Speak directly to the analyst to clarify any post sales queries you may have.
10% Free customizationThis report comes with 10% free customization, enabling you to add data that meets your specific business needs.
Highlighted by ISACA in 2024, 58% of cybersecurity professionals believed their organizations were susceptible to a cyberattack within the year, a statistic that underscores the urgent need for robust data protection mechanisms like EKM. Despite this demand, market expansion faces a substantial hurdle due to the operational complexity of these systems, a problem worsened by a global scarcity of skilled personnel qualified to manage complex encryption lifecycles.
Market Drivers
The rising frequency and sophistication of global cyberattacks are forcing organizations to implement enterprise key management (EKM) solutions to limit financial exposure and protect critical infrastructure. Because attackers frequently target cryptographic assets to decrypt sensitive data, automating key lifecycles is crucial for minimizing the impact of potential breaches. According to IBM’s 'Cost of a Data Breach Report 2024' released in July 2024, the global average cost of a data breach hit USD 4.88 million, emphasizing the need for stronger encryption strategies to reduce liability. Consequently, firms are adopting EKM to ensure stolen data is rendered useless through cryptographic erasure and access revocation, keeping compromised information unintelligible to unauthorized users.Additionally, the rapid migration to cloud, hybrid, and multi-cloud computing environments is fundamentally changing how encryption keys are provisioned, serving as a secondary catalyst for the market. As enterprises distribute workloads, they face the difficulty of harmonizing fragmented security policies across various platforms, necessitating centralized key management systems to retain sovereignty over cloud-hosted data. Thales’s '2024 Cloud Security Study' from June 2024 notes that 47% of corporate data in the cloud is sensitive, creating a major operational challenge regarding consistent encryption management. Furthermore, the Identity Theft Resource Center reported in 2024 that data compromises in the United States jumped to 3,205 during the previous year, highlighting the critical need for scalable EKM frameworks capable of addressing evolving threat landscapes.
Market Challenges
The growth of the Global Enterprise Key Management Market is significantly hindered by operational complexity combined with a persistent shortage of skilled professionals. As encryption environments grow more intricate due to the adoption of hybrid cloud systems, the demand for specialized talent to handle cryptographic key lifecycles increases. Many organizations struggle to effectively deploy centralized key management solutions due to a lack of in-house expertise required to navigate these dense technical systems. This skills gap compels enterprises to delay implementation schedules or reduce the scope of security initiatives, directly slowing market adoption and growth rates.The scale of this workforce deficit is profound and continues to limit the industry's potential. According to ISC2 in 2024, the global cybersecurity workforce gap expanded to 4.8 million unfilled roles. This severe shortage indicates that numerous organizations lack the necessary human capital to securely operate complex key management infrastructures. As a result, the inability to find qualified personnel prevents businesses from fully integrating robust encryption standards, thereby stifling the overall momentum of the enterprise key management sector.
Market Trends
The integration of Post-Quantum Cryptography (PQC) algorithms is transforming the market as organizations rush to future-proof their encryption standards against quantum computing threats. This trend is largely fueled by the "harvest now, decrypt later" risk, where attackers steal encrypted data today with the intent of unlocking it once quantum processors become powerful enough. Enterprises are actively auditing their cryptographic agility and incorporating quantum-resistant algorithms into their security roadmaps to protect long-term intellectual property. The urgency of this shift is evident in Entrust’s '2024 PKI and Post-Quantum Trends Study' from October 2024, which found that 61% of global respondents intend to migrate to post-quantum cryptography within five years, indicating a major strategic move to overhaul legacy encryption infrastructures before vulnerabilities escalate.Simultaneously, incorporating key management into DevSecOps pipelines is becoming essential as cloud-native applications grow in complexity. In modern microservices architectures, the number of machine identities - such as keys for containers, APIs, and service accounts - vastly exceeds human identities, creating management blind spots that manual methods cannot resolve. Automated key orchestration embedded within CI/CD workflows ensures that ephemeral cryptographic assets are generated and rotated without slowing development speeds. The critical need for this integration is highlighted by Venafi’s December 2024 report, 'The Impact of Machine Identities on the State of Cloud Native Security in 2024', which noted that 56% of organizations faced a security incident related to machine identities in the past year, underscoring the demand for pipeline-integrated controls.
Key Players Profiled in the Enterprise Key Management Market
- Microsoft Corporation
- Amazon.com, Inc.
- RSA Security LLC
- CyberArk Software Ltd.
- Broadcom, Inc.
- Venafi, Inc.
- DigiCert, Inc.
- Protegrity USA, Inc.
- A10 Networks, Inc.
- Delinea Inc.
Report Scope
In this report, the Global Enterprise Key Management Market has been segmented into the following categories:Enterprise Key Management Market, by Component:
- Solution
- Services
Enterprise Key Management Market, by Deployment:
- Cloud
- On-premises
Enterprise Key Management Market, by Application:
- Disk Encryption
- File & Folder Encryption
- Database Encryption
- Communication Encryption
- Cloud Encryption
Enterprise Key Management Market, by Region:
- North America
- Europe
- Asia-Pacific
- South America
- Middle East & Africa
Competitive Landscape
Company Profiles: Detailed analysis of the major companies present in the Global Enterprise Key Management Market.Available Customization
The analyst offers customization according to your specific needs. The following customization options are available for the report:- Detailed analysis and profiling of additional market players (up to five).
This product will be delivered within 1-3 business days.
Table of Contents
Companies Mentioned
The key players profiled in this Enterprise Key Management market report include:- Microsoft Corporation
- Amazon.com, Inc.
- RSA Security LLC
- CyberArk Software Ltd.
- Broadcom, Inc.
- Venafi, Inc.
- DigiCert, Inc.
- Protegrity USA, Inc.
- A10 Networks, Inc.
- Delinea Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 181 |
| Published | January 2026 |
| Forecast Period | 2025 - 2031 |
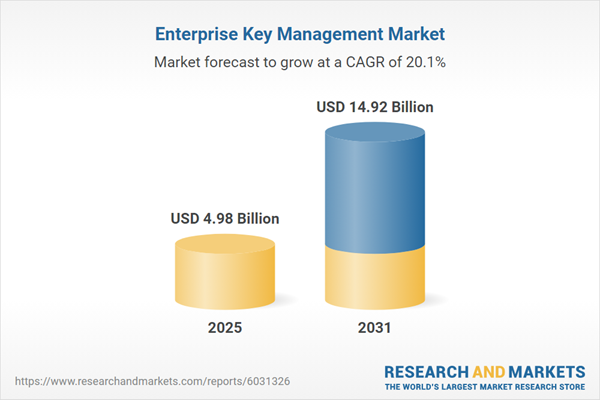
| Estimated Market Value ( USD | $ 4.98 Billion |
| Forecasted Market Value ( USD | $ 14.92 Billion |
| Compound Annual Growth Rate | 20.0% |
| Regions Covered | Global |
| No. of Companies Mentioned | 11 |