Speak directly to the analyst to clarify any post sales queries you may have.
An authoritative primer explaining how encryption has evolved into a strategic pillar for data protection governance and operational resilience across modern enterprise environments
The contemporary encryption software landscape sits at the intersection of accelerating digital transformation, heightened regulatory scrutiny, and an expanding threat environment. Organizations are adopting encryption not as a single control but as a pervasive architecture that spans data at rest, data in transit, and data in use. This shift elevates cryptographic strategy from an IT task to a board-level priority where risk management, compliance, and business continuity converge.As enterprises diversify workloads across cloud, hybrid, and on-premises environments, cryptographic controls must be rethought to preserve portability, maintain performance, and simplify key lifecycle management. Security practitioners increasingly expect encryption solutions to support interoperability across heterogeneous stacks while delivering transparent performance and minimal operational overhead. At the same time, the rise of regulatory mandates focused on data protection and privacy demands demonstrable, auditable encryption capabilities that map to legal and industry-specific obligations.
Threat actors are leveraging more sophisticated tools, including automation and commoditized exploit kits, which intensifies the need for defense-in-depth architectures that position encryption as a last line of defense. Advances in cryptographic engineering, such as the emergence of post-quantum considerations and hardware-backed key storage, introduce new technical trade-offs for practitioners. Consequently, technology selection now requires balancing maturity and innovation together with maintainability and vendor maturity.
Taken together, these forces create an environment where strategic choices about encryption have immediate operational consequences and long-term implications for resilience and regulatory alignment. This report unpacks those choices, offering a structured view to help leaders prioritize investments, integrate cryptography into broader cloud and data architectures, and align technical roadmaps with evolving risk appetites.
A comprehensive overview of the converging technological and regulatory dynamics reshaping encryption strategy and vendor differentiation in modern enterprise ecosystems
The landscape for encryption software is undergoing transformative shifts driven by converging technological, regulatory, and operational vectors. Cloud-native workloads and distributed architectures require encryption that is platform-agnostic, policy-driven, and capable of seamless key orchestration across public, private and hybrid estates. This migration away from siloed cryptographic controls toward centralized key management and policy enforcement introduces new expectations for service-level interoperability and governance.Simultaneously, regulatory frameworks across jurisdictions are elevating accountability for data protection and breach disclosure, which compels organizations to adopt encryption as a demonstrable control rather than an aspirational security feature. This regulatory pressure is complemented by procurement and insurer requirements that increasingly view strong cryptographic practices as prerequisites for risk transfer and third-party relationships. As a result, compliance, auditability, and cryptographic assurance are becoming core differentiators for vendors.
On the technology front, hardware-backed security modules, secure enclaves, and integrated key management services are converging to provide stronger tamper resistance and simplified developer experiences. The emergence of post-quantum cryptography discussions has shifted roadmaps even in organizations that do not expect quantum impact in the immediate term, influencing selections around algorithm agility and update pathways. Threat intelligence improvements, including automated detection of cryptographic misuse and misuse patterns in telemetry, are enabling more proactive remediation workflows that tie into security orchestration.
These shifts collectively push the market toward solutions that offer not only robust algorithms but also operational tooling, policy automation, and demonstrable compliance artifacts. Businesses must therefore adapt procurement, operations, and security architectures to these new imperatives, rethinking vendor selection criteria and governance models to ensure encryption delivers both technical protection and verifiable assurance.
An analytical assessment of how 2025 United States tariff changes have reconfigured hardware sourcing, procurement strategies, and service delivery models for encryption deployments
U.S. tariff adjustments and trade policy changes enacted in 2025 have introduced a range of operational and sourcing considerations for vendors and customers within the encryption software ecosystem. Increased tariffs on hardware components and legacy appliances used for cryptographic acceleration raise procurement costs for integrated hardware-software solutions, prompting purchasers to reassess total cost of ownership and prioritize software-centric or cloud-based alternatives where feasible. These dynamics encourage a shift away from heavy reliance on vendor-specific hardware modules toward flexible, cloud-native key management and software cryptographic primitives.Supply chain fragmentation resulting from tariff-driven supplier realignment has also affected the availability and lead times of specialized components, particularly for hardware security modules and tamper-resistant devices. Organizations that previously planned firmware-dependent rollouts may need to recalibrate deployment timelines and embrace modular architectures that allow incremental upgrades without wholesale hardware refresh. Moreover, heightened trade friction can complicate cross-border support and warranty arrangements, increasing the operational risk profile for multinational deployments.
Service providers and cloud platforms have responded by expanding local data center footprints and by offering managed cryptographic services that absorb hardware procurement complexity from customers. This response reduces capital outlays for enterprises but increases reliance on vendor-managed controls and third-party attestations. The tariff environment further amplifies the importance of contract language addressing compliance with export controls, localization requirements, and supply continuity, as legal teams now play a more central role in procurement decisions.
In sum, the cumulative effect of tariff changes is not merely an uplift in procurement cost but a structural nudge toward more software-driven designs, localized service delivery, and contractual safeguards. Security architects and procurement officers must work in tandem to mitigate these headwinds by adopting modular cryptographic approaches, diversifying supplier relationships, and insisting on transparency around component provenance and supportability.
A deep segmentation analysis that aligns encryption architecture choices with organization scale, deployment mode nuances, cryptographic types, and end user vertical expectations
Understanding segmentation is essential to aligning encryption capabilities with organizational needs and operational constraints. Based on encryption type, deployments are categorized across Asymmetric and Symmetric approaches, where asymmetric cryptography remains foundational for identity, key exchange, and digital signatures while symmetric algorithms are typically favored for high-performance bulk data protection. These two approaches are complementary, and practical architectures often orchestrate both to balance security properties with throughput and latency requirements.Based on organization size, requirements diverge between Large Enterprise and Small And Medium Enterprise environments, where large entities commonly demand enterprise-grade key management, multi-tenancy controls, and integration into sprawling identity and access management ecosystems, whereas smaller organizations prioritize ease of deployment, predictable pricing, and managed services that reduce operational overhead. Choices around automation, logging fidelity, and integration depth therefore track closely with organizational scale and maturity.
Based on deployment mode, solutions are evaluated across Cloud, Hybrid, and On Premises architectures, with the Cloud category further studied across Private and Public models. Public cloud environments appeal for elasticity and managed cryptographic services, while private cloud deployments are selected for stronger control over isolation and compliance. Hybrid strategies are frequently adopted to balance regulatory and latency constraints, necessitating unified key policies and consistent identity frameworks across all environments.
Based on end user verticals, patterns vary across Banking Financial Services Insurance, Government, Healthcare, and Information Technology Telecom sectors. Financial services and government prioritize rigorous audit trails, hardware-backed key custody, and long-term archival integrity. Healthcare emphasizes data subject privacy and constrained interoperability with legacy clinical systems, while IT and telecom sectors require high-throughput, low-latency encryption integrated into network functions and customer-facing services. Recognizing these segmentation distinctions enables vendors and buyers to reconcile cryptographic properties, operational maturity, and regulatory obligations when architecting solutions.
Regional dynamics and regulatory contrasts that determine encryption strategy, procurement priorities, and supply chain resilience across the Americas, EMEA, and Asia-Pacific
Geography matters for encryption strategy because regulatory regimes, threat actor profiles, infrastructure maturity, and consumer data expectations differ markedly across regions. The Americas exhibit a blend of innovation and regulatory patchwork, with large-scale cloud adoption and diverse enterprise requirements driving demand for flexible managed key services, while state and federal regulations emphasize breach notification and data protection obligations that shape procurement and compliance activities. Regional concentration of hyperscale cloud providers also influences vendor choices and integration patterns.Europe, Middle East & Africa present a heterogeneous landscape where stringent data protection rules and regional privacy frameworks elevate the importance of data localization, demonstrable encryption controls, and strong auditability. In many countries within this region, public-sector procurement and critical infrastructure standards push organizations toward hardware-backed custody and explicit cryptographic assurance. Local vendor ecosystems and compliance ecosystems vary, requiring tailored approaches to deployment and third-party risk management.
Asia-Pacific continues to be characterized by rapid digital adoption, large-scale public cloud investments, and regulatory modernization efforts that vary by country. In this region, high-growth digital-native enterprises often prioritize scalability and developer-friendly encryption primitives, while legacy industries demand adaptable solutions that interoperate with established operational technologies. Geopolitical dynamics can also shape cross-border data flows and technology sourcing, making supply chain transparency and contractual risk allocation critical considerations for global organizations operating in or sourcing from this region.
A competitive landscape synopsis highlighting the technical differentiators, operational assurances, and service capabilities that define vendor selection criteria in enterprise encryption
The competitive environment among encryption software providers emphasizes several recurring capabilities that drive buyer preference. Robust key lifecycle management, including strong access controls, automated rotation, and tamper-evident audit trails, is a baseline expectation. Vendors that combine these controls with developer-friendly APIs, SDKs and seamless cloud integrations command greater interest, as they reduce time-to-production and operational friction for engineering teams.Another differentiator is the ability to offer hybrid control planes that deliver consistent policy enforcement across public cloud, private cloud and on-premises environments. Products that enable unified policy modeling and cross-boundary key portability simplify governance and lower integration costs for large-scale enterprises. Additionally, hardware-backed security options, such as HSM integrations and support for secure enclave primitives, remain important for customers with high-assurance needs and regulatory constraints that mandate physical tamper resistance.
Operational transparency and third-party attestations are increasingly central to vendor evaluations. Buyers expect clear documentation on cryptographic primitives, algorithm agility, compliance mappings, and incident response playbooks. Vendors that provide demonstrable evidence of secure development practices, independent cryptographic review, and continuous monitoring capabilities gain credibility among risk-averse purchasers. Finally, the ability to deliver managed services and professional services that accelerate deployment and adapt default configurations to sector-specific compliance requirements often tips procurement decisions in favor of vendors that pair technology with execution capability.
Actionable, prioritized steps for security and business leaders to strengthen cryptographic posture while preserving operational agility and regulatory alignment
Leaders should adopt a pragmatic, phased approach to strengthening cryptographic posture that balances immediate risk reduction with long-term architectural modernization. Begin by conducting a critical asset inventory and mapping data flows to identify where encryption will materially reduce risk and satisfy compliance obligations. This evidence-based prioritization ensures investment is aligned to the highest-impact controls rather than dispersed across low-value use cases.Next, implement policy-driven key management that decouples key lifecycle operations from individual applications and platforms. Standardizing on a central policy framework and enforcing it through automation reduces configuration drift and simplifies audits. Where possible, prefer solutions that provide cross-environment policy consistency so that encryption controls remain uniform across public cloud, private cloud and on-premises deployments.
Architect for future agility by selecting vendors and primitives that support algorithm agility and modular key custody options. This design principle allows organizations to respond to emerging cryptographic developments, such as post-quantum readiness, without wholesale reengineering. In parallel, strengthen procurement and contract clauses to require supply chain transparency, clear SLAs for security updates, and artifacts for independent verification.
Finally, invest in operational readiness through targeted training, runbooks, and incident simulations that incorporate cryptographic failure modes. Complement technical controls with governance processes that assign clear ownership for key management, periodic reviews of cryptographic posture, and a lifecycle plan for algorithm and infrastructure upgrades. These steps create a sustainable program that reduces operational risk and supports evolving business needs.
A transparent description of the multi-method research approach combining expert interviews, vendor capability analysis, and anonymized case studies to derive actionable encryption insights
The research underpinning this executive summary synthesizes technical literature, vendor documentation, regulatory texts, and primary interviews with technical leaders and procurement specialists across multiple industries. The methodology combined qualitative interviews that explored deployment challenges and priorities with structured reviews of vendor capabilities to identify common feature sets and integration patterns. Secondary sources were used to corroborate technical assertions and to map regulatory obligations against typical enterprise architectures.Case-based analysis of representative deployments provided insight into integration trade-offs and operational practices that succeed in production environments. These case examples were anonymized and generalized to ensure the findings are applicable across sectors with similar constraints. Additionally, scenario analysis examined the implications of supply chain shocks and policy shifts to surface resilient design patterns and contractual controls that organizations should adopt.
Throughout the research process, emphasis was placed on triangulating evidence from multiple perspectives-technical operators, compliance owners, and procurement professionals-to minimize bias and ground recommendations in operational reality. The result is a pragmatic framework that emphasizes actionable controls, vendor selection criteria, and governance practices that practitioners can adopt incrementally to improve cryptographic effectiveness.
A concise synthesis emphasizing the strategic role of encryption as a foundational capability for trust, compliance, and operational resilience across modern enterprises
Encryption has moved from being a checkbox control to a strategic enabler of trust, resilience, and regulatory compliance. The confluence of cloud adoption, regulatory tightening, and evolving threat capabilities means that cryptographic decisions now carry operational, legal, and financial consequences that extend beyond traditional security teams. Organizations that treat encryption as an integrated architectural capability-backed by clear policies, automated key management, and contractual safeguards-will be better positioned to protect data, support regulatory obligations, and sustain digital transformation initiatives.Actionable progress requires alignment across security, engineering, procurement, and legal functions to ensure that technical design choices are matched by operational processes and contractual protections. Vendors that provide both robust technical primitives and operational services that lower integration complexity will continue to be preferred in environments where time-to-value and demonstrable assurance matter most. While ongoing shifts in policy and technology will demand continuous attention, the underlying imperative is straightforward: prioritize verifiable, auditable, and manageable cryptographic controls that integrate with existing workflows and cloud-native practices.
In closing, the path forward is to combine tactical remediation of high-risk exposures with strategic investments in interoperable, policy-driven cryptographic foundations. This balanced approach will enable organizations to reduce near-term risk while building the flexibility needed to adapt to future cryptographic and regulatory developments.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
16. China Encryption Software Market
Companies Mentioned
The key companies profiled in this Encryption Software market report include:- Amazon Web Services, Inc.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cryptomathic Ltd.
- CyberArk Software, Inc.
- Dell Technologies Inc.
- ESET spol. s r.o.
- F-Secure Corporation
- Fortinet, Inc.
- Google LLC
- Hewlett Packard Enterprise Company
- International Business Machines Corporation
- McAfee Corp
- Microsoft Corporation
- Oracle Corporation
- PKWARE, Inc.
- Proofpoint, Inc.
- Thales S.A.
- Trend Micro Incorporated
- Utimaco GmbH
- Venafi, Inc.
- VMware, Inc.
- WinMagic Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 180 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
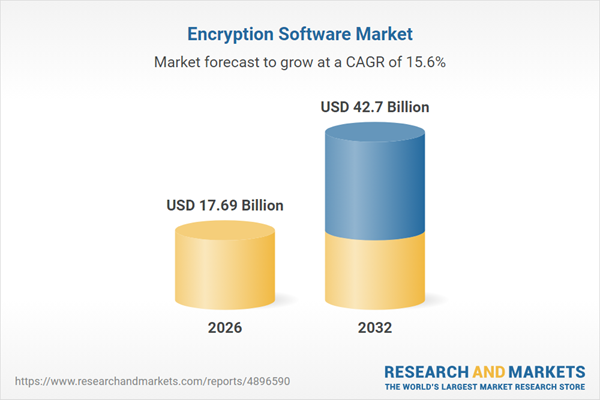
| Estimated Market Value ( USD | $ 17.69 Billion |
| Forecasted Market Value ( USD | $ 42.7 Billion |
| Compound Annual Growth Rate | 15.6% |
| Regions Covered | Global |
| No. of Companies Mentioned | 25 |