Speak directly to the analyst to clarify any post sales queries you may have.
An authoritative strategic framing for leaders modernizing physical identity and access management to balance user experience, security, and regulatory compliance
Physical identity and access management sits at the intersection of security architecture, operational resilience, and digital transformation. Organizations are increasingly confronted with hybrid physical-digital perimeters where access points range from traditional door controllers to cloud-managed visitor systems and biometric-enabled kiosks. Decision-makers must therefore balance frictionless user experiences with stringent authentication controls, while ensuring operational continuity across distributed sites and increasingly remote workforces.This introduction clarifies contemporary imperatives: integrating identity-first thinking into physical security, aligning technologies with regulatory obligations, and embedding scalable processes that support continuous verification. It also highlights the need for cross-disciplinary governance that brings together facilities management, IT security, and legal teams to assess risk tolerance and policy enforcement. By foregrounding these priorities, security leaders can better sequence investments, evaluate vendor propositions, and design deployment models that reduce complexity.
Finally, the introduction frames how subsequent sections examine market shifts, tariff-driven supply chain effects, segmentation insights, regional dynamics, competitive behaviors, recommended actions, and research rigor. This framing helps readers rapidly orient to the strategic choices ahead and positions the ensuing analysis as a practical guide for leaders charged with modernizing access management across diverse environments.
Critical transformative dynamics reshaping physical identity and access management driven by edge intelligence, hybrid architectures, and evolving threat and operational models
The landscape for physical identity and access management is undergoing transformative shifts driven by technological convergence, changing threat profiles, and evolving user expectations. Edge compute and AI-enabled biometrics are moving decision-making closer to endpoints, enabling faster authentication while creating new data governance considerations. At the same time, cloud-native management consoles and zero-trust principles are reshaping how organizations think about trust boundaries, leading to hybrid architectures that blend on-premises controllers with cloud orchestration.Concurrently, adversaries are increasingly leveraging social engineering and credential replay techniques that exploit weak physical authentication, prompting a reassessment of multi-factor strategies and tamper-resistant hardware. Interoperability expectations have grown as enterprises seek vendor-agnostic integrations with HR systems, building automation, and identity providers. Standards work and API-driven integrations are therefore critical enablers for scale and future-proofing.
Finally, operational models are evolving. Managed services and outcome-based contracts are becoming more prevalent as organizations look to offload routine administration and focus internal teams on exceptions and policy governance. These shifts collectively demand that security and facilities leaders adopt a strategic architecture mindset, prioritize modular investments, and insist on demonstrable privacy and resiliency controls when evaluating new solutions.
How recent tariff measures have reshaped procurement, sourcing, and design priorities across hardware-reliant access control ecosystems with adaptive mitigation strategies
Tariff actions instituted in 2025 have exerted a cumulative influence across procurement, sourcing strategies, and vendor cost models within the physical identity and access management ecosystem. Hardware-dependent components such as biometric readers, access control panels, and credentialing devices have been most directly affected by increased import duties, which has compelled buyers and integrators to reevaluate total landed costs and long-term maintenance agreements. In response, procurement teams have widened supplier searches, placed greater emphasis on local assembly or regional supply partners, and renegotiated service-level terms to mitigate potential price volatility.Beyond procurement, tariffs have accelerated product roadmaps toward software-centric value propositions and cloud-managed offerings that reduce reliance on imported physical components. Vendors have responded by accelerating modular designs that enable incremental upgrades, reducing the need for wholesale hardware replacements. Meanwhile, service partners have expanded stocking strategies and introduced component lifecycle management services to smooth operational continuity for end users.
Regulatory and contractual implications have also emerged. Organizations operating across borders have increased scrutiny of warranties, parts availability clauses, and contractual indemnities to reduce exposure to tariff-driven shortages. Taken together, these changes reinforce the imperative for comprehensive supplier risk assessments and adaptive sourcing strategies that preserve security posture without compromising access availability.
