Speak directly to the analyst to clarify any post sales queries you may have.
Unveiling the Strategic Imperative of Encryption-as-a-Service in Securing Enterprise Data Across Diverse Industