The utilization of hardware & software to track and regulate devices, physical processes, and infrastructure is known as operational technology (OT). Many asset-intensive industries use operational technology systems to fulfil a variety of functions, from managing critical infrastructure (CI) to managing robots on a factory floor.
Manufacturing, electrical generation & distribution, oil and gas, aviation, rail, maritime, and utilities are just a few of the industries that use OT. The digitization of daily life and business over the past two decades has given rise to a number of new participants in the cybersecurity industry. The digitalization of several industries has caused a blurring of the distinctions among operational technology (OT) and information technology (IT) as OT has been brought online.
In these highly complicated contexts, the ensuing "cyber-physical" systems have produced several vulnerabilities and dangers that are challenging to discover. To counter the dangers posed by industrial players, a new generation of specialist security players is currently developing that natively support convergent IT/OT settings. The OT cyber security market currently appears to be in a position to realize its full potential due to regulatory, market awareness, and the availability of innovative solutions.
In the next five years, stakeholders will need to deal with two major issues: first, implementing new OT security solutions that give extensive expertise in asset identification, network visibility, and constant risk monitoring; and second, addressing the talent shortage that is affecting cybersecurity in general and OT security in particular due to the specialized skillset it necessitates. This is expected to increase demand for solutions with significant automation capabilities as well as for managed OT security services.
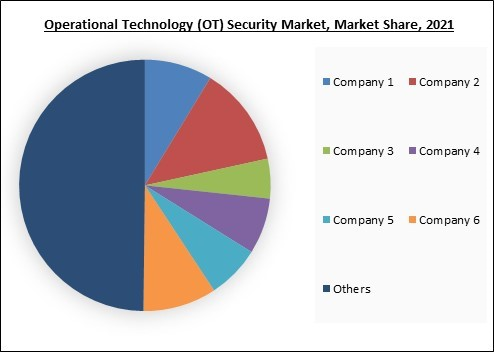
The leading players in the market are competing with diverse innovative offerings to remain competitive in the market. The below illustration shows the percentage of revenue shared by some of the leading companies in the market. The leading players of the market are adopting various strategies in order to cater demand coming from the different industries. The key developmental strategies in the market are Acquisitions.
COVID-19 Impact Analysis
To assist lower the risk of data breaches, vendors are enhancing their OT security solutions with fresh features and putting them on the cloud. Since such solutions need to be implemented from scratch, the market for OT security services is expected to rise. Oil and gas companies were frightened about the possibility of an unusual situation as a result of the pandemic's impact on the fluctuation of oil prices around the world. As a result, big oil and gas firms are implementing OT security solutions to protect their operations. A decrease in supply chain and exports disruptions are two main factors adding to the output fall.Market Growth Factors
High Usage Of Digital Technologies In Industrial Systems
Several industries are undergoing a shift as a result of the evolving technological landscape. The use of technical components in industrial systems to integrate them into a specific ecosystem is positively impacted by the evolving digital landscape. These advancements have the potential to be beneficial for M2M and IIoT, which when combined with these new technologies could provide a heterogeneous landscape for simple platform-to-platform communication.Surge In The Demand For Ot Security Services
While large organizations have a strong foundation for safeguarding their critical infrastructure, SMEs dearth numerous basic cyber infrastructures for defending their internal as well as external enterprise ecosystems. To do this, large organizations require managed & professional services as well as expertise. Small and medium-sized businesses (SMEs) sometimes lack the staff or analytics needed to identify assaults and their patterns on their company, which gives cybercriminals an advantage.Market Restraining Factors
Huge Cost Attached To The Procurement Of Ot Security Solutions
With efficient and safe operations, adopting OT security solutions necessitates company-wide coverage, which drives up infrastructure costs and becomes prohibitively expensive for certain operators. Strong multi-factor authentication is required by the current OT security standards to guarantee that only authorized persons have both physical and logical access to crucial assets. For a vital infrastructure company to implement, up-front costs like licences, hardware needs, help desk fees, and maintenance and renewal operations are expensive.Offering Outlook
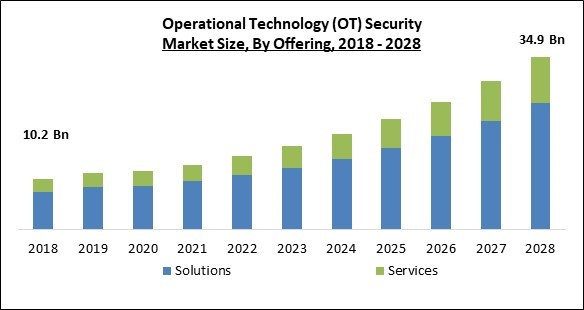
Based on offering, the Operational Technology (OT) Security Market is classified into Solutions and Services. The solution segment procured the highest revenue share in the Operational Technology (OT) Security Market in 2021. Control systems are typically regarded as proprietary and can occasionally be combined from different suppliers. Additionally, OT endpoints are sometimes outdated technology that was never designed to be connected and was created before cyber dangers were recognized as a problem.Deployment Mode Outlook
On the basis of deployment mode, the Operational Technology (OT) Security Market is bifurcated into On-premises and Cloud. The on-premises segment acquired the highest revenue share in the Operational Technology (OT) Security Market in 2021. There is a rise in the investments by companies on the deployment of such advanced solutions and systems. Along with that, the growing cases of data breaches and cyberattacks is compelling companies to implement solution on their premises.Vertical Outlook
By vertical, the Operational Technology (OT) Security Market is divided into BFSI, Manufacturing, Energy & Power, and Oil & Gas. The energy and power segment procured a significant revenue share in the Operational Technology (OT) Security Market in 2021. Increased regulations, more frequent attacks, the requirement for the connection of market players to utility core systems, and, most importantly, the expansion of private consumer data entering utility systems due to smart metering & smart home initiatives, are all challenges that power utilities must deal with.Organization Size Outlook
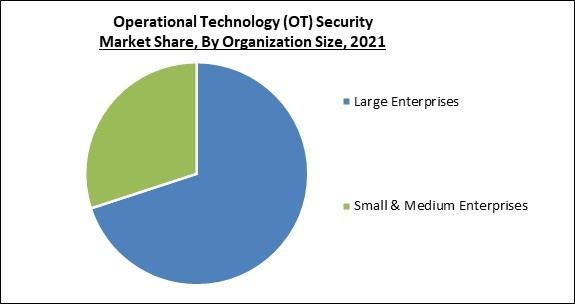
Based on organization size, the Operational Technology (OT) Security Market is segmented into SMEs and Large Enterprises. SMEs segment procured a significant revenue share in the Operational Technology (OT) Security Market in 2021. The requirement for cloud-based OT security solutions from SMEs is increasing as more applications are deployed in the cloud. Because they offer a practical means for businesses across industries to improve cybersecurity, cloud-based OT security solutions are preferable to on-premises security solutions.Operational Technology (OT) Security Market Report Coverage Report Attribute Details Market size value in 2021 USD 13.1 Billion Market size forecast in 2028 USD 34.9 Billion Base Year 2021 Historical Period 2018 to 2020 Forecast Period 2022 to 2028 Revenue Growth Rate CAGR of 15.5% from 2022 to 2028 Number of Pages 269 Number of Tables 433 Report coverage Market Trends, Revenue Estimation and Forecast, Segmentation Analysis, Regional and Country Breakdown, Market Share Analysis, Competitive Landscape, Companies Strategic Developments, Company Profiling Segments covered Offering, Deployment Mode, Organization Size, Vertical, Region Country scope US, Canada, Mexico, Germany, UK, France, Russia, Spain, Italy, China, Japan, India, South Korea, Singapore, Malaysia, Brazil, Argentina, UAE, Saudi Arabia, South Africa, Nigeria Growth Drivers
- High Usage Of Digital Technologies In Industrial Systems
- Surge In The Demand For Ot Security Services
- Huge Cost Attached To The Procurement Of Ot Security Solutions
Regional Outlook
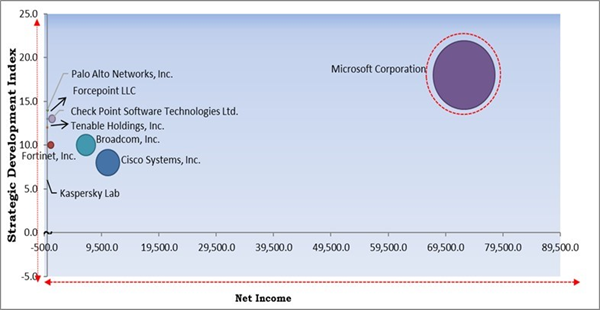
Region-wise, the Operational Technology (OT) Security Market is analyzed across North America, Europe, Asia Pacific and LAMEA. North America emerged as the leading region with the highest revenue share in the Operational Technology (OT) Security Market in 2021. Government initiatives concerning expenditures in OT security as well as R&D activities have led to advancements and are anticipated to do so in the region's cybersecurity environment and fuel the OT security market's future expansion. In this region, technological & digital transformations have been highly inventive and adopted quickly.Cardinal Matrix - Operational Technology (OT) Security Market Competition Analysis
The major strategies followed by the market participants are Product Launches. Based on the Analysis presented in the Cardinal matrix; Microsoft Corporation is the major forerunner in the Operational Technology (OT) Security Market. Companies such as Broadcom, Inc., Cisco Systems, Inc. and Palo Alto Networks, Inc. are some of the key innovators in Operational Technology (OT) Security Market.
The market research report covers the analysis of key stake holders of the market. Key companies profiled in the report include Microsoft Corporation, Broadcom, Inc. (Symantec Corporation), Cisco Systems, Inc., Fortinet, Inc., Forcepoint LLC (Francisco Partners), Tenable Holdings, Inc., Check Point Software Technologies Ltd., FireEye, Inc., Palo Alto Networks, Inc., and Kaspersky Lab.
Strategies deployed in Operational Technology (OT) Security Market
; Partnerships, Collaborations and Agreements:
- Jul-2022: Palo Alto Networks extended its partnership with Deloitte Touche Tohmatsu India, an international professional services network. This partnership aimed to provide comprehensive and end-to-end technology-based cyber incident response services to companies in India.
- Apr-2022: Microsoft extended its partnership with HCL Technologies (HCL), a leading global technology company. Under this partnership, cybersecurity fusion platform solutions of HCL, along with Microsoft’s range of security products, like Azure Sentinel and Microsoft 365 E5, is expected to be covering identity and access, information protection, hybrid cloud infrastructure security, IT (Information Technology), and OT (Operational Technology) security and cloud app security, which is expected to further provide companies the building blocks to defend against a dynamic cybersecurity environment.
- Jan-2022: Palo Alto Networks came into a partnership with KPMG, a multinational professional services network. This partnership aimed to provide Managed Security Services (MSS) powered by Palo Alto Networks Cortextm XDR as well as XSOAR security platform, Zero Trust, and multi-cloud cybersecurity solutions to KPMG customers and clients in India.
- Noc-2021: Palo Alto Networks entered into a partnership with Siemens, a German multinational conglomerate corporation. This partnership aimed to integrate the security vendor’s VM-Series firewalls with Siemens’ Ruggedcom networking and security appliances to enable enterprises to protect their industrial control systems and other major infrastructure without compromising performance, security, or the ability to scale.
- Oct-2021: Forcepoint formed a partnership with KPMG, a multinational professional services network. This partnership aimed to provide data protection services to businesses in India. In addition, the partnership is expected to bring together KPMG in India’s industry-top cyber security services with Forcepoint’s top-class data-first cybersecurity innovations that allow companies and government agencies to safeguard their sensitive data anywhere it is accessed.
