Speak directly to the analyst to clarify any post sales queries you may have.
A compelling strategic introduction that outlines why multifactor authentication sits at the nexus of cybersecurity, compliance, and digital transformation imperatives
Multifactor authentication has moved from a recommended control to an operational imperative as organizations contend with escalating credential-based threats and complex compliance demands. The introduction sets the stage by mapping how identity, access, and user verification now serve as foundational elements of enterprise risk management and digital transformation strategies. Given rapid advances in mobile computing, remote work, and cloud migration, authentication architectures must reconcile user experience with robust security controls to protect sensitive assets and preserve business continuity.This introduction frames the central themes that will be examined across the report: evolving threat vectors that target single-factor weaknesses, the operational trade-offs between friction and protection, and the integration challenges that security and IT teams face when deploying multifactor solutions across distributed environments. It also underscores how multifactor authentication contributes to broader resilience objectives by reducing the likelihood of lateral movement following initial compromise and by enabling stronger policy enforcement for high-value transactions. In setting expectations, the section outlines key drivers for adoption, the role of standards and regulatory drivers in shaping design choices, and the ways in which technology selection affects long-term manageability and total cost of ownership.
An in-depth exploration of the transformative technological and operational shifts reshaping authentication strategies across cloud, mobile, and enterprise environments
The authentication landscape is undergoing transformative shifts driven by both technological maturation and changing user behavior. First, biometric methods and cryptographic hardware tokens have become more practical at scale, prompting a shift from knowledge-based factors toward possession- and inherence-based approaches. Second, the move to cloud-native identity platforms and decentralized trust models has accelerated, enabling continuous and contextual authentication that adjusts risk decisions in real time rather than relying solely on static credentials. These dynamics are altering how enterprises architect identity systems, pushing teams to adopt adaptive mechanisms that assess device posture, geolocation, and behavioral signals alongside traditional factors.Concurrently, regulatory expectations and industry best practices are converging on stronger authentication for sensitive transactions, which in turn has encouraged broader adoption of standards such as FIDO and OAuth-derived flows. This confluence is fostering interoperability and vendor consolidation in some segments, while also opening opportunities for innovative providers that can deliver seamless UX without compromising security. Ultimately, these shifts are prompting organizations to rethink authentication as a distributed security service-one that must integrate with endpoint management, threat intelligence, and access governance-so that controls remain effective across hybrid IT estates and evolving attack techniques.
A comprehensive analysis of how shifting United States tariff policies in 2025 influence procurement, supply resilience, and strategic sourcing of authentication hardware and services
Policy shifts and tariff decisions can exert material influence on the supply chains that underpin hardware-based and tokenized authentication solutions. The introduction of new or adjusted duties affects sourcing strategies, procurement cycles, and vendor selection, particularly for organizations that rely on devices or secure elements produced in specific geographies. In response, buyers and solution architects are increasingly emphasizing modular architectures that decouple core authentication logic from location-sensitive components, thereby preserving continuity even when discrete hardware elements face pricing or availability pressures.As trade dynamics evolve, vendors with diverse manufacturing footprints and those able to shift production to alternate regions gain a relative advantage. Procurement teams consequently place greater emphasis on supplier resilience, dual-sourcing strategies, and contractual mechanisms that mitigate cost volatility. From a deployment perspective, software-centric and cloud-native authentication services can partially insulate organizations from tariffs that primarily affect physical tokens and secure hardware. Nevertheless, enterprises that require hardware-backed assurances-such as government agencies or regulated financial firms-must weigh tariff exposure as part of their sourcing and lifecycle management strategies to maintain compliance and service levels.
