of advanced persistent threats, distributed denial-of-service campaigns, insider risks, and diverse malware families-ransomware, rootkits, spyware, and trojans-each demanding tailored countermeasures that combine technical controls with behavioral analytics. In terms of security architecture, the move toward Zero Trust, Defense-in-Depth, DevSecOps practices, and Comply-to-Connect paradigms reflects a need for continuous verification, stronger supply chain controls, and secure-by-design development lifecycles. Application-focused domains such as critical infrastructure protection, identity and access management with emphasis on access control and authentication, risk and compliance management, and threat intelligence and response highlight where investments yield outsized operational benefits. Deployment models must be chosen with attention to cloud-based and on-premise trade-offs, balancing agility and sovereignty, and end-user considerations across Air Force, Army, defense contractors, government agencies, and Navy use cases show varied operational constraints, certification requirements, and integration priorities. Taken together, these segmentation insights indicate that tailored, interoperable solutions that respect domain-specific constraints and lifecycle needs will be most effective in delivering sustained defensive value.
Regionally differentiated threat, procurement, and partnership dynamics that determine how defense cybersecurity capabilities must be adapted for operational relevance
Regional dynamics influence threat profiles, procurement practices, and partnership models in distinct ways across the Americas, Europe, Middle East & Africa, and Asia-Pacific, shaping where and how organizations allocate defensive resources. In the Americas, a concentration of advanced cyber capabilities and a mature defense industrial base drive strong collaboration between government and industry on intelligence sharing, secure supply chain initiatives, and standards alignment, which supports rapid operationalization of new security paradigms. By contrast, Europe, Middle East & Africa display heterogeneity in regulatory approaches and interoperability priorities, with many states focusing on harmonizing cross-border defenses, elevating sovereign capabilities, and incentivizing resilient domestic production to meet both national security and industrial policy goals.Asia-Pacific presents a highly dynamic environment where rapid technology adoption, coupled with rising regional tensions, leads to accelerated modernization of military communications and networked platforms, prompting investments in robust secure architectures and enhanced identity and access controls. Across all regions, geopolitical considerations and allied interoperability imperatives influence procurement timelines and certification demands, and these regional distinctions mean that solution providers must adapt offerings to local regulatory regimes, integration ecosystems, and mission-specific requirements to achieve operational relevance and long-term adoption.
How top defense cybersecurity companies are differentiating through integration, trusted supply chains, explainable analytics, and end-to-end lifecycle offerings
Leading companies in the defense cybersecurity ecosystem are converging around platforms that combine advanced analytics, rapid detection and response, and hardened hardware for high-assurance environments. Market leaders differentiate through demonstrable integration capabilities with legacy and mission systems, strong track records of secure engineering practices, and investments in explainable machine learning to improve operational trust. Strategic partnerships between technology vendors, integrators, and specialized service providers are common, enabling end-to-end delivery models that include consulting, systems integration, managed detection, and sustained maintenance support.Companies that excel are those that can navigate stringent certification regimes, prove supply chain integrity, and offer modular solutions that accommodate both cloud-native and on-premise deployments. They also prioritize transparent threat intelligence sharing and participate in industry-government collaborations to improve collective defense. Competitive advantage stems from the ability to balance innovation with rigorous lifecycle security, to demonstrate compliance with evolving standards, and to provide clear pathways for customers to achieve mission assurance while controlling total cost of ownership over program lifecycles.
Practical strategic imperatives and capability investments that industry leaders must implement to accelerate secure modernization and strengthen operational resilience
Industry leaders should pursue a coordinated strategy that aligns procurement, engineering, and operational teams to accelerate secure modernization while managing risk. First, prioritize adoption of Zero Trust principles across networks and mission systems, paired with strong identity and access management practices that enforce least privilege and continuous verification. Second, invest in resilient supply chain strategies that include provenance controls, secure manufacturing attestations, and selective onshoring or trusted allied sourcing for critical components; these measures will reduce geopolitical exposure and improve lifecycle assurance. Third, accelerate adoption of DevSecOps practices to embed security throughout the development pipeline, leveraging automated testing, threat modeling, and secure configuration baselines to reduce vulnerabilities before deployment.Additionally, enhance incident detection and response capabilities by integrating behavioral analytics, extended detection and response tools, and tailored playbooks that reflect operational realities of different service domains. Strengthen workforce capability through targeted upskilling programs that blend cyber operations, cloud security, and secure systems engineering, and retain talent by offering clear career pathways tied to mission impact. Finally, foster formalized public-private information sharing arrangements that respect classification boundaries while enabling rapid exchange of actionable intelligence; this collective approach will improve readiness and reduce mean time to remediate across the ecosystem.
