Key Highlights
- With features including network firewalls, gateway antivirus, gateway anti-spam, VPN, load balancing, data leak prevention, content filtering, and on-appliance reporting, Unified Threat Management (UTM) is a comprehensive security solution with enormous value to businesses. Over the past ten years, there has been a growth in demand for UTM solutions and services due to consolidating all such security capabilities onto a single appliance. Due to its many advantages, including low cost, ease of deployment, and configuration, small businesses were once the primary end users of unified threat management. However, today's enterprises are also adopting UTM solutions because of their scalable and agile features, which can lower energy consumption and increase IT productivity.
- A few main reasons for the rise in demand for UTM solutions include increased data breaches, regulatory compliance, assistance from cutting-edge technology, and the ability to offer increased value to enterprises. In the upcoming years, it is anticipated that the market for unified threat management will experience tremendous expansion.
- Solutions for unified threat management offer numerous benefits in terms of efficiency and integration. The UTM solution has historically been less practical for applications demanding consistent and high network throughput due to the decrease in performance features caused by consolidating multiple security tools into a single network device. This obstacle prevented the Unified Threat Management market from taking off in big businesses. Vendors are now continuously improving the quality and quantity of their solution offerings to meet this challenge and maintain them in line with the needs of large organizations.
- Currently, UTM centralized consoles are used by larger firms' various branch offices to provide security for a whole infrastructure. This eliminates the need to manage individual sites or gateways, which lowers administrative expenses and mistakes.
- Since the COVID-19 epidemic broke out, and since then, there has been a rise in UTM adoption across the board. The need for unified threat management in healthcare has grown along with the exponential increase in COVID-19 patients, hospital admissions, and the greater use of digital health services like electronic medical records (EMR). The demand for unified threat management implementation is increasing due to the increase in online and digital transactions worldwide. The increased use of IT services amid lockdown limitations and work-from-home regulations has increased demand for UTM.
Unified Threat Management Market Trends
Increasing demand for data security is one of the major factor driving growth of the market.
- Several organizations are currently focusing on networking and IT infrastructure, which immediately boosts data generation. Because more data is being generated regularly, these firms are dealing with problems linked to data breaches.
- For IT firms today, protecting a corporate network from attackers has become a serious task. As network operators are compelled to integrate more components to address escalating security concerns, the problem has expanded tremendously in recent years. Enterprises of all sizes are using unified Threat Administration (UTM) solutions, but primarily SMBs, to reduce the complexity of management and combat this rising issue. Intensive point security solutions are being replaced with these alternatives to reduce spending and energy usage.
- Initially, these solutions were used to serve small businesses. Still, due to an increase in the features and applications available in the market for unified threat management, where UTM can be used, the trend of adopting such appliances and services is shifting more and more in favor of mid-sized and enterprise-level businesses.
- Initially, these solutions were used to serve small businesses. Still, due to an increase in the features and applications available in the market for unified threat management, where UTM can be used, the trend of adopting such appliances and services is shifting more and more in favor of mid-sized and enterprise-level businesses.
- The impact of data breaches would hurt the performance of the organizations in terms of customer loss, revenue reduction, loss of competitive advantage, staff productivity, and other factors. To help organizations increase the security level, protection, visibility, and control over the data across the network, UTM solutions contain capabilities like application control, intrusion detection, content filtering, and others. Therefore, UTM solutions would offer a high level of data protection that helps to reduce the loss of sensitive data, consequently driving the growth of the UTM market.
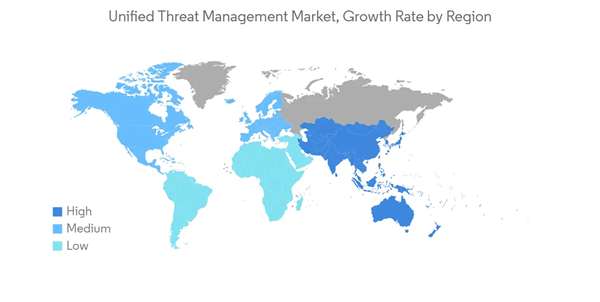
North America to account for significant market growth.
- Due to the region's expanding cloud security infrastructure, the unified threat management (UTM) industry is predicted to rise significantly in North America. Additionally, the area experiences a high volume of cyberattacks, which led to the widespread adoption of UTM solutions and cyber security tools, further bolstering the market's expansion in the area.
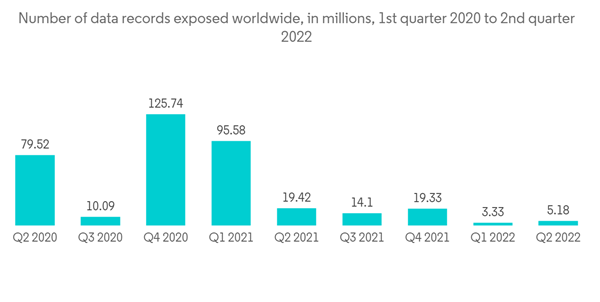
- For instance, according to the Identity Theft Resource Center, nearly 294 million people in the United States were victims of cyber data infractions such as breaches, data exposure, and data leaks in 2021. There were 817 instances of data compromise in the United States in the first half of the last year. There were 785 instances of private data infringement found in the nation in 2015.
- The demand for affordable UTM solutions is expected to increase as the number of SMEs in the area rises. Vendors also frequently update their products by including new features in order to enhance performance and satisfy user demands. The regional market is anticipated to be driven by these factors as well.
- The demand for dependable security and data leak prevention solutions across IT, telecom, BFSI, healthcare, retail, manufacturing, transport, utilities, and other domains can be linked to regional growth trends. Leading unified threat management service providers' presence in the US and Canada will have a favorable effect on the dynamics of regional growth.
Unified Threat Management Market Competitor Analysis
The Unified Threat Management market is competitive owing to the presence of many large and small players operating in the domestic and international markets. The market needs to be more cohesive due to the many technological giants. Key strategies adopted by the major players in the market are product innovation and mergers and acquisitions. Some of the key developments in the market are:- April 2022 - Fleet Secure Unified Threat Management (UTM), a standard feature on Inmarsat's acclaimed Fleet Xpress service, was introduced by the industry-leading mobile satellite communications company Inmarsat to safeguard vessel networks against hackers. Along with Fleet Secure Endpoint and Fleet Secure Cyber Awareness Training, Fleet Secure UTM completes the suite of Inmarsat cyber security products for ship owners. The robustness of Fleet Secure UTM protection, which was created in collaboration with the marine cyber security expert Port-IT, is based on the integration of many network security solutions into a single application.
Additional benefits of purchasing the report:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
This product will be delivered within 2 business days.