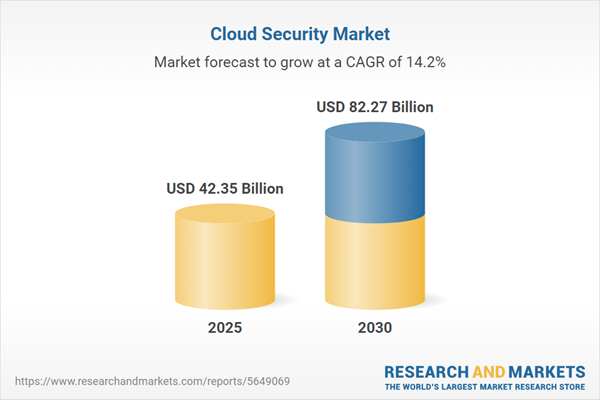
The global cloud security market is poised for substantial growth from 2025 onward, driven by the escalating adoption of cloud services and the rising threat of cyberattacks targeting smartphones and cloud-based systems. Cloud security, encompassing technologies, protocols, and best practices, safeguards data, applications, and infrastructure in cloud computing environments. This report analyzes key market trends, growth drivers, and regional dynamics, highlighting the critical role of cloud security in addressing evolving cyber threats.
Market Trends
The increasing reliance on cloud services, coupled with growing cybercrime, is fueling demand for robust cloud security solutions. Innovations in smartphone technology have expanded the attack surface, necessitating advanced security measures to protect sensitive data. Government initiatives, particularly in North America, are enforcing stricter cloud security protocols, reinforcing the region’s position as the market leader. The surge in cyber threats targeting mobile devices and cloud platforms is expected to sustain North America’s dominance and drive global market growth over the forecast period.Growth Drivers
Increasing Adoption of Mobile Devices
The widespread use of smartphones and smart devices is a significant driver of the cloud security market. Smartphones, integral to daily activities like online banking, shopping, and social media, are vulnerable to cyberattacks, particularly through unsecured Wi-Fi connections. Attackers exploit these vulnerabilities to access sensitive data, such as banking credentials or personal information, increasing the need for cloud security solutions to protect mobile-driven cloud services. The growing integration of cloud-based applications on smartphones amplifies this demand, as organizations seek to secure data across devices and networks.Rising Cybercrime Cases
The proliferation of cloud services for banking, data storage, and other applications has led to a surge in cybercrime, further propelling the cloud security market. High-profile incidents, such as crypto hacks targeting platforms like the Ronin Network, highlight the financial and operational risks of cyberattacks. These incidents underscore the need for advanced security measures to protect cloud-based systems. Organizations are prioritizing robust cloud security protocols to mitigate risks, safeguard sensitive data, and ensure compliance with regulatory standards, driving market expansion.Regional Outlook
North America: Market Leader
North America holds the largest share of the cloud security market, driven by proactive government initiatives and stringent regulations aimed at bolstering cybersecurity. The region’s advanced technological infrastructure and high adoption of cloud services, particularly in industries like finance and healthcare, amplify the demand for cloud security solutions. The increasing frequency of cyberattacks, including ransomware and business email compromise (BEC), further solidifies North America’s position as the market leader, with sustained growth expected through the forecast period.Global Perspective
While North America dominates, other regions are also witnessing growing demand for cloud security due to increasing cloud adoption and cyber threats. The global rise in smartphone usage and cloud-based services is creating a universal need for secure environments, with governments worldwide implementing stricter regulations to protect digital infrastructure.Key Benefits of this Report:
- Insightful Analysis: Gain detailed market insights covering major as well as emerging geographical regions, focusing on customer segments, government policies and socio-economic factors, consumer preferences, industry verticals, and other sub-segments.
- Competitive Landscape: Understand the strategic maneuvers employed by key players globally to understand possible market penetration with the correct strategy.
- Market Drivers & Future Trends: Explore the dynamic factors and pivotal market trends and how they will shape future market developments.
- Actionable Recommendations: Utilize the insights to exercise strategic decisions to uncover new business streams and revenues in a dynamic environment.
- Caters to a Wide Audience: Beneficial and cost-effective for startups, research institutions, consultants, SMEs, and large enterprises.
What do businesses use our reports for?
Industry and Market Insights, Opportunity Assessment, Product Demand Forecasting, Market Entry Strategy, Geographical Expansion, Capital Investment Decisions, Regulatory Framework & Implications, New Product Development, Competitive IntelligenceReport Coverage:
- Historical data from 2022 to 2024 & forecast data from 2025 to 2030
- Growth Opportunities, Challenges, Supply Chain Outlook, Regulatory Framework, and Trend Analysis
- Competitive Positioning, Strategies, and Market Share Analysis
- Revenue Growth and Forecast Assessment of segments and regions including countries
- Company Profiling (Strategies, Products, Financial Information, and Key Developments among others).
Market Segmentation:
By Deployment Model
- Private
- Public
- Hybrid
By SecurityType
- Email and Web Security
- Cloud Database Security And Data Loss Prevention
- Cloud IAM
- Network Security
- Others
By End-User
- Government
- Leisure
- Retail
- BFSI
- Communication and Technology
- Healthcare
- Others
By Geography
- North America
- USA
- Canada
- Mexico
- South America
- Brazil
- Argentina
- Others
- Europe
- United Kingdom
- Germany
- Sweden
- Denmark
- Others
- Middle East and Africa
- UAE
- Israel
- South Africa
- Others
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Others
Table of Contents
Companies Mentioned
- AMAZON WEB SERVICES INC.
- PALO ALTO NETWORK INC.
- CISCO SYSTEMS INC.
- IBM CORPORATION
- FORTINET
- MICROSOFT (MICROSOFT AZURE)
- INTEL SECURITY GROUP
- SKYHIGH SECURITY
- TRUSTWAVE HOLDINGS
- CA TECHNOLOGIES
- TREND MICRO
- AKAMAI TECHNOLOGIES, INC.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 161 |
| Published | July 2025 |
| Forecast Period | 2025 - 2030 |
| Estimated Market Value ( USD | $ 42.35 Billion |
| Forecasted Market Value ( USD | $ 82.27 Billion |
| Compound Annual Growth Rate | 14.2% |
| Regions Covered | Global |
| No. of Companies Mentioned | 12 |