Comprehensive segmentation intelligence revealing how solution type, authentication methods, deployment models, organizational scale, and vertical demands shape adoption choices
Segment-driven analysis reveals how solution design, authentication modality, deployment preferences, organizational size, and vertical use cases collectively determine purchaser requirements and adoption pathways. Based on solution type, the market divides into hardware, services, and software, with hardware encompassing access control panels, biometric readers, and card readers, services covering managed services and professional services, and software split between cloud and on-premises delivery models. These distinctions influence investment timing and integration challenges, with hardware-heavy programs requiring stronger logistics planning while software-dominant strategies emphasize interoperability and rapid policy updates.Based on authentication type, solutions range across biometric, password/PIN, RFID, and smart card approaches, with biometric technologies further differentiated into facial recognition, fingerprint, iris recognition, and voice recognition modalities. Each authentication class presents unique trade-offs between usability, spoof-resistance, and privacy obligations, shaping how organizations deploy multifactor strategies and how they manage user consent and data retention. Based on deployment mode, the market separates into cloud and on-premises options, with cloud offerings prioritizing centralized policy control and remote management while on-premises installations offer lower-latency decisioning and localized data governance.
Based on organization size, buyers are distinguished between large enterprises and small and medium organizations, a segmentation that correlates with procurement complexity, governance maturity, and appetite for managed services. Based on end-user vertical, real-world requirements differ across banking, finance and insurance, government, healthcare, retail, and transportation and logistics, where regulatory regimes, peak throughput needs, and physical site characteristics drive tailored solution architectures. Integrating these segmentation lenses enables more precise vendor evaluation, deployment sequencing, and long-term operations planning.
Regional operational and regulatory variances that dictate differential solution preferences and deployment strategies across the Americas, EMEA, and Asia-Pacific
Regional dynamics materially influence technology preferences, procurement practices, and regulatory constraints, producing distinct strategic priorities across major geographies. In the Americas, buyers frequently prioritize integration with enterprise identity providers, data privacy compliance frameworks, and scalability for geographically dispersed facilities, resulting in strong demand for hybrid solutions that combine cloud orchestration with local decisioning. Conversely, Europe, Middle East & Africa features a mosaic of regulatory environments and standards expectations, with heightened scrutiny on biometric data protection and a corresponding emphasis on privacy-preserving deployments and transparent processing measures.Meanwhile, Asia-Pacific is characterized by rapid technology adoption, dense urban deployments, and supply chain concentration, driving interest in high-throughput biometrics and tightly integrated building management systems. Regional vendor ecosystems also vary, where local manufacturing footprints and regional distributors can materially reduce procurement friction and improve post-deployment support. Cross-region organizations must therefore reconcile divergent compliance obligations, regional supply chain constraints, and differing user expectations when designing global access strategies.
Taken together, these regional insights underline the importance of flexible architectures and governance frameworks that can be adapted to local legal and operational realities while maintaining consistent corporate security standards.
Competitive landscape patterns showing how product extensibility, channel partnerships, managed services, and privacy assurances determine market leadership and customer retention
Competitive dynamics in the physical identity and access management domain are defined by product differentiation, service delivery models, partner ecosystems, and the ability to demonstrate security efficacy at scale. Market leaders differentiate through integration breadth, offering robust APIs and prebuilt connectors to HR systems, identity providers, and building automation platforms. At the same time, companies investing in platform extensibility and modular hardware reduce friction for customers seeking incremental upgrades rather than wholesale replacements.Service providers and channel partners play a pivotal role in scaling deployments, especially where managed services, long-term maintenance, and custom integration are required. Firms that cultivate deep systems integration expertise and regional support networks secure enduring customer relationships and higher lifetime engagement. Meanwhile, vendors emphasizing privacy by design and certification-driven controls can reduce adoption barriers in regulated verticals such as healthcare and government.
Finally, business models are evolving with subscription pricing, outcome-based contracts, and bundled service offerings that align vendor incentives with customer uptime and security outcomes. Competitive success increasingly depends on the ability to combine credible technical innovation with predictable delivery and transparent governance.
Actionable strategic recommendations for leaders to prioritize interoperability, resilient sourcing, layered authentication, and cross-functional governance to accelerate secure deployments
Industry leaders should adopt a proactive, architecture-first approach that balances operational resilience with user-centric access models. Begin by prioritizing interoperability: insist on open APIs, standardized data schemas, and vendor-agnostic integrations to avoid lock-in and to enable phased modernization. Concurrently, implement a layered authentication strategy that pairs biometric modalities with fallback factors such as smart cards or device-based tokens, thereby minimizing single-point failures while enhancing fraud resistance.Leaders must also strengthen supply chain resilience by qualifying secondary suppliers, negotiating parts availability clauses, and considering regional assembly or stocking agreements to mitigate tariff and logistics disruptions. From an organizational perspective, align facilities, IT, and security teams through a formal governance forum that defines policy, incident escalation, and privacy obligations. Invest in managed services where operational scale or skill gaps challenge internal teams, and ensure clear handoffs and performance metrics in vendor contracts.
