Speak directly to the analyst to clarify any post sales queries you may have.
A strategic orientation on how converging technological, operational, and regulatory pressures are redefining priorities for enterprise network security investments and architectures
Network security has evolved from a perimeter-focused discipline into a foundational enabler of business continuity, innovation, and trust. Over the past several years, the proliferation of remote work, cloud-native architectures, and API-driven interactions has reframed traditional risk models, requiring executives to balance agility with rigorous control frameworks. As attack surfaces expand, decision-makers must integrate threat prevention, detection, and response capabilities into a coherent enterprise strategy that supports digital initiatives rather than impedes them.In this context, procurement and architecture teams confront a complex vendor landscape that spans point solutions, integrated platforms, and managed service providers. Technology choices are increasingly influenced by interoperability requirements, identity-centric controls, and the ability to operationalize security telemetry into meaningful workflows. Consequently, leaders are prioritizing solutions that deliver demonstrable improvements in time to detect and time to respond, while preserving developer velocity and business flexibility.
Moreover, regulatory expectations and third-party risk considerations are forcing organizations to adopt more transparent and auditable controls. This confluence of operational, technical, and compliance drivers underscores the necessity of a strategic approach to network security that aligns investments with business outcomes. The subsequent sections explore the transformative shifts in the landscape, the specific implications of recent tariff measures, segmentation-driven insights, regional dynamics, vendor positioning, and recommended actions for leaders seeking to strengthen their security posture.
How simultaneous advances in cloud architectures, attacker behavior, and regulatory expectations are forcing a fundamental redesign of network security architectures and operations
The security landscape is undergoing transformative shifts driven by three broad vectors: technology evolution, attacker sophistication, and governance pressures. First, technological advancements such as cloud-native deployments, microsegmentation, zero trust models, and the proliferation of encrypted traffic are changing what defenses must protect and how they are implemented. These developments necessitate solutions that can operate across hybrid environments, ingest diverse telemetry sources, and provide contextualized, identity-aware controls that tie policy to user and workload attributes.Second, adversaries are scaling their operations through automation, supply chain compromise, and targeted exploitation of misconfigurations in complex environments. As a result, organizations must invest in capabilities that emphasize proactive threat hunting, behavior-based detection, and rapid containment. Behavior-based anti-malware approaches are gaining traction alongside signature-based techniques because they detect anomalies that signature libraries alone cannot surface. In parallel, intrusion detection and prevention systems are being retooled to operate in concert with identity and access management controls and security analytics to accelerate triage and response.
Third, governance and compliance frameworks are mandating higher levels of visibility and accountability. Security information and event management disciplines are evolving to incorporate advanced log management and analytics, enabling continuous compliance and forensic readiness. Unified threat management platforms are being reconsidered in favor of modular ecosystems that allow organizations to adopt best-of-breed components, including VPN solutions that support both remote access and site-to-site connectivity. In combination, these shifts require security leaders to adopt an architecture-first mindset that anticipates change, prioritizes interoperability, and embeds security controls into development and operations lifecycles.
The enduring effects of 2025 tariff measures on supply chain resilience and procurement decisions that are reshaping vendor selection and deployment strategies across security stacks
Policy actions affecting tariffs have a cascading influence on procurement strategies, supplier selection, and the total cost of ownership that underpins security programs. The cumulative impact of tariff measures implemented in 2025 has prompted organizations to reassess supplier dependency, diversify sourcing, and re-evaluate the economics of hardware-centric versus software-centric security solutions. Consequently, procurement teams have grown more conservative with single-vendor hardware rollouts and more open to cloud-delivered models that mitigate physical supply chain constraints.In practice, tariff-induced changes have led to a greater emphasis on modularity and portability. Firms are accelerating adoption of software-based firewalls, virtual appliances, and cloud-native security services that can be provisioned across geographies without being tied to specific hardware shipments. This shift also affects how organizations approach vendor relationships, with an increased focus on contractual flexibility, regional distribution capabilities, and local support ecosystems. Furthermore, tariffs have magnified the importance of lifecycle management and patching strategies, since replacement cycles for proprietary appliances may lengthen and spare parts may become less accessible.
