Speak directly to the analyst to clarify any post sales queries you may have.
An essential orientation to why centralized and policy-driven key management is now critical for resilient enterprise data protection strategies
Key Management as a Service (KMaaS) has become a foundational element for organizations that must protect sensitive data across cloud and on-premises environments. As cryptographic requirements evolve, enterprises are moving from ad hoc key handling toward centralized, policy-driven control of encryption keys, yielding stronger governance and operational consistency. This shift is driven by a confluence of regulatory expectations, digital transformation programs, and the growing diversity of environments where sensitive data resides.
The introduction frames the strategic stakes of adopting robust key management solutions: reducing exposure from misconfigured key lifecycles, enforcing separation of duties, and enabling secure data mobility across hybrid estates. Decision-makers should view KMaaS not simply as a technical control but as a risk management capability that integrates with identity, access management, and broader security operations. In practice, this means aligning cryptographic policies with business processes and compliance requirements, while maintaining the agility needed for rapid development and cloud-native deployments.
Throughout this report, emphasis is placed on pragmatic design choices that reconcile security objectives with operational realities. The introduction sets expectations for subsequent sections by underscoring interoperability, auditability, and the importance of vendor-transparent key custody models. Ultimately, the case for KMaaS centers on reducing cryptographic risk while enabling secure innovation across modern IT landscapes.
How converging forces of cloud-native architectures, hardware-backed trust, and evolving managed models are reshaping enterprise key management practices
The landscape for cryptographic key management is undergoing transformative shifts as organizations contend with increasingly heterogenous IT environments and elevated regulatory scrutiny. Cloud-native architectures and microservices have accelerated the adoption of dynamic key usage patterns, prompting a move away from static, locally stored keys toward service-based key lifecycle management. This transition supports rapid application deployment while demanding robust automation and policy enforcement to prevent configuration drift and human error.
Concurrently, the rise of confidential computing and hardware-backed isolation technologies is reshaping expectations for root-of-trust guarantees. Enterprises are evaluating combinations of cloud key management services, virtual HSMs, and physical HSMs to match workload requirements and threat models. As a result, integration capabilities, standards compliance, and clear delineation of key custody responsibilities have become decisive procurement criteria. In parallel, managed service models are evolving to offer varying degrees of exclusivity and shared tenancy, enabling organizations to choose higher control or more cost-efficient models based on risk appetite.
These shifts are reinforcing the need for interoperable key management frameworks that support hybrid and multi-cloud strategies while preserving audit trails and compliance artifacts. Organizations that adapt by codifying cryptographic policies, investing in automation, and selecting flexible key custody options will be better positioned to maintain data confidentiality and operational continuity amid rapid technological change.
How 2025 tariff-driven changes in hardware costs and supply chains are altering procurement strategies and accelerating cloud-first custody alternatives
The cumulative impact of United States tariffs implemented in 2025 has introduced new considerations for procurement, supply chains, and deployment architectures within cryptographic infrastructure. Tariff-related increases in the cost of imported hardware, including physical hardware security modules and specialized cryptographic components, have led organizations to reassess where and how they source key management appliances and associated trust anchors. Procurement teams are increasingly factoring total cost of ownership implications into decisions about on-premises HSM purchases versus cloud-based or virtualized alternatives.
In response, some enterprises have accelerated adoption of virtual HSMs and cloud-native key management capabilities to mitigate exposure to hardware cost fluctuations and supply delays. This trend has been accompanied by renewed focus on vendor diversification, local sourcing, and partnerships with regional manufacturers to reduce single-source dependency. At the same time, managed service providers that maintain localized inventory and offer dedicated managed service options are gaining attention for their capacity to absorb procurement volatility and preserve service continuity.
Operationally, the tariffs have reinforced the strategic value of flexible deployment models that permit workload mobility between cloud, hybrid, and on-premises environments. Security teams are prioritizing design patterns that enable migration of key custody without compromising cryptographic integrity, thereby maintaining resilience against supply chain and geopolitical disruptions. As a result, procurement strategies are now evaluated not only on price and feature sets, but on supply chain robustness and the ability to support long-term cryptographic stewardship.
