Speak directly to the analyst to clarify any post sales queries you may have.
Setting the Stage for NextGeneration Security in Online Gaming Environments with Rising Complexity Accelerating Threat Vectors and Expanding Player Expectations
The online gaming industry has evolved into a vibrant digital ecosystem characterized by rapid innovation and a constantly shifting threat landscape. Rising user engagement, propelled by next-generation consoles, mobile devices, and cloud gaming platforms, has expanded the attack surface and intensified the need for robust security frameworks. As interactive experiences grow in complexity, developers and operators must address a variety of security challenges ranging from real-time fraud prevention to protecting the integrity of large-scale multiplayer environments. Furthermore, the proliferation of cross-platform play and interconnected social features demands a more integrated approach to safeguarding both infrastructure and user data.Amid heightened regulatory focus on data privacy and digital transactions, stakeholders must align technical defenses with compliance requirements while maintaining seamless user experiences. This imperative drives a convergence of traditional cybersecurity measures with specialized gaming security solutions. Insights derived from qualitative interviews with industry leaders underscore the importance of adaptive security postures that evolve alongside emerging attack vectors. By combining proactive threat intelligence with scalable protection services, online gaming platforms can not only mitigate risk but also foster trust and loyalty among players. Consequently, this introduction sets the stage for an in-depth exploration of transformative shifts, tariff impacts, segmentation insights, and actionable recommendations to ensure the resilience and longevity of online gaming ecosystems.
Examining Transformative Shifts Reshaping Online Gaming Security Through Technological Advances Artificial Intelligence Integration and Emerging Regulatory Imperatives
The online gaming landscape has experienced transformative shifts driven by technological innovation, escalating sophistication of cyber threats, and evolving regulatory frameworks. Advancements in cloud computing have enabled elastic scaling of gaming environments, but they have also introduced novel vulnerabilities related to misconfigurations and inter-tenant risks. Meanwhile, the integration of blockchain technologies for in-game asset ownership and decentralized gaming economies presents new security opportunities alongside unique challenges in ensuring transaction integrity and preventing unauthorized token manipulation.Moreover, the advent of cross-platform play has blurred traditional infrastructure boundaries, compelling security architects to adopt unified identity and access management solutions that can seamlessly authenticate users across consoles, mobile devices, and personal computers. Simultaneously, the emergence of real-time analytics powered by artificial intelligence has driven a shift from reactive threat detection toward predictive security models capable of identifying anomalous behaviors before they manifest as major incidents. On the compliance front, tightened data protection regulations in key jurisdictions have prompted operators to reevaluate data encryption practices and privacy controls, ensuring robust safeguards without compromising latency-sensitive gaming experiences. Through these converging forces, the industry is redefining its security posture, transitioning from isolated defenses to cohesive, intelligence-driven ecosystems that can adapt to the rapid pace of change.
Unraveling the Cumulative Impact of United States Tariffs on Online Gaming Security Supply Chains and Cost Structures in 2025
The introduction of new United States tariff measures in 2025 has triggered a series of implications for online gaming security supply chains and cost structures. Hardware components for data centers, gaming consoles, and network edge devices have experienced adjusted import duties, driving up procurement costs for critical infrastructure. These increases have necessitated strategic sourcing decisions and accelerated the pursuit of domestic manufacturing partnerships to maintain budgetary stability and supply chain resilience.Beyond hardware, the broader ecosystem of security solutions-ranging from application hardening tools to advanced encryption modules-has felt the ripple effects of increased duties on imported software components and specialized security appliances. Consequently, service providers have reevaluated their pricing models, passing a portion of the cost burden onto end users while simultaneously exploring cost-optimization strategies such as containerization and virtualization to maximize resource utilization. Furthermore, this tariff environment has underscored the importance of diversified vendor portfolios, prompting security teams to integrate open-source technologies alongside proprietary offerings and to localize certain development activities to mitigate exposure to international trade fluctuations.
In addition, evolving tariff dynamics have intensified collaboration between legal, procurement, and security leadership, fostering a more holistic approach to financial planning. By proactively addressing these fiscal pressures, organizations can maintain robust security postures without compromising on innovation or user satisfaction.
Uncovering Key Segmentation Insights by Component Risk Type Platform Deployment Mode and End User to Guide Targeted Security Strategies
A nuanced understanding of market segmentation illuminates where security investments can drive maximum impact. When analyzed by component, the market divides into comprehensive services and specialized solutions. Service offerings encompass consulting and implementation engagements that tailor defenses to unique architectures, managed services that continuously monitor and respond to incidents, and support and maintenance programs that ensure long-term reliability. On the solutions side, protections span application security measures that fortify code integrity, data encryption capabilities that safeguard sensitive player information, DDoS protection systems that preserve uptime during peak events, identity and access management frameworks-complete with multi-factor authentication, privileged access management, and single sign-on features-and risk and fraud management platforms that detect and deter malicious activities.Examining risk types reveals key priorities for mitigation efforts, including the prevention of data breaches, the deterrence of doxing and swatting incidents, defenses against identity theft and account takeover scenarios, countermeasures for malware and virus outbreaks, and anti-phishing strategies to protect user credentials. Platform-based analysis highlights the distinct security profiles of console gaming, mobile environments-spanning Android and iOS devices-and personal computer ecosystems that encompass Linux, macOS, and Windows operating systems. Deployment mode considerations differentiate cloud-native architectures from on-premises installations, each presenting unique controls for network segmentation and resource isolation. Finally, from an end-user perspective, developers require secure development lifecycles and API hardening, while gamers-both casual players and competitive professionals-demand frictionless authentication and real-time protection to maintain seamless gameplay experiences. By weaving these dimensions together, stakeholders can craft targeted security roadmaps that align with specific operational and user requirements.
Illuminating Critical Regional Insights Spanning Americas Europe Middle East Africa and Asia Pacific to Navigate Diverse Security Requirements
Regional dynamics exert a significant influence on the design and deployment of online gaming security measures. In the Americas, security strategies must address a mature market landscape characterized by stringent data privacy regulations and robust enforcement mechanisms. Operators in this region prioritize comprehensive encryption standards, advanced threat intelligence sharing, and rapid incident response capabilities to safeguard large user communities and complex multiplayer environments.Transitioning to Europe, Middle East & Africa, organizations navigate a diverse regulatory tapestry that includes the General Data Protection Regulation alongside emerging data sovereignty laws. Here, security frameworks emphasize granular access controls, privacy-by-design principles, and rigorous third-party risk assessments. Collaborative initiatives between public and private sectors have accelerated threat information exchanges, fostering a collective defense posture against cross-border cyber threats.
In the Asia-Pacific region, the convergence of high-growth mobile gaming markets and pioneering cloud adoption drives a focus on scalable, latency-optimized security solutions. Operators place heightened emphasis on automated compliance, real-time behavioral analytics, and localized threat intelligence tailored to regional attacker methodologies. By understanding these varied regional requirements, stakeholders can deploy adaptive controls that align with local market conditions while maintaining cohesive global security governance.
Profiling Leading Companies Driving Innovation in Online Gaming Security with Advanced Solutions and Comprehensive Service Offerings
Leading companies within the online gaming security space are distinguished by their ability to integrate comprehensive service offerings with cutting-edge technological platforms. Several prominent vendors deliver end-to-end managed detection and response capabilities, combining continuous network monitoring, threat hunting, and incident remediation within a unified framework. These providers often augment their offerings with specialized advisory services to guide secure architecture design, DevSecOps integration, and compliance alignment across multiple jurisdictions.Simultaneously, innovative solution providers excel at embedding artificial intelligence and machine learning into core security components. Their platforms leverage predictive analytics to identify anomalous behavior patterns, enabling early intervention before attacks escalate. In parallel, established cybersecurity firms have expanded their portfolios through targeted acquisitions, incorporating application security suites, real-time risk scoring engines, and advanced DDoS mitigation services. Collaboration between niche specialists and major cloud service providers is further enhancing the availability of integrated security controls at scale, allowing gaming operators to deploy protective measures closer to the edge.
These leading companies also prioritize developer enablement, offering secure software development kits and threat modeling tools that streamline the secure development lifecycle. By championing interoperability and open standards, they ensure that security solutions can evolve alongside rapidly changing gaming technologies and player demands.
Formulating Actionable Recommendations for Industry Leaders to Enhance Resilience Mitigate Risks and Optimize Security Investments in Gaming Platforms
Industry leaders must adopt a multi-faceted approach to fortifying gaming ecosystems against increasingly sophisticated threats. First, embedding security into the development process by adopting secure coding practices, automated vulnerability scanning, and continuous integration pipelines will minimize latent application flaws. In parallel, incorporating real-time behavioral analytics and machine learning algorithms within live environments can preemptively detect unusual activity, enabling security teams to neutralize incidents before they propagate.Moreover, fostering collaboration across organizational silos-spanning legal, compliance, procurement, and operations-ensures that financial and regulatory constraints are balanced with security imperatives. Establishing clear governance frameworks and accountability structures will streamline decision-making and accelerate response times during incidents. Additionally, diversifying vendor relationships and exploring open-source alternatives can mitigate the risk of supply chain disruptions and tariff-driven cost increases.
Investing in player-centric security experiences through adaptive authentication, transparent privacy controls, and responsive support channels will reinforce user trust and loyalty. Finally, continuous learning programs, including simulation exercises and threat intelligence workshops, will equip teams with the skills needed to navigate emerging attack methods. By operationalizing these recommendations, decision-makers can achieve a resilient security posture that scales with evolving technological and regulatory landscapes.
Detailing the Comprehensive Research Methodology Underpinning the Analysis Incorporating Qualitative Interviews Data Triangulation and Rigorous Validation Processes
This research is grounded in a robust methodology that combines qualitative insights with rigorous data triangulation. Primary information was gathered through in-depth interviews with cybersecurity experts, game developers, and executive decision-makers, providing firsthand perspectives on emerging threats and strategic priorities. To validate these findings, the study incorporates secondary data from reputable industry white papers, regulatory publications, and peer-reviewed sources, ensuring that conclusions reflect the latest advancements and best practices.Quantitative elements were analyzed using structured frameworks to cross-reference threat incidence rates, adoption trends for security solutions, and regional regulatory developments. Statistical validation techniques were applied to assess data consistency and reliability, while scenario modeling explored potential outcomes under varying tariff and technology adoption scenarios. Furthermore, a peer review process engaged external subject matter specialists to critique methodology design and interpretive frameworks, bolstering the study’s overall integrity.
By integrating these qualitative and quantitative approaches, the research provides a comprehensive, evidence-based understanding of the online gaming security landscape. This structured methodology ensures that stakeholders receive actionable insights underpinned by transparent validation and in-depth expert analysis.
Concluding Reflections on the Evolving Online Gaming Security Landscape Emphasizing Strategic Imperatives and Future Preparedness
As the online gaming industry continues to expand, security challenges will evolve in both complexity and scale. The convergence of emerging technologies-such as cloud gaming, decentralized architectures, and immersive virtual environments-will necessitate adaptive security frameworks capable of rapid iteration. Simultaneously, regulatory landscapes will become increasingly intricate, requiring operators to balance innovation with compliance across global markets.The cumulative impact of geopolitical developments and tariff adjustments underscores the need for diversified supply chains and agile procurement strategies. In parallel, the integration of artificial intelligence into threat detection and response processes will reshape how security teams anticipate and neutralize risks. Collaboration among industry stakeholders, including game developers, security providers, and regulatory bodies, will drive the development of unified standards and best practices.
Ultimately, organizations that proactively embed security into every layer of their gaming ecosystems-from code development through user engagement-will secure competitive advantages and foster sustainable growth. By remaining vigilant, investing in emerging defenses, and cultivating cross-functional partnerships, the industry can navigate the shifting landscape and deliver trustworthy, resilient gaming experiences for players worldwide.
Market Segmentation & Coverage
This research report forecasts the revenues and analyzes trends in each of the following sub-segmentations:- Component
- Services
- Consulting & Implementation
- Managed Services
- Support & Maintenance
- Solutions
- Application Security
- Data Encryption
- DDoS Protection
- Identity & Access Management
- Multi-Factor Authentication
- Privileged Access Management
- Single Sign-On
- Risk & Fraud Management
- Services
- Risk Type
- Data Breaches
- Doxing & Swatting
- Identity Theft & Account Takeover
- Malware & Viruses
- Phishing
- Platform
- Console
- Mobile
- Android
- iOS
- PC
- Linux
- MacOS
- Windows
- Deployment Mode
- Cloud
- On Premises
- End User
- Game Developers
- Gamers
- Casual
- Competitive
- Americas
- North America
- United States
- Canada
- Mexico
- Latin America
- Brazil
- Argentina
- Chile
- Colombia
- Peru
- North America
- Europe, Middle East & Africa
- Europe
- United Kingdom
- Germany
- France
- Russia
- Italy
- Spain
- Netherlands
- Sweden
- Poland
- Switzerland
- Middle East
- United Arab Emirates
- Saudi Arabia
- Qatar
- Turkey
- Israel
- Africa
- South Africa
- Nigeria
- Egypt
- Kenya
- Europe
- Asia-Pacific
- China
- India
- Japan
- Australia
- South Korea
- Indonesia
- Thailand
- Malaysia
- Singapore
- Taiwan
- Cloudflare, Inc.
- Akamai Technologies, Inc.
- Radware Ltd.
- Fortinet, Inc.
- Imperva, Inc. by Thales SA
- NETSCOUT Systems, Inc.
- Arkose Labs, Inc.
- Irdeto B.V.
- Human Security, Inc.
- McAfee, LLC
- Digital.ai Software, Inc.
- Gen Digital Inc.
- NAGRAVISION S.à.r.l
- OneSpan Inc.
- Noventiq Holdings plc
- F-Secure
- Palo Alto Networks, Inc.
- Trend Micro Incorporated
- Bitdefender SRL
- Cisco Systems Inc.
- Amazon Web Services, Inc.
- Microsoft Corporation
- AO Kaspersky Lab
- Google LLC by Alphabet Inc.
- Tencent Holdings Limited
- Ubisoft Entertainment SA
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
3. Executive Summary
4. Market Overview
7. Cumulative Impact of Artificial Intelligence 2025
List of Figures
Samples

LOADING...
Companies Mentioned
The key companies profiled in this Online Gaming Security market report include:- Cloudflare, Inc.
- Akamai Technologies, Inc.
- Radware Ltd.
- Fortinet, Inc.
- Imperva, Inc. by Thales SA
- NETSCOUT Systems, Inc.
- Arkose Labs, Inc.
- Irdeto B.V.
- Human Security, Inc.
- McAfee, LLC
- Digital.ai Software, Inc.
- Gen Digital Inc.
- NAGRAVISION S.à.r.l
- OneSpan Inc.
- Noventiq Holdings plc
- F-Secure
- Palo Alto Networks, Inc.
- Trend Micro Incorporated
- Bitdefender SRL
- Cisco Systems Inc.
- Amazon Web Services, Inc.
- Microsoft Corporation
- AO Kaspersky Lab
- Google LLC by Alphabet Inc.
- Tencent Holdings Limited
- Ubisoft Entertainment SA
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 189 |
| Published | October 2025 |
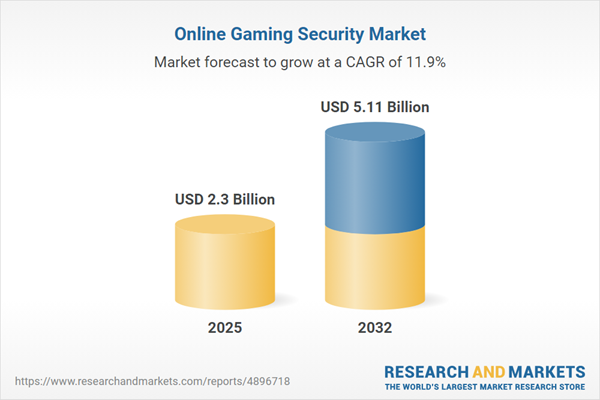
| Forecast Period | 2025 - 2032 |
| Estimated Market Value ( USD | $ 2.3 Billion |
| Forecasted Market Value ( USD | $ 5.11 Billion |
| Compound Annual Growth Rate | 11.9% |
| Regions Covered | Global |
| No. of Companies Mentioned | 27 |