A clear explanation of the mixed-method research approach combining expert interviews, doctrinal analysis, and cross-sectional mapping to produce actionable defense cybersecurity insights
This research synthesizes qualitative and quantitative methods to deliver a robust, defensible analysis of defense cybersecurity dynamics. Primary research involved structured interviews and workshops with defense cybersecurity practitioners, procurement officials, system integrators, and subject-matter experts to capture operational constraints, procurement behaviors, and technology adoption drivers. Secondary sources included publicly available doctrinal publications, government guidance on acquisition and supply chain security, vendor technical documentation, and open-source reporting on notable cyber incidents to contextualize threat vectors and defensive responses.Analytical approaches combined thematic coding of qualitative inputs with cross-sectional analysis of capability attributes to identify common patterns and divergent requirements across end users and regions. Security architecture and component evaluations were mapped against practical deployment scenarios to highlight where trade-offs emerge between agility, sovereignty, and assurance. Throughout the methodology, attention was paid to corroborating claims across multiple sources and to noting areas where evidence indicates emerging trends rather than established practice. These methods ensure the findings are grounded in current operational realities and provide actionable guidance for decision-makers focused on enhancing defense cyber posture.
Concluding synthesis that underscores why integrating cybersecurity into operational design, procurement, and workforce development is essential to maintaining mission readiness
In an era where mission success increasingly depends on the integrity and resilience of cyber systems, defense organizations must treat cybersecurity as an integral element of operational design rather than an afterthought. The converging forces of technological innovation, evolving threat capabilities, and supply chain complexities demand a strategic posture that integrates secure architecture principles, rigorous supplier vetting, and continuous capability development. Leaders who adopt a holistic approach-aligning procurement strategies, engineering practices, and operational procedures-will reduce systemic risk and enhance readiness across contested environments.By embracing adaptive defenses, investing in workforce excellence, and fostering trusted partnerships that prioritize secure development and transparent information sharing, organizations can better anticipate adversary moves and contain incidents with limited operational disruption. The conclusion underscores that sustainable advantage in defense cyberspace is achieved through disciplined execution of architecture, policy, and people strategies, supported by pragmatic procurement and lifecycle governance. In short, cybersecurity must be woven into the fabric of defense capability development to ensure resilient, mission-capable forces.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
19. China Defense Cybersecurity Market
Companies Mentioned
The key companies profiled in this Defense Cybersecurity market report include:- Accenture PLC
- Airbus SE
- Akamai Technologies, Inc.
- Amazon Web Services, Inc.
- Amentum Services, Inc.
- AO Kaspersky Lab
- ASGN Incorporated
- AT&T Inc.
- BAE Systems PLC
- Bharat Electronics Limited
- Binary Defense
- Booz Allen Hamilton Holding Corporation
- CACI International Inc.
- CAE Inc.
- Celerium Inc.
- Cisco Systems, Inc.
- CounterCraft S.L.
- CrowdStrike, Inc.
- Cybastion
- Elbit Systems Ltd.
- Fortinet, Inc.
- Futurex LP
- General Dynamics Corporation
- Huntington Ingalls Industries
- International Business Machines Corporation
- IronNet, Inc.
- Israel Aerospace Industries Ltd.
- L3Harris Technologies Inc.
- Leidos Holdings, Inc.
- Leonardo S.p.A.
- Lockheed Martin Corporation
- ManTech International Corporation
- Microsoft Corporation
- Mission Secure Inc.
- Northrop Grumman Corporation
- Okta, Inc.
- Oracle Corporation
- Orange S.A.
- Owl Cyber Defense Solutions, LLC
- Parsons Corporation
- Peraton Corp.
- PRODAFT
- Rockwell Automation Inc.
- RTX Corporation
- Saab AB
- Science Applications International Corporation
- Stefanini Group
- Tata Consultancy Services Limited
- Thales Group
- Trellix
- Wipro Limited
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 188 |
| Published | January 2026 |
| Forecast Period | 2025 - 2030 |
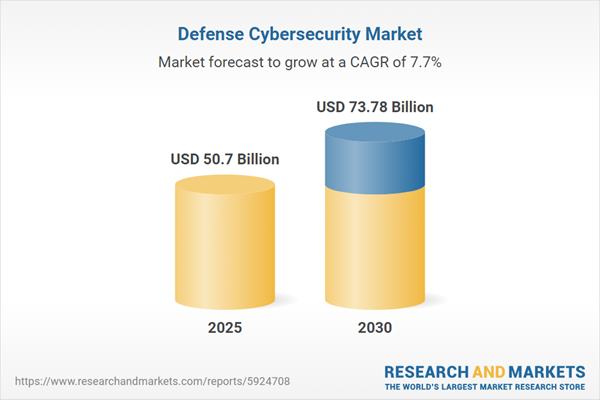
| Estimated Market Value ( USD | $ 50.7 Billion |
| Forecasted Market Value ( USD | $ 73.78 Billion |
| Compound Annual Growth Rate | 7.7% |
| Regions Covered | Global |
| No. of Companies Mentioned | 52 |