A nuanced set of segmentation insights revealing how model choice, organization scale, deployment preferences, and industry verticals determine authentication priorities and trade-offs
Segmentation analysis highlights differentiated adoption patterns and design priorities across authentication capabilities, organization sizes, deployment modes, and industry verticals. Based on model, the market is studied across five-factor authentication, four-factor authentication, three-factor authentication, and two-factor authentication; organizations focused on high-assurance use cases prioritize multi-factor stacks that combine possession, inherence, and contextual signals, whereas broader consumer-facing services often balance usability and risk by favoring two- or three-factor constructs. This diversity in model choice guides solution requirements, vendor selection criteria, and integration complexity, with higher-factor approaches necessitating tighter lifecycle management for credentials and more robust recovery paths.Based on organization size, the market is studied across large enterprises and SMEs; larger organizations typically adopt centralized identity orchestration, invest in custom integrations with privileged access management and identity governance systems, and maintain dedicated teams for continuous monitoring and policy tuning. In contrast, SMEs emphasize turnkey, cloud-delivered offerings that minimize operational overhead and accelerate time to protection. Based on deployment mode, the market is studied across cloud and on premise; cloud deployments accelerate rollout and reduce hardware dependency, while on-premise choices persist where regulatory constraints or legacy ecosystems demand local control. Finally, based on vertical, the market is studied across BFSI, government, healthcare, IT and telecom, and retail; each vertical emphasizes different authentication assurances-BFSI and government demand the highest levels of assurance and auditability, healthcare prioritizes patient privacy and clinical workflow compatibility, IT and telecom focus on scalable machine-to-machine trust, and retail balances strong authentication with rapid, low-friction consumer checkout experiences.
Taken together, these segmentation lenses reveal how technical, organizational, and regulatory contours shape solution roadmaps and procurement cycles. They also highlight the need for flexible licensing models, adaptive policy engines, and rigorous vendor performance metrics to ensure that chosen approaches remain aligned with evolving risk tolerances and operational realities.
Key regional perspectives that explain how regulatory pressure, cloud adoption, and cultural factors drive differentiated authentication strategies across major global regions
Regional dynamics exert a meaningful influence on strategy, regulation, and vendor ecosystems, producing distinct adoption patterns across geographies. Across the Americas, investments emphasize integration with large cloud providers, widespread adoption of mobile-first authentication experiences, and a strong commercial ecosystem for identity startups and managed service providers. Regulatory drivers in specific jurisdictions also push enterprises toward stronger authentication for financial and healthcare transactions, while regional innovation hubs accelerate pilot programs for passwordless flows and biometric convergence. Consequently, organizations in this region prioritize scalability, partner ecosystems, and solutions that integrate seamlessly with dominant cloud and collaboration platforms.In Europe, Middle East & Africa, compliance frameworks such as the GDPR family and sector-specific mandates elevate data protection and transparency requirements, which in turn influence architecture choices and consent flows. Public sector procurement in several countries demands high-assurance credentials and local data residency, encouraging a mix of cloud and on-premise deployments. Meanwhile, localized vendor ecosystems and multinational compliance considerations shape procurement and integration patterns. In the Asia-Pacific region, rapid digital adoption and large-scale government initiatives to digitize services drive demand for versatile authentication mechanisms that support both consumer and enterprise use cases. High mobile penetration and diversified device ecosystems push vendors to optimize cross-platform interoperability and support a broad range of biometric and tokenized methods. Taken together, these regional considerations require vendors and buyers to tailor solutions to local regulatory, cultural, and infrastructural realities while preserving global management capabilities.
A critical examination of competitive behaviors and vendor strategies highlighting product differentiation, partner ecosystems, and attributes that drive enterprise trust and adoption
Leading vendors and ecosystem participants demonstrate divergent approaches to productization, channel strategy, and partnership orchestration. Some companies concentrate on end-to-end authentication suites that bundle device-based keys, biometric verification, and contextual risk engines into unified platforms that appeal to large enterprises seeking centralized control. Others specialize in modular components-such as FIDO-compliant authenticators or risk scoring services-that integrate via standardized APIs into broader identity stacks, enabling faster deployment and best-of-breed architectures.Channel and partner strategies also matter: organizations that cultivate strong alliances with cloud hyperscalers, managed security service providers, and systems integrators are more successful at scaling deployments across heterogeneous estates. Additionally, research indicates that vendors who invest in developer-centric tooling, comprehensive documentation, and SDKs reduce friction for integrators and accelerate adoption. Finally, companies that prioritize transparent privacy practices, clear recovery mechanisms, and compliance-ready audit trails earn greater trust among regulated customers, driving long-term retention and deeper contractual commitments.
