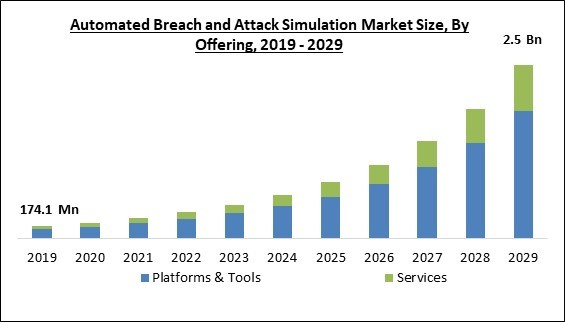
The Global Automated Breach and Attack Simulation Market size is expected to reach $2.5 billion by 2029, rising at a market growth of 31.4% CAGR during the forecast period.
Platforms or systems that automate security assessment by simulating actual attack scenarios are known as automated breach and attack simulation solutions. End users can increase data protection by using these technologies to find security flaws in the current security framework. In addition, ABAS is a computerized method that mimics actual cyberattacks and aids organizations in understanding their security posture & locating potential holes.
The automated breach and attack simulation market is expanding due to the rising complexity of managing security risks and the spike in need for prioritizing security investments. Also, the market for automated breach and assault simulation is expanding favorably as the number of cyberattacks increases globally. On the other hand, it's anticipated that the rise in digitalization initiatives will present lucrative chances for the growth of the automated breach and attack simulation market during the forecast period.
Due to escalating security investments and concerns over compliance with security requirements, the market for automated breach & attack simulation is anticipated to expand globally. By modeling actual attack situations, the automated breach and attack simulation solutions are the platforms or technologies that make it possible to automate security assessment. These solutions enhance data security by assisting users in finding flaws in the current security system.
The volume of industrial data is growing, and there is a growing need for analytics tools and solutions to strengthen organizational security and improve facility operations. These are the main drivers of market growth. The automated breach and simulation solutions can be used to launch automated attacks, frequently utilized to launch unexpected or planned simulated attacks. To launch complex assaults and evaluate the condition of an organization's cybersecurity infrastructure, they have artificial intelligence (AI) and machine learning (ML) capabilities.
COVID-19 Impact Analysis
The COVID-19 outbreak positively affected the expansion of the automated breach and attack simulation market because of these factors: a rise in the popularity of digital solutions; a rise in the threat of cyberattacks from unethical hackers’ trend. Small and medium businesses were encouraged to adopt effective ABAS solutions during the COVID-19 pandemic, which drove the growth of the automated breach and attack simulation (ABAS) market. This has helped to bridge the gap between current security architecture and cyber-attacks that use advanced methods to penetrate organizational resources.
Market Growth Factors
Growing incidence of data breaches rising need for ABAS solutions
Numerous layers of preventive measures should ideally be included in any sound network architecture. The network architecture must have preventive and investigative controls in addition to the former. The majority of cyberattacks cannot be prevented. Despite the firewall's ability to block specific types of traffic from entering the network, preventive techniques may fail to identify and stop such attacks. When harmful or illegal traffic enters the system while evading security measures, the logs may not show that it did so. To detect an impending attack, these harmful entries are not examined. As a result, to recognize and stop such assaults, solid network architecture and automated breach and attack simulation solutions are required.
Growing complexities in managing security threats
Continuous and rapid increases in the digitization of business could be observed globally, increasing the number of application-based solutions. However, no such solutions have resolved all application-related security issues. The simulated platform is effective in resolving the issues and aiding in the system's vulnerability investigation. In addition, once a vulnerability has been identified, developers can readily protect the enterprise system from the identified vulnerabilities. Due to this growing complexity in managing security threats, the need for automated breach and attack simulation solutions arises, leading to market expansion.
Market Restraining Factors
Dearth of skilled professionals
A pricey service is penetration testing. Both service providers & client firms may suffer financial losses if penetration testing is not done correctly. Several employers say there is a scarcity of cybersecurity professionals, and they think this shortfall directly impacts their businesses. This highlights the necessity for proper and better security professional training, which will close the skill gap and produce the necessary competence for locating and assessing cyberattacks. The lack of security professionals could slow the market's expansion.
