The Encryption Software Market Study provides a comprehensive analysis of the global encryption software market, focusing on key trends, market dynamics, and competitive intelligence. This study is designed for industry experts seeking actionable insights into market opportunities, technological advancements, and strategic developments. It covers applications, deployment models, enterprise sizes, end-user industries, and geographic regions, offering a detailed perspective on the factors shaping the market's growth trajectory.
Study Overview
The Encryption Software Market Study examines the evolving landscape of encryption software, driven by increasing cybersecurity threats, regulatory compliance requirements, and the adoption of cloud-based solutions. The study segments the market by application (cloud, database, disk, communication, and file/folder encryption), deployment model (on-premise and cloud), enterprise size (small, medium, and large), and end-user industries (BFSI, government, manufacturing, communication and technology, retail, healthcare, and others). It also provides a geographic analysis covering North America, South America, Europe, the Middle East and Africa, and Asia Pacific. The research methodology integrates primary and secondary data sources, ensuring robust and reliable insights for industry stakeholders.Competitive Environment and Analysis
In the Encryption Software Market Study, the competitive intelligence section highlights key developments from major players shaping the market. For instance,Microsoft Corporation
has advanced its encryption offerings through Azure's confidential computing capabilities, integrating hardware-based trusted execution environments to enhance data security during processing. This development strengthens Microsoft’s position in cloud encryption, catering to enterprises prioritizing data privacy in hybrid cloud environments. Similarly,Thales Group
has expanded its portfolio with the launch of advanced key management solutions, such as the CipherTrust Data Security Platform, which unifies encryption and access control for multi-cloud environments. These innovations underscore the competitive strategies of major players to address evolving security demands. The study also evaluates emerging players, mergers, acquisitions, and collaborations, alongside a vendor competitiveness matrix to provide a holistic view of the market's competitive dynamics.Conclusion
The Encryption Software Market Study offers industry experts a detailed roadmap to navigate the rapidly evolving encryption software landscape. By analyzing market drivers, restraints, and strategic developments from key players like Microsoft and Thales, the study equips stakeholders with the insights needed to capitalize on growth opportunities and address competitive challenges. This research serves as an essential resource for decision-makers aiming to stay ahead in the dynamic encryption software market.Key Benefits of this Report:
- Insightful Analysis: Gain detailed market insights covering major as well as emerging geographical regions, focusing on customer segments, government policies and socio-economic factors, consumer preferences, industry verticals, and other sub-segments.
- Competitive Landscape: Understand the strategic maneuvers employed by key players globally to understand possible market penetration with the correct strategy.
- Market Drivers & Future Trends: Explore the dynamic factors and pivotal market trends and how they will shape future market developments.
- Actionable Recommendations: Utilize the insights to exercise strategic decisions to uncover new business streams and revenues in a dynamic environment.
- Caters to a Wide Audience: Beneficial and cost-effective for startups, research institutions, consultants, SMEs, and large enterprises.
What do businesses use our reports for?
Industry and Market Insights, Opportunity Assessment, Product Demand Forecasting, Market Entry Strategy, Geographical Expansion, Capital Investment Decisions, Regulatory Framework & Implications, New Product Development, Competitive IntelligenceReport Coverage:
- Historical data from 2022 to 2024 & forecast data from 2025 to 2030
- Growth Opportunities, Challenges, Supply Chain Outlook, Regulatory Framework, and Trend Analysis
- Competitive Positioning, Strategies, and Market Share Analysis
- Revenue Growth and Forecast Assessment of segments and regions including countries
- Company Profiling (Strategies, Products, Financial Information, and Key Developments among others).
Different segments covered under the encryption software market report are as below:
By Application
- Cloud Encryption
- Database Encryption
- Disk Encryption
- Communication Encryption
- File/Folder Encryption
By Deployment Model
- On-premise
- Cloud
By Enterprise Size
- Small
- Medium
- Large
By End-User
- BFSI
- Government
- Manufacturing
- Communication and Technology
- Retail
- Healthcare
- Others
By Geography
- North America
- United States
- Canada
- Mexico
- South America
- Brazil
- Argentina
- Others
- Europe
- United Kingdom
- Germany
- France
- Spain
- Others
- Middle East and Africa
- Saudi Arabia
- UAE
- Israel
- Others
- Asia Pacific
- Japan
- China
- India
- South Korea
- Indonesia
- Thailand
- Others
Table of Contents
Companies Mentioned
- International Business Machines Corporation
- Microsoft Corporation
- Broadcom Inc.
- Sophos Ltd.
- Thales Group
- Trend Micro Incorporated
- Dell Technologies Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 140 |
| Published | July 2025 |
| Forecast Period | 2025 - 2030 |
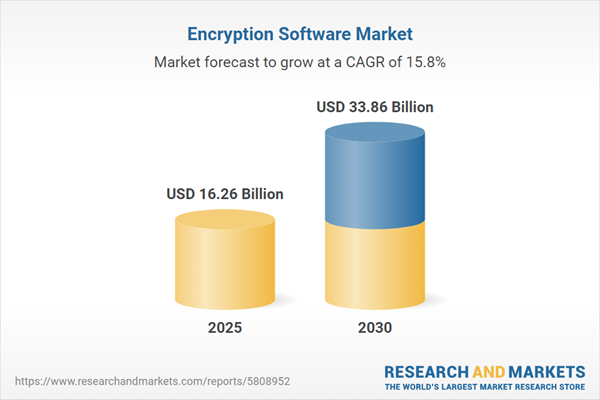
| Estimated Market Value ( USD | $ 16.26 Billion |
| Forecasted Market Value ( USD | $ 33.86 Billion |
| Compound Annual Growth Rate | 15.8% |
| Regions Covered | Global |
| No. of Companies Mentioned | 9 |