ISO 28000 Supply Chain Management Audit Program Added
Compliance Management Tool Kit - Defines Best Practices
PCI-DSS, Sarbanes-Oxley, HIPAA, GDPR, CCPA, GLAB, COBIT, and ISO 28000 Compliance Tools
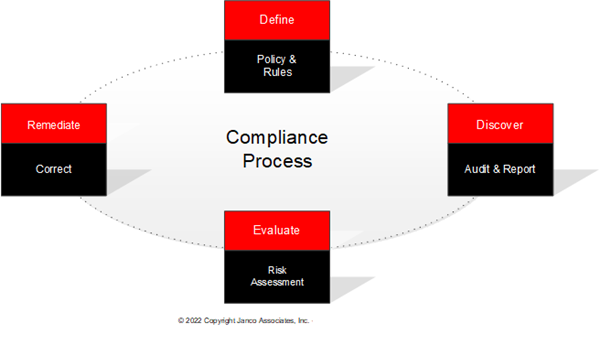
Numerous laws and regulatory mandates focus on corporate governance and accountability around sensitive information (specifically financial, non-public information and protected health care information). This has significantly impacted the underlying IT systems that support the applications and repositories holding this sensitive information.
Organizations are continuously looking for help in preventing fraud and protecting sensitive information. The fact that key corporate executives carry personal liability in the event of non-compliance virtually ensures compliance is a key initiative in any large organizations. Additionally, there are other internal cost-containment requirements that can be effectively met by defining and implementing a sound auditing and compliance methodology. Most corporations agree that compliance leads to better corporate governance and management.
The Kit comes in three versions. Each version contains the Compliance Management White Paper, ISO 28000 Security Audit Program (Supply Chain Management), a self-scoring Security Audit Program, a PCI Audit Program, and 31 key job descriptions including one for the Chief Compliance Officer which is six pages in length.
Recent ransomware attacks focused most C-Level executives on asset security and compliance as more business is conducted on the Internet. In addition, not meeting compliance mandates exposes enterprises to damaged reputations and fines. The Compliance Management Kit provides tools that are properly implemented minimize those risks. The Compliance Management Kit is the must-have tool to meet mandated governmental and industry compliance objectives.
Compliance Management - Gold Edition
- Compliance Management White Paper
- HIPPA Audit Program
- Security Audit Program
- Supply Chain ISO 28000 Audit Program
- PCI Audit Program
- Compliance Management Job Descriptions (25 key positions)
- Record Classification and Management Policy - Word - Policy which complies with mandated US, EU, and ISO requirements
- Privacy Compliance Policy that addresses the EU's GDPR and the latest California Consumer Privacy Act
Table of Contents
- License Conditions
- Compliance Management
- Compliance Requirements
- Record Classification, Management, Retention, and Destruction
- ISO Security Domains
- ISO 27000
- ISO 28000
- Governmental Mandates
- California Consumer Privacy Act (CaCPA)
- California SB 1386 Personal Information Privacy
- COPPA
- FCRA
- FCTA
- FISMA
- FTC Information Safeguards
- General Data Protection Regulation (GDPR)
- Gramm-Leach-Bliley (Financial Services Modernization)
- HIPAA
- Massachusetts 201 CMR 17.00 Data Protection Requirements
- Sarbanes-Oxley Act
- State Security Breach Notification Laws
- Implementation
- Compliance Tools Purchase Options
- COBIT Edition
- Appendix
- HIPPA Audit Program
- PCI Audit Program
- ISO 28000 - Supply Chain Compliance Audit Program
- Security Audit Program
- Compliance Management Job Description Bundle
- Privacy Compliance Policy
- Record Classification, Management, Retention, Destruction Policy
- Version History
Executive Summary
PCI-DSS, Sarbanes-Oxley, HIPAA, GDPR, CCPA, GLAB, COBIT, and ISO 28000 Compliance Tools
Numerous laws and regulatory mandates focus on corporate governance and accountability around sensitive information (specifically financial, non-public information and protected health care information). This has significantly impacted the underlying IT systems that support the applications and repositories holding this sensitive information.
Organizations are continuously looking for help in preventing fraud and protecting sensitive information. The fact that key corporate executives carry personal liability in the event of non-compliance virtually ensures compliance is a key initiative in any large organizations. Additionally, there are other internal cost-containment requirements that can be effectively met by defining and implementing sound auditing and compliance methodology. Most corporations agree that compliance leads to better corporate governance and management.
Compliance Management Toolkit Versions
Janco offers a full range of tools to help enterprises of all sizes to address these issues. The Compliance Management kit provides necessary the infrastructure governance tools.