A multidimensional segmentation analysis revealing how offering types, deployment choices, key categories, enterprise scale, and vertical demands shape adoption and design
A nuanced segmentation framework reveals where capabilities and adoption patterns diverge across the key management ecosystem. Based on offering type, the market distinguishes between Cloud KMS, Hardware Security Module, and Managed Service. Cloud KMS further differentiates into hybrid cloud, private cloud, and public cloud implementations, reflecting varied operational models and trust boundaries. Hardware Security Module options split into physical HSM appliances and virtual HSM instances, each serving different assurance and scalability needs. Managed Service offerings range from dedicated managed service engagements to shared managed service arrangements, aligning with differing control and cost priorities.
Deployment model segmentation separates cloud, hybrid, and on-premises approaches. The hybrid category itself bifurcates into multi-cloud hybrid and single-cloud hybrid patterns, signifying whether organizations maintain distributed relationships with multiple cloud providers or anchor primarily with one. Key type segmentation clarifies whether cryptographic workloads rely predominantly on asymmetric or symmetric keys, which shapes algorithm support, lifecycle procedures, and performance considerations. Enterprise size segmentation contrasts large enterprises with small and medium enterprises, highlighting contrasts in governance maturity, in-house security resources, and procurement scale.
Industry vertical segmentation surfaces unique functional demands across sectors such as BFSI, government and defense, healthcare, IT and telecom, and retail and e-commerce. These vertical contexts drive differentiated compliance drivers, performance constraints, and integration priorities. Synthesizing these segmentation lenses shows that architectural design and sourcing decisions must be purposefully matched to regulatory profiles, operational tempo, and risk tolerance to deliver effective and sustainable key management outcomes.
How regional regulatory nuance, supply chain resilience, and cloud adoption patterns differentiate implementation priorities across global markets
Regional dynamics exert a powerful influence on implementation approaches, vendor ecosystems, and regulatory expectations. In the Americas, strong demand for cloud-native services coexists with an established installed base of on-premises HSM deployments, prompting hybrid strategies that balance agility with control. Security and compliance teams in this region emphasize alignment with domestic regulatory frameworks while also negotiating cross-border data flows for multinational operations.
Across Europe, Middle East & Africa, regulatory complexity and diverse national requirements necessitate careful attention to data residency, auditability, and standards alignment. Organizations in this region frequently seek vendors that can demonstrate localized support and compliance assurances, and they often prioritize solutions that facilitate strict separation of duties and auditable key custody. In contrast, Asia-Pacific displays both rapid cloud adoption and strong interest in localized manufacturing and supply chain resilience, particularly in markets that have prioritized sovereign technology initiatives.
Taken together, these regional variations underscore that a one-size-fits-all approach is impractical. Successful programs account for regional regulatory nuance, local supplier ecosystems, and the geopolitical drivers that inform procurement and architecture decisions. Firms that embed regional considerations into vendor selection, deployment topology, and operational playbooks will achieve smoother implementations and more sustainable cryptographic governance.
How vendor strategies and customer selection criteria are converging around interoperability, managed service flexibility, and standards-based trust models
Corporate participants and vendors within the key management space are demonstrating differentiated strategies to address modern cryptographic needs. Leading providers emphasize interoperability with cloud platforms and identity systems, while investing in modular architectures that support hybrid deployment and seamless key migration. A notable pattern is the emergence of stronger managed service portfolios that allow customers to choose between shared tenancy for cost efficiency and dedicated managed services for higher assurance and control.
Strategic partnerships have become a hallmark of vendor approaches, with collaborations formed to integrate HSM capabilities into broader security stacks and to embed key management into developer workflows. Product roadmaps are increasingly guided by standards convergence, including support for open key management protocols and hardware-backed attestation features that facilitate secure remote provisioning. Market participants are also prioritizing transparent key custody models and audit capabilities to address governance and compliance questions from enterprise buyers.
From the customer perspective, organizations are focusing on proof-of-concept work that validates integration, performance, and auditability before committing to wide-scale deployments. As a result, vendors that provide robust sandbox environments, clear migration pathways, and strong professional services support are positioned to earn trust and long-term relationships with enterprise clients.
Practical steps for leaders to align governance, architectural flexibility, and operational readiness to reduce cryptographic risk and enable secure innovation
Industry leaders should adopt a pragmatic, phased approach to strengthening key management capabilities that aligns risk appetite with operational realities. Start by codifying cryptographic policy and governance constructs, ensuring that lifecycle procedures, roles, and audit requirements are explicit and measurable. Once governance is established, prioritize integration with identity and access management and automation tooling to reduce manual intervention and the risk of human error.
