Key Highlights
- Security measures protect the network and the points of entry that link internal data to equipment that is connected to the internet externally, such as laptops, mobile phones, and other devices. It is the most effective cybersecurity solution for safeguarding various corporate networks. The sector is expected to grow as the bring-your-own-device (BYOD) policy is increasingly used. This enormous number of gadgets necessitates security solutions and favourably affects the consumer security market.
- There is a significant risk of assaults from inside and outside the company, leaving end-users secret information exposed. Many companies are using artificial intelligence (AI) to combat these threats. Combining AI and machine learning makes recognizing dangers easier, significantly reducing activity. Risks associated with automating endpoint security solutions might be seen simultaneously at multiple security points.
- Enterprises face substantial data risks from various assaults, including zero-day trojans, malware, and advanced persistent threats due to the expansion of business operations. These dangers have forced businesses to implement consumer security software to shield their networks from potential intrusions. In addition to firewalls, intrusion prevention and detection systems, data backup, and encryption, the security providers also offer packages with several other components.
- Bring-your-own-device (BYOD) programs are widely accepted in organizations since they increase employee productivity while saving the company money. BYOD has many advantages, but there could be a security concern. Employees who use outdated technology without security updates make it simple for hackers to take advantage of software flaws. Similarly, if an employee saves their credentials, losing or having their device stolen puts both the local device and the corporate network in danger of a data breach.
- The COVID-19 pandemic has compelled businesses worldwide to act swiftly to secure large numbers of remote workers and upgrade their tooling beyond the basic security measures. Organizations need cybersecurity vendors who can meet their requirements in the perilous threat landscape more than ever because rapid transformations are of utmost importance. Plans and practices for incident response are now being modified or updated because the majority of the security and risk team is working in settings and mindsets entirely different from their previous ones.
Consumer Security Market Trends
Rapid Adoption of Cloud-Based Deployment
- There are several advantages to this deployment strategy that small and medium-sized enterprises may find very helpful. Instead of using their internal servers, businesses use vendor-hosted cloud-based endpoint protection through the internet. These include computers, servers, mobile devices, laptops, desktops, and other internet-connected hardware.
- The user-friendliness of a cloud-based security program is a key component of its success and rapid adoption across the globe. Additionally, cloud solutions are exceedingly simple to set up and may be installed and operational in a matter of minutes. This significantly decreases the installation downtime required by standard endpoint security products. Also, contracts for cloud security often last one to three years. They are, therefore, a fantastic option to re-evaluate after a year to see if the vendor picked still meets the demand needs.
- Cloud antivirus is frequently less expensive than buying a whole software package. Most popular antivirus capabilities, including virus scanning, scan scheduling, reporting, and file cleanup, are included in cloud-based antivirus services. Also, significantly less processing power is required to maintain system security. The only time a user's computer is required to scan their file system is periodic. They need to upload the results because cloud technology will process and interpret the scan data.
- Before cloud computing, a firewall separated a trusted network from an untrusted one, and the trusted and untrusted networks had a distinct border (referred to as a 'network perimeter'). However, this distinction is irrelevant in cloud computing because trusted cloud assets can be accessed across an unreliable network (the internet). Despite the lack of a network border, these assets are protected by cloud-hosted firewalls. Furthermore, the firewall vendor, not the customer, configures, maintains, and updates cloud-hosted firewalls.
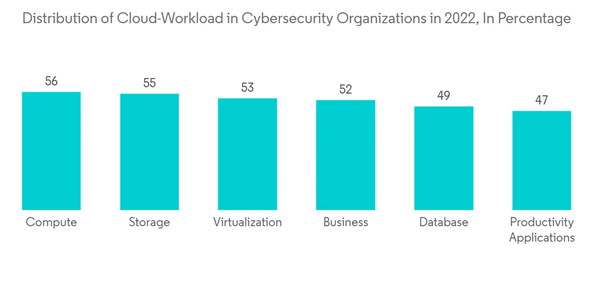
- According to Fortinet's Cloud Security Report last year, several cybersecurity experts were questioned about the cloud services and workloads that their companies use the most. The top of the list is made up of security services (58%), then computing (56%), storage (55%), and virtualization (53%).
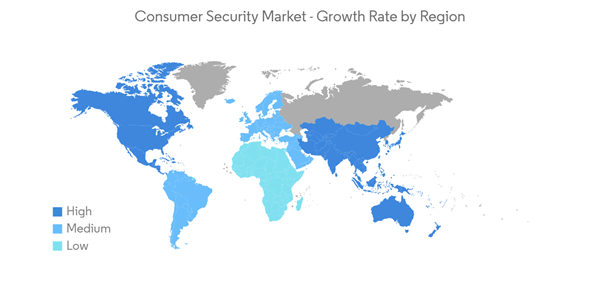
Significant Growth Rate in the Asia-Pacific Region
- The majority of developing economies are found in the APAC area. Due to the region's exponential increase in connected devices, simple PC security and anti-virus software cannot guard against security threats. The growing adoption of network-based technologies, which has led to a tremendous demand for security solutions to defend this network against attacks, is the main factor driving the Asia-Pacific security market.
- The governments of many nations in the region are concentrating on enhancing consumer security and data privacy laws. For instance, the PDP Bill is being worked on by the Indian government to replace the IT Act and related laws. Given that it is currently one of the most data-centric economies, India is working on updating the rules as much as feasible. Significant modifications have been made to India's data privacy legislation, particularly since the passage of the 2021 data protection bill. This is stimulating the market in the nation and the area and providing a chance for security service providers.
- Furthermore, facilitative strategies have been used by Singapore, Japan, South Korea, and Hong Kong. Open API standards and technical specifications, as well as recommendations and suggested standards, may be published by a governmental or commercial standard-setting group. The necessity of security software for data protection is driving the Consumer Security Market in the region.
- By establishing new business hubs, major multinational corporations are growing their operations in the regions, demonstrating the market's potential for expansion. For instance, IBM has opened a new cyber security hub in India. It consists of a cyber range, software development facilities, and a security operations center and would service corporations in the Asia-Pacific region.
- Due to shadow IT, data leakage, and the cloud, Fortinet highlighted that the huge increase in BYOD and BYOA usage among the mobile workforce in Asia Pacific (APAC) exposes corporate networks to more complicated security threats. Employees increasingly anticipate always having their mobile devices with them and having access to the data required to do their jobs from any location. Companies are increasingly letting employees connect to the business network from their own devices to meet these needs, with minimal control over the applications they use. Therefore, with the rapid rise in data safety concerns, there is a huge demand for security services across the region.
Consumer Security Market Competitor Analysis
The Consumer Security Market is at a highly fragmented stage as the market currently consists of many players. Several key players in the Consumer Security Market constantly try to bring advancements. A few prominent companies are entering into collaborations and expanding their footprints in developing regions to consolidate their positions in the market. The major player in this market includes RSA Security, Cisco Systems, IBM Corporation, McAfee, NortonLifeLock Inc, and others.In September 2022, McAfee Corp, a leader in online security worldwide, disclosed the introduction of McAfee+ in Australia. McAfee+ is a new product line that includes all-new identity and privacy protections that let users live their lives online in complete security. Following its debut in the United States, the new McAfee+ product suite is now offered in Australia. It gives customers access to identity restoration, lost wallet support, and award-winning protection against threats and viruses for all their devices.
In January 2022, Avast released a new firewall feature for their free antivirus software. The new Firewall in Avast Free Antivirus protects users from network threats. It is part of the upgrade, reinforcing Avast's commitment to offering advanced and useful security and privacy tools for everyone without charge. For even greater security against data breaches, spoofing attempts, and malicious devices searching for open ports on the user's PC, Avast has incorporated additional sophisticated Firewall features to Avast Premium Security.
Additional benefits of purchasing the report:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
This product will be delivered within 2 business days.