Finally, embed privacy-preserving practices and transparent user communications into every deployment, including data minimization, purpose limitation, and clear retention policies. This will not only reduce legal risk but also build user trust, which is critical for adoption of biometric and continuous authentication methods.
A rigorous mixed-methods research approach combining expert interviews, technology assessments, regulatory validation, and scenario stress-testing to ensure credible findings
The research underpinning this report employs a mixed-methods approach that integrates primary expert interviews, technology capability assessments, and secondary validation across regulatory and standards documents. Primary inputs include structured discussions with security architects, facilities managers, procurement leads, and systems integrators to capture real-world deployment constraints and buyer priorities. Technology assessments evaluate product architectures for interoperability, cryptographic hygiene, hardware tamper-resistance, and administrative control planes.Secondary validation involved reviewing public regulatory frameworks, technical standards, and industry guidance to ensure that interpretations of privacy and compliance obligations reflect contemporary legal expectations. The methodology also incorporates scenario-based stress testing of sourcing and tariff impacts to understand operational vulnerabilities and mitigation options. Throughout the process, findings were triangulated across multiple evidence streams to limit single-source bias and to enhance the reliability of conclusions.
A transparent audit trail of methodological choices, interview sampling, and assessment criteria is provided to support reproducibility and to enable readers to evaluate the fit of the analysis to their own organizational contexts.
Concluding strategic synthesis emphasizing modular architecture, privacy-first deployments, resilient sourcing, and cross-functional governance to secure physical access ecosystems
In conclusion, modern physical identity and access management is no longer a purely facilities-driven concern but a strategic capability that bridges security, compliance, and user experience. The interplay of edge intelligence, cloud orchestration, evolving biometrics, and supply chain dynamics requires leaders to adopt modular architectures, prioritize interoperable integrations, and maintain adaptable sourcing strategies. Doing so reduces operational risk while enabling secure, friction-optimized access across diverse work environments.Organizations that proactively integrate privacy-preserving design, robust vendor governance, and cross-functional operational alignment will be best positioned to respond to regulatory changes and emergent threats. Moreover, the shift toward service-oriented delivery models and subscription pricing opens new pathways for sustained improvement and predictable operational expenditure. Ultimately, a deliberate, evidence-based modernization program that balances technology, process, and policy will deliver measurable gains in security posture, user trust, and operational efficiency.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
17. China Physical Identity & Access Management Market
Companies Mentioned
The key companies profiled in this Physical Identity & Access Management market report include:- Access Security Corporation
- AlertEnterprise Inc.
- AMAG Technology, Inc.
- Amazon Web Services, Inc.
- Anviz Global Inc.
- Atos SE
- Brivo Inc.
- Capgemini SE
- Genetec Inc.
- HID Global Corporation
- Honeywell International Inc.
- IBM Corporation
- IDCUBE Identification Systems (P) Ltd.
- Identiv Inc.
- Infosys Limited
- Johnson Controls International plc
- Micro Focus International plc
- Microsoft Corporation
- Nexus Group AB
- Okta Inc.
- One Identity LLC
- Oracle Corporation
- Thales Group
- Wipro Limited
- ZKTeco Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 181 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
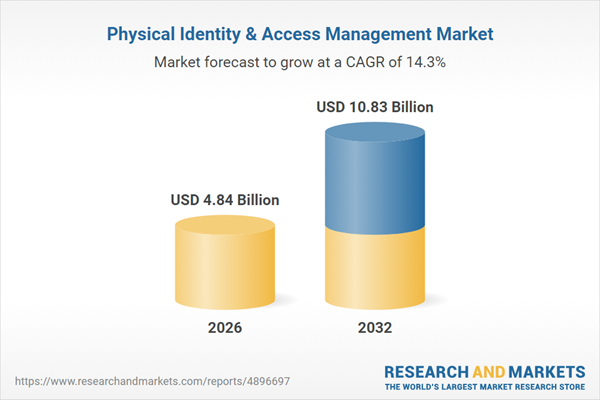
| Estimated Market Value ( USD | $ 4.84 Billion |
| Forecasted Market Value ( USD | $ 10.83 Billion |
| Compound Annual Growth Rate | 14.3% |
| Regions Covered | Global |
| No. of Companies Mentioned | 26 |