Offering Outlook
Based on offering, the automated breach and attack simulation market is segmented into platforms & tools, and services. The platforms & tools segment held the highest revenue share in the automated breach and attack simulation market in 2022. This is because cybersecurity providers provide automated breach and attack simulation solutions as a platform. The end-users are encouraged to choose these solutions since they mimic attacks along the entire kill chain and remove any additional danger during continuous upgrades and maintenance.
Deployment Mode Outlook
On the basis of deployment mode, the automated breach and attack simulation market is fragmented into on-premises, and cloud. In 2022, the cloud segment garnered a significant revenue share in the automated break-and-attack simulation market. Organizations are using cloud-based ABAS solutions to reduce costs and increase business agility. Due to its affordability and simplicity, SMEs favor cloud-based implementation. Small businesses can examine vulnerabilities and lessen the threat environment at a far lower cost with the help of the cloud-based deployment of these solutions, boosting their ability to serve customers.
Application Outlook
By application, the automated breach and attack simulation market is divided into configuration management, patch management, threat management and others. The threat management acquired a substantial revenue share in the automated breach and attack simulation market in 2022. Threat intelligence systems gather and analyze data from many sources about the current and emerging threat vectors to produce actionable threat management feeds & reports that different security control solutions can efficiently use. These solutions assist organizations in protecting themselves against the potential occurrences of data breaches by informing them of the hazards of Advanced Persistent Threats (APTs), zero-day assaults, and other similar concerns.
End-user Outlook
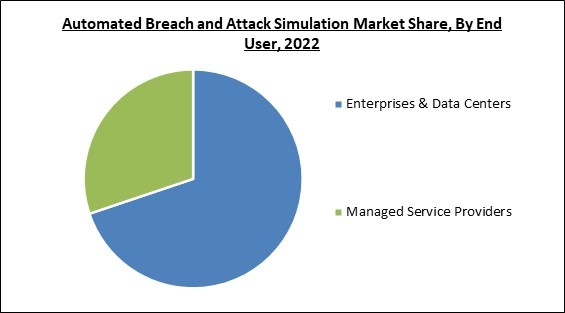
Based on end user, the automated breach and attack simulation market is bifurcated into enterprises & data centers, and managed service providers. In 2022, the enterprise & data centers segment registered the maximum revenue share in the automated breach and attack simulation market. There is still a significant gap in the effectiveness of proactively mitigating new attack vectors despite increasing cybersecurity spending from various end users, and most incidents go unreported or are only partially reported. To combat today's sophisticated cyberattacks, businesses are considering implementing a proactive strategy for breach mitigation.
Growth Drivers
- Growing incidence of data breaches rising need for ABAS solutions
- Growing complexities in managing security threats
Restraints
- Dearth of skilled professionals
Regional Outlook
Region wise, the automated breach and attack simulation market is analyzed across North America, Europe, Asia Pacific and LAMEA. In 2022, the North America region led the automated breach and attack simulation market by generating maximum revenue share. This is due to the fact that it is a technologically advanced region with a significant early adopter population and the presence of key market participants. The expansion of government programs, like smart cities, smart infrastructure, etc., as well as advances surrounding the incorporation of AI and ML in ABASs as well as rising demand for cloud-based ABAS are predicted to fuel the demand for ABAS.
Free Valuable Insights:
The market research report covers the analysis of key stake holders of the market. Key companies profiled in the report include Qualys, Inc., Rapid7, Inc. (IntSights), Sophos Group PLC (Thoma Bravo), Keysight Technologies, Inc., Skybox Security, Inc., NopSec.com, Inc., ReliaQuest, LLC, SCYTHE Inc., CyCognito Ltd. And FireEye, Inc.