Actionable recommendations for executives and security leaders to operationalize adaptive authentication, reinforce supplier resilience, and measure program performance
Leaders must take decisive steps to align authentication strategies with broader security and business objectives. First, they should adopt an adaptive authentication framework that incorporates device posture, user behavior analytics, and transaction context to raise assurance where risk dictates while preserving low-friction access for routine tasks. Second, executives should prioritize investments in standards-based approaches, favoring open protocols and hardware-backed credentials to avoid vendor lock-in and to enable future interoperability. By doing so, organizations maintain the flexibility to integrate advanced factors as needs change without costly rip-and-replace initiatives.Moreover, procurement and security teams should strengthen supplier resilience through diversified sourcing and contractual protections that address potential tariff and supply chain disruptions. They should also institutionalize lifecycle processes for credential issuance, revocation, and recovery, ensuring operational readiness for large-scale rollouts. Finally, organizations should incorporate continuous measurement-using operational metrics that reflect authentication failure rates, friction impact on productivity, and incident reduction-to guide iterative improvements and to communicate the program’s value to leadership and stakeholders.
A transparent research methodology combining practitioner interviews, technical assessments, and standards analysis to produce verifiable and operationally relevant findings
The research underpinning this analysis combines qualitative interviews, technical evaluations, and comparative product reviews to ensure balanced and practical insights. Primary engagement included structured conversations with security leaders, identity architects, and procurement specialists to capture real-world deployment challenges and decision criteria. Complementing these engagements, technical assessments reviewed protocol support, interoperability characteristics, and security controls across representative solutions to evaluate how designs perform under diverse operational constraints.To ensure objectivity, secondary research drew on regulatory texts, standards body publications, and vendor documentation to map compliance implications and architectural patterns. Comparative analysis focused on feature parity, integration ease, and operational considerations rather than on unit economics or market sizing. Throughout, findings were validated through cross-referencing multiple sources and by soliciting practitioner feedback to refine recommendations and to surface pragmatic adoption pathways for different organization profiles.
A succinct conclusion emphasizing that adaptive, standards-driven multifactor authentication is essential to sustain security, compliance, and digital trust
In closing, multifactor authentication represents a pragmatic convergence of security, usability, and regulatory alignment that organizations cannot afford to postpone. The technology and operational best practices described across this report illustrate a clear path: adopt adaptive, standards-based approaches; prioritize supplier and supply-chain resilience; and measure program outcomes to maintain momentum and justify continued investment. As threat actors refine credential-based tactics, a layered approach to authentication will remain a cornerstone of effective cyber defense.Moving forward, decision-makers should treat authentication as an evolving capability that requires ongoing tuning, cross-functional governance, and proactive integration with broader identity and access management disciplines. By doing so, organizations will strengthen their posture against common attack vectors, support regulatory compliance, and enable secure digital experiences that underpin business growth and trust.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
16. China Multi-factor Authentication Market
Companies Mentioned
The key companies profiled in this Multi-factor Authentication market report include:- Broadcom Inc
- Cisco Systems Inc
- CyberArk Software Ltd
- Entrust Corporation
- Fujitsu Group
- Google LLC
- HID Global Corporation
- IBM Corporation
- LastPass
- ManageEngine
- Microsoft Corporation
- NEC Corporation
- Okta Inc
- OneSpan Inc
- Oracle Corporation
- Ping Identity Corporation
- RSA Security LLC
- Salesforce
- Secret Double Octopus
- SecureAuth Corporation
- SecureEnvoy Limited
- Silverfort
- Thales Group
- WatchGuard Technologies
- Yubico AB
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 193 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
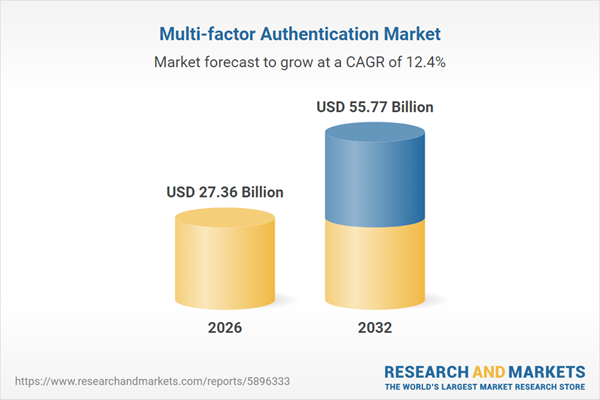
| Estimated Market Value ( USD | $ 27.36 Billion |
| Forecasted Market Value ( USD | $ 55.77 Billion |
| Compound Annual Growth Rate | 12.4% |
| Regions Covered | Global |
| No. of Companies Mentioned | 26 |