As a transitional outcome, many security teams are redefining capital expenditure plans to favor operating expenditure models where feasible, while ensuring controls remain robust. Identity and access management solutions, including multifactor authentication and privileged access management, have become prioritized investments because they reduce dependence on edge hardware. At the same time, organizations must remain vigilant about the potential trade-offs in latency, control, and data residency that may accompany accelerated cloud migration. Overall, tariff-related dynamics have catalyzed a strategic pivot toward resilience through source diversity, software portability, and contractual agility.
Segment-specific insights across components, deployment modes, organizational scale, and vertical requirements that reveal differential procurement drivers and solution design priorities
A granular segmentation lens reveals differentiated adoption drivers and technical requirements across components, deployment modes, organization size, and industry verticals. When assessed by component, the landscape includes anti-malware, firewall, identity and access management, intrusion detection and prevention, security information and event management, unified threat management, and virtual private network capabilities. Within anti-malware, behavior-based approaches complement signature-based techniques to detect novel threats, and organizations often deploy a combination of the two to balance precision with coverage. Identity and access management practices emphasize multi-factor authentication, privileged access management, and single sign-on to reduce credential-based risk and operational friction. Security information and event management systems increasingly incorporate both log management and security analytics to enable correlation, anomaly detection, and forensic investigation. Virtual private network solutions are evaluated for both remote access and site-to-site connectivity, with different configuration expectations depending on the user population and architecture.Deployment mode introduces another axis of differentiation. Cloud-oriented deployments span IaaS, PaaS, and SaaS models and are favored for rapid scalability, centralized management, and reduced hardware dependencies. Conversely, on-premise solutions-available as open source or proprietary offerings-remain relevant for organizations with strict data residency, latency, or regulatory requirements. Organizational scale shapes procurement behavior: large enterprises typically require sophisticated integration capabilities, centralized policy orchestration, and broad vendor ecosystems to support complex heterogeneous environments. Small and medium enterprises, by contrast, prioritize turnkey solutions, lower operational overhead, and pricing predictability.
Industry verticals impose unique constraints and priorities. Banking, finance, and insurance demand rigorous controls across banking operations, capital markets, and insurance workflows and place a premium on auditability and resistance to fraud. Government entities focus on sovereignty, secure inter-agency connectivity, and long-term vendor stability. Healthcare organizations balance patient privacy, device security, and clinical continuity. IT and telecom providers prioritize high-throughput, low-latency protections and multi-tenant isolation, while retail environments seek to secure point-of-sale systems and omnichannel commerce pathways. These segmentation insights should inform product roadmaps, channel strategies, and service offerings to ensure alignment with customer procurement criteria and technical prerequisites.
How geographic nuances in regulation, talent, and infrastructure are shaping adoption patterns and procurement preferences across the Americas, Europe Middle East & Africa, and Asia-Pacific
Regional dynamics exert a strong influence on how network security solutions are procured, deployed, and supported. In the Americas, innovation hubs and a broad ecosystem of managed security providers foster rapid adoption of cloud-delivered services and advanced analytics capabilities. Organizations in this region tend to prioritize rapid operationalization, integration with threat intelligence feeds, and vendor partnerships that offer extensive service-level commitments. Conversely, Europe, Middle East & Africa presents a more heterogeneous regulatory and political landscape, where data protection frameworks and national security considerations shape preferences for on-premise deployments, local support, and clear data residency guarantees. In many jurisdictions across this region, procurement cycles are influenced by public sector accreditation requirements and the need for vendor transparency in supply chains.The Asia-Pacific region is characterized by diverse maturity levels and a significant emphasis on scale and performance. Large technology providers and service operators in the region demand solutions that can handle high transaction volumes and complex multi-tenant architectures. Additionally, talent availability and local engineering capabilities influence adoption patterns, with some markets accelerating cloud-first strategies while others maintain hybrid postures due to regulatory or latency constraints. Across all regions, interoperability, standards compliance, and the availability of skilled operational staff are recurring considerations that shape implementation timelines and total cost of operations.