When selecting solutions, evaluate options through a risk-adjusted lens that considers both technical assurance and supply chain robustness. For organizations facing increased hardware procurement volatility, consider hybrid mixes that leverage virtual HSMs and cloud KMS for elasticity, with targeted physical HSMs reserved for the highest-assurance workloads. Additionally, negotiate clear service-level commitments and escrow or portability provisions to preserve operational continuity and key access rights.
Finally, invest in internal capability building through targeted training for cryptography owners and security operations personnel, and establish continuous validation programs that exercise key rotation, backup, and recovery processes. By combining policy clarity, architectural flexibility, and operational readiness, leaders can reduce cryptographic risk while enabling secure innovation across the enterprise.
A rigorous mixed-methods approach integrating practitioner interviews, technical validation, and scenario analysis to produce actionable guidance without relying on numerical projections
This research synthesizes primary interviews with security architects, procurement leads, and managed service operators, supplemented by secondary analysis of technical standards, regulatory guidance, and public vendor documentation. Qualitative insights were prioritized to capture real-world trade-offs and procurement behaviors, while technical comparisons focused on feature parity, integration pathways, and assurance models rather than pricing or volumetric estimates.
Data collection emphasized diversity of perspective across enterprise sizes, verticals, and regional markets to surface practical considerations for hybrid and multi-cloud contexts. Case studies and proof-of-concept outcomes were used to validate vendor claims related to interoperability, migration support, and audit artifact generation. The methodology also incorporated scenario-based assessments to understand resilience strategies against supply chain disruptions and shifts in hardware availability.
Throughout the research process, findings were cross-validated with independent technical reviews and operational practitioners to ensure accuracy and relevance. The resulting analysis prioritizes actionable guidance and comparative understanding to inform procurement, architecture, and governance decisions without relying on numeric market projections.
Concluding synthesis that positions policy-driven lifecycle control, hybrid flexibility, and supply chain resilience as the pillars of sustainable key management programs
In conclusion, effective key management has evolved into a strategic imperative that intersects security, compliance, procurement, and cloud architecture. Organizations that treat cryptographic controls as integral to enterprise risk management will be better equipped to protect sensitive data, support regulatory obligations, and enable secure digital transformation. Central themes emerging from the analysis include the importance of policy-driven lifecycle management, flexibility across hybrid and multi-cloud topologies, and resilience against supply chain and procurement disruptions.
Progress requires coordination across governance, architecture, and operational domains, with emphasis on automation, auditability, and standards-based integration. Leaders should prioritize capability building, rigorous vendor validation, and contractual protections that preserve key portability and continuity. By doing so, enterprises can achieve a balance between assurance and agility, enabling secure innovation without compromising foundational protections for cryptographic assets.
Ultimately, the path forward involves disciplined implementation, continual validation, and strategic sourcing choices that reflect both technical requirements and geopolitical realities, positioning organizations to meet current obligations and adapt to future challenges.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
17. China Key Management as a Service Market
Companies Mentioned
The key companies profiled in this Key Management as a Service market report include:- Amazon Web Services, Inc.
- Entrust Corporation
- Fortanix, Inc.
- Google LLC
- HashiCorp, Inc.
- IBM Corporation
- Microsoft Corporation
- Oracle Corporation
- Thales Group
- Venafi, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 195 |
| Published | January 2026 |
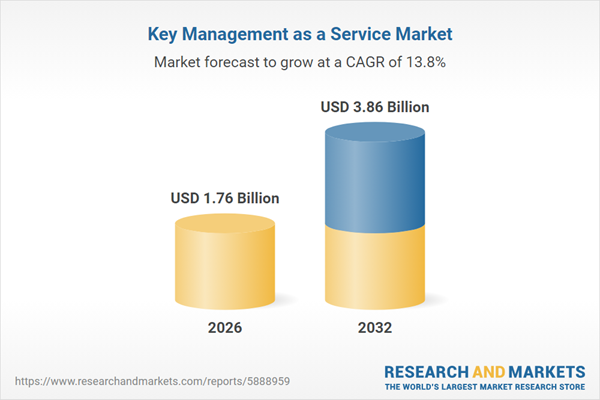
| Forecast Period | 2026 - 2032 |
| Estimated Market Value ( USD | $ 1.76 Billion |
| Forecasted Market Value ( USD | $ 3.86 Billion |
| Compound Annual Growth Rate | 13.7% |
| Regions Covered | Global |
| No. of Companies Mentioned | 11 |