Strategies Deployed in Automated Breach and Attack Simulation Market
- Mar-2023: Sophos came into partnership with Cowbell, a provider of cyber risk insurance. Following the partnership, the company would provide small and medium enterprises with streamlined access to cyber insurance coverage and facilitate optimal insurance provision for its customers in the U.S. with opt-in sharing of endpoint health security data.
- Jan-2023: Sophos introduced Sophos Network Detection and Response (NDR) which recognizes rogue assets, insider threats, unprotected devices, and novel attacks for accelerating threat detection and response. Using a combination of machine learning, advanced analytics, and rule-based matching approaches, Sophos NDR continuously monitors network traffic to detect suspicious activities that may be suggestive of attacker activity.
- Jun-2022: ReliaQuest announced an agreement to acquire Digital Shadows, a threat intelligence startup. An end-to-end picture is created for businesses worldwide by combining the internal visibility offered by ReliaQuest with the external threat intelligence and digital risk monitoring offered by Digital Shadows. This is an exceptional opportunity for its clients and partners because of the complementing technical capabilities, shared cultural values, and geographic synergies.
- Mar-2022: Keysight Technologies announced a partnership with SCADAfence for creating a new concept called 'Virtual BAS Agents'. Because of this, security teams may simulate assaults on the IT-OT boundary in a secure and non-intrusive manner.
- Mar-2022: Keysight Technologies launched Breach Defense, a security operations (SecOps) platform created for improving operational security effectiveness. The new platform Threat Simulator breach and attack simulation solution allows network and security operations teams to securely model the most recent assaults and exploits on live networks to assess the effectiveness of operational security. Keysight's Threat Simulator offers both practical assistance for patching vulnerabilities and real-time threat intelligence.
- Jan-2022: ReliaQuest opened a new office in Pune, Maharashtra. The expansion would provide the company with quality technical talent for continuously creating and providing an OpenXDR platform, which would help the security operators in becoming more efficient and proactive with their security posture.
- Sep-2020: ReliaQuest signed a partnership with Tampa Bay Buccaneers that comprises its designation as the team’s Official Cybersecurity Partner. Through this partnership, ReliaQuest's GreyMatter platform will be able to help the Buccaneers defend against security breaches by giving them unmatched visibility into potential threats and the on-demand automation capabilities to proactively respond and continuously validate the team's security over time.
- Jun-2019: ReliaQuest announced the launch of GreyMatter, a first-of-its-kind, integrated platform that integrates disparate processes, technologies, and teams for delivering greater control and visibility of enterprise security operations. GreyMatter proactively identifies and addresses cybersecurity threats across an organization using a combination of machine learning and human analysis so that security teams can mobilize more quickly and efficiently.
Scope of the Study
By Offering
- Platforms & Tools
- Services
By Deployment Mode
- On-premise
- Cloud
By End-user
- Enterprises & Data Centers
- Managed Service Providers
By Application
- Configuration Management
- Threat Management
- Patch Management
- Others
By Geography
- North America
- US
- Canada
- Mexico
- Rest of North America
- Europe
- Germany
- UK
- France
- Russia
- Spain
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Singapore
- Malaysia
- Rest of Asia Pacific
- LAMEA
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Key Market Players
List of Companies Profiled in the Report:
- Qualys, Inc.
- Rapid7, Inc. (IntSights)
- Sophos Group PLC (Thoma Bravo)
- Keysight Technologies, Inc.
- Skybox Security, Inc.
- NopSec.com, Inc.
- ReliaQuest, LLC
- SCYTHE Inc.
- CyCognito Ltd.
- FireEye, Inc.
Unique Offerings
- Exhaustive coverage
- The highest number of Market tables and figures
- Subscription-based model available
- Guaranteed best price
- Assured post sales research support with 10% customization free
Table of Contents
Companies Mentioned
- Qualys, Inc.
- Rapid7, Inc. (IntSights)
- Sophos Group PLC (Thoma Bravo)
- Keysight Technologies, Inc.
- Skybox Security, Inc.
- NopSec.com, Inc.
- ReliaQuest, LLC
- SCYTHE Inc.
- CyCognito Ltd.
- FireEye, Inc.