- Apr-2021: Broadcom formed a partnership with Google, an American multinational technology company. This partnership aimed to make Broadcom’s enterprise security software available on the Google Cloud Platform. In addition, the partnership aimed to offer secure access to cloud applications and offer enterprises better performance, constant compliance, and enhanced security that is expected to empower an organization’s cloud adoption journey.
- Dec-2020: Kaspersky entered into a memorandum of understanding (MoU) with the Indian Computer Emergency Response (CERT-In). This MoU is expected to work together for developing a cooperative relationship and enable the fulfillment of mutual objectives for making a safe & secure cyberspace in the country.
- Aug-2020: Fortinet entered into a partnership with Schneider Electric, the leader in the digital transformation of energy management and automation. This partnership focused on offering cybersecurity solutions that acknowledge the unique requirements of OT networks.
- Aug-2020: Check Point Software Technologies formed a partnership with Claroty, the global leader in operational technology (OT) security. This partnership aimed to provide companies and critical infrastructure operators the real-time cybersecurity as well as visibility they require to safeguard OT and industrial control system (ICS) networks from cyber-attacks.
; Product Launches and Product Expansions:
- Apr-2022: Fortinet launched FortiOS 7.2, the new upgrades to its flagship operating system and the foundation of the Fortinet Security Fabric. This product is expected to offer new AI-powered FortiGuard security services, advancements to the only converged networking and security platform accessible, and consolidation of security point products across endpoints, networks, and clouds.
- Feb-2022: Forcepoint released Forcepoint ONE, the industry’s first ‘easy button’ for safeguarding enterprises with hybrid workforces. The Forcepoint ONE all-in-one cloud platform is expected to streamline security for conventional and remote workforces, enabling customers to achieve safe, controlled access to business data on the web, in the cloud, and in private applications.
- Nov-2020: Check Point Software Technologies unveiled its next-generation unified cyber security platform, Check Point R81. This product is expected to provide autonomous threat prevention developed for the whole distributed enterprise, allowing IT staff to handle the most complicated and dynamic network environments simply and efficiently.
; Acquisitions and Mergers:
- Jun-2022: Microsoft took over Miburo, a cyber threat analysis, and research company. This acquisition aimed to accelerate threat intelligence research into new foreign cyber threats. Through this acquisition of Miburo, Microsoft is expected to continue its mission to take action, and to partner with others in the public as well as private sectors to get long-term solutions, which is expected to stop foreign adversaries from threatening public and private sector consumers.
- Jun-2022: Microsoft acquired ReFirm Labs, a firmware security startup. This acquisition aimed to protect the internet of things and intelligent edge devices. Along with that, the acquisition is expected to bring top-class expertise in firmware security and the Centrifuge firmware platform to boost their ability to evaluate and assist protect firmware backed by the power and speed of the cloud.
- May-2022: Broadcom acquired VMware, a leading innovator in enterprise software. The Broadcom Software Group is expected to rebrand and work as VMware, including Broadcom's prevailing infrastructure and security software solutions as part of an expanded VMware portfolio.
- Apr-2022: Tenable Holdings acquired Bit Discovery, a leader in external attack surface management (EASM). This acquisition aimed to combine Tenable’s Cyber Exposure solutions with Bit Discovery’s EASM capabilities, which is expected to offer customers a differentiated 360-degree view of the modern attack surface to detect and remove areas of known and unknown security risk.
- Feb-2022: Check Point Software Technologies acquired Spectral, a leading worldwide designer and manufacturer of systems and software. This acquisition aimed to combine Check Point’s cloud security capabilities and threat intelligence tools with Spectral’s security tools for developers to make it possible for companies to deploy security earlier in the software development life cycle.
- Nov-2021: Check Point Software Technologies acquired Avanan, the fastest growing cloud email security company. This acquisition aimed to integrate Avanan technology into the Check Point Infinity architecture to provide the top security to remote workforces worldwide, offering the only unified solution that is expected to safeguard from malicious files, URLs, and phishing over collaborations apps, email, network, web, and endpoint.
- Oct-2021: Forcepoint acquired Bitglass, an information technology company. This acquisition aimed to enable Forcepoint to boost its ability to acknowledge customers’ widespread requirement for allowing hybrid workforces to securely access and utilize data everywhere in the web, cloud, and data center more simply than ever before.
- Oct-2021: Kaspersky completed the acquisition of Brain4Net, an SD-WAN and NFV orchestration software developer. This acquisition aimed to enhance the cloud security capabilities and XDR offering of Kaspersky.
- Sep-2021: Tenable took over Accurics, a pioneer in delivering cloud-native security for both DevOps and security teams. This acquisition aimed to enable Tenable's solutions to include holistic assessment and the automated remediation of policy violations and breach paths before the infrastructure is provisioned and across its lifecycle.
- Jun-2021: Microsoft took over CloudKnox, a developer of a multi-cloud permissions management platform. This acquisition aimed to expand Microsoft's security business. Under this acquisition, CloudKnox’s software is expected to work with Microsoft’s Azure public cloud, and the Amazon and Google clouds.
- Jun-2021: Cisco took over Kenna Security, a cybersecurity leader. Under this acquisition, Kenna’s risk-based vulnerability management technology is expected to companies to work cross-functionally to swiftly detect, prioritize and remediate cyber risks.
- Jun-2021: Forcepoint took over Deep Secure, a UK-based internet security company. This acquisition aimed to add Deep Secure's cybersecurity products and services, which enable safeguard companies from cyberattacks provided through malware and assist prevent unwanted data loss.
- Dec-2020: Palo Alto Networks acquired Expanse, a leader in attack surface management. Under this acquisition, Expanse is expected to bring a distinct level of visibility to security via the constant scanning of exposed assets.
- Sep-2020: Palo Alto Networks acquired the Crypsis Group, a leading incident response, risk management, and digital forensics consulting firm. This acquisition aimed to strengthen the Palo Alto Networks Cortex platform with expert services for incident response and proactive assurance.
- Jun-2020: Microsoft completed the acquisition of CyberX, a robust cybersecurity platform for continuously reducing IoT or OT risks. In the acquisition, CyberX is expected to support the prevailing Azure IoT security capabilities and extend to prevailing devices including those utilized in industrial IoT, Operational Technology, and infrastructure scenarios.
Scope of the Study
Market Segments Covered in the Report:
By Offering- Solutions
- Services
- Manufacturing
- Energy & Power
- Oil & Gas
- BFSI
- Others
- On-premise
- Cloud
- Large Enterprises
- Small & Medium Enterprises
- North America
- US
- Canada
- Mexico
- Rest of North America
- Europe
- Germany
- UK
- France
- Russia
- Spain
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Singapore
- Malaysia
- Rest of Asia Pacific
- LAMEA
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Key Market Players
List of Companies Profiled in the Report:
- Microsoft Corporation
- Broadcom, Inc. (Symantec Corporation)
- Cisco Systems, Inc.
- Fortinet, Inc.
- Forcepoint LLC (Francisco Partners)
- Tenable Holdings, Inc.
- Check Point Software Technologies Ltd.
- FireEye, Inc.
- Palo Alto Networks, Inc.
- Kaspersky Lab
Unique Offerings from the Publisher
- Exhaustive coverage
- The highest number of Market tables and figures
- Subscription-based model available
- Guaranteed best price
- Assured post sales research support with 10% customization free
Table of Contents
Companies Mentioned
- Microsoft Corporation
- Broadcom, Inc. (Symantec Corporation)
- Cisco Systems, Inc.
- Fortinet, Inc.
- Forcepoint LLC (Francisco Partners)
- Tenable Holdings, Inc.
- Check Point Software Technologies Ltd.
- FireEye, Inc.
- Palo Alto Networks, Inc.
- Kaspersky Lab