Transitionally, cross-border collaboration and threat-sharing arrangements are increasing, which amplifies the need for standardized telemetry formats and interoperable APIs. As a result, vendors and customers alike are prioritizing regional partnerships, local delivery models, and documentation that supports multiple regulatory regimes. These geographic nuances should guide go-to-market segmentation, channel investments, and localization strategies for solution providers.
Insights into vendor differentiation and partnership dynamics that reveal how integration capabilities, managed services, and specialized innovation are redefining competitive advantage
Competitive dynamics in the network security ecosystem are evolving as incumbents adapt to cloud economics and emerging challengers emphasize specialization and integration. Vendors that combine deep security engineering with robust integration frameworks are differentiating through platform orchestration, threat intelligence partnerships, and managed detection and response capabilities. At the same time, specialist firms that focus on areas such as behavior-based malware detection, advanced security analytics, or identity and access management are gaining traction by delivering high-fidelity signals and streamlined operational workflows.Partnership ecosystems are an increasingly important axis of differentiation. Successful vendors demonstrate the ability to interoperate with cloud providers, orchestration tools, endpoint agents, and SIEM platforms that incorporate log management and analytics. They also invest in developer-friendly interfaces and APIs that enable rapid automation, enabling customers to codify security controls into deployment pipelines. Furthermore, channel and managed services partners play a pivotal role in delivering scale, especially for organizations that lack deep in-house security operations expertise.
Consolidation pressures are prompting strategic acquisitions and alliances that aim to unify prevention, detection, and response capabilities. However, integration risk remains non-trivial; therefore, buyers evaluate roadmaps, integration maturity, and support models as closely as they assess functional capabilities. Pricing models are also evolving, with a clear shift toward subscription-based offerings that bundle analytics, threat intelligence, and orchestration while reducing upfront capital commitments. Ultimately, the firms that succeed will be those that balance technical excellence, ease of operations, and credible service delivery across diverse deployment environments.
Prioritized and pragmatic actions for executives to strengthen resilience, optimize procurement, and align security investments with organizational risk and operational goals
Leaders should adopt a pragmatic, phased approach to strengthen their network security posture while aligning investments with business priorities. Initially, organizations should prioritize identity-centric controls, including multi-factor authentication, privileged access management, and single sign-on, because these measures materially reduce credential-based risk and can be implemented with limited hardware dependence. Concurrently, investing in behavior-based detection capabilities alongside signature-based defenses enhances the ability to catch novel threats and reduce dwell time.Next, emphasize interoperability and orchestration. Organizations should select solutions that offer robust APIs, support for log management and security analytics, and seamless integration with existing orchestration and ticketing systems. This strategy accelerates incident response and reduces manual toil in security operations. Where feasible, adopt cloud-delivered security services across IaaS, PaaS, and SaaS environments to improve scalability and diminish supply chain exposure tied to proprietary hardware. For environments that must remain on-premise due to regulatory or latency constraints, favor solutions that provide both open source and proprietary pathways to maintain flexibility.
Finally, implement governance measures that tie security objectives to measurable operational outcomes. Establish a prioritized roadmap that aligns tooling adoption with risk reduction goals, invest in staff training to close operational gaps, and cultivate vendor relationships that include clear escalation, local support, and contractual flexibility. These actions, taken together, will enable organizations to balance resilience, cost efficiency, and adaptability as threats and requirements continue to evolve.
A transparent mixed-methods research design combining practitioner interviews, vendor briefings, and secondary analysis with rigorous triangulation and quality assurance
This research employed a mixed-methods approach combining primary qualitative inquiry, structured secondary analysis, and rigorous data triangulation to ensure the validity and reliability of findings. Primary research included structured interviews with security practitioners, procurement leaders, and technology executives across enterprise and public sector organizations, which supplied contextual insights into procurement drivers, integration challenges, and operational trade-offs. These conversations were augmented by vendor briefings and technical demonstrations to assess solution architectures, integration capabilities, and support models.Secondary sources involved a comprehensive review of public filings, regulatory guidance, technical white papers, and industry best practice frameworks to corroborate emergent themes and to situate findings within documented standards. The research team applied a consistent segmentation logic across components, deployment modes, organization size, and industry verticals to ensure comparability. Components analyzed included anti-malware with behavior-based and signature-based modalities, firewall, identity and access management with multi-factor authentication and privileged access management, intrusion detection and prevention, security information and event management with log management and security analytics, unified threat management, and virtual private network solutions covering remote access and site-to-site configurations.
Quality assurance measures included cross-validation of findings with independent experts, consistency checks across data sources, and an explicit recognition of limitations where observable trends varied by region or vertical. Ethical considerations and confidentiality commitments guided primary engagements, and the methodology favored transparency in assumptions to enable readers to assess applicability to their own contexts.
Synthesis of strategic priorities and risk trade-offs to guide executives in aligning security investments with operational resilience and business enablement
The strategic imperative for network security is clear: protect the expanding digital surface while enabling the business capabilities that drive growth and differentiation. Across components, deployment models, and regions, the dominant themes converge on portability, interoperability, identity-centric controls, and analytics-driven detection. Organizations that foreground identity and access management, embrace behavior-based detection techniques, and prioritize integration between telemetry sources and response orchestration will be better positioned to reduce dwell times and operational overhead.Moreover, geopolitical and procurement pressures, including tariff-related supply dynamics, have accelerated shifts toward software-centric, cloud-delivered security models. These changes require a reassessment of vendor relationships, contractual flexibility, and lifecycle management practices. At the same time, regional and vertical nuances remain significant; regulatory requirements, latency constraints, and local talent availability will continue to shape implementation choices.
In closing, decision-makers should treat security as a strategic enabler rather than a cost center. By aligning security investments with measurable outcomes, investing in people and process alongside technology, and choosing partners that demonstrate integration maturity and operational discipline, organizations can build resilient, adaptable defenses that support their broader strategic objectives.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
16. China Network Security Software Market
Companies Mentioned
The key companies profiled in this Network Security Software market report include:- A10 Networks, Inc.
- Barracuda Networks, Inc.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- CyberArk Software Ltd.
- F5, Inc.
- FireEye, Inc.
- Fortinet, Inc.
- IBM Corporation
- Imperva, Inc.
- Juniper Networks, Inc.
- Kaspersky Lab ZAO
- LogRhythm, Inc.
- McAfee, LLC by Advent International
- Palo Alto Networks, Inc.
- Qualys, Inc.
- Rapid7, Inc.
- SolarWinds Inc.
- Sophos Group plc
- Tenable, Inc.
- WatchGuard Technologies, Inc.
- Zscaler, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 195 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
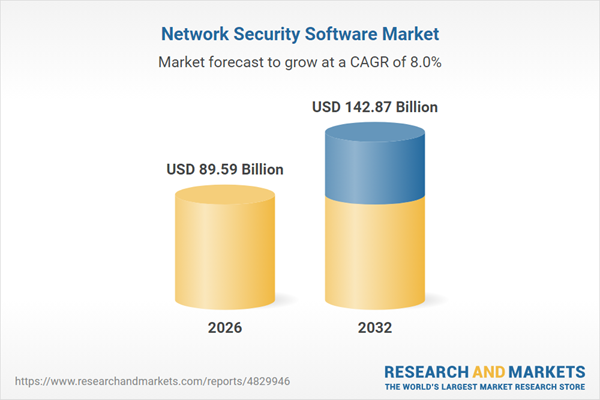
| Estimated Market Value ( USD | $ 89.59 Billion |
| Forecasted Market Value ( USD | $ 142.87 Billion |
| Compound Annual Growth Rate | 8.0% |
| Regions Covered | Global |
| No. of Companies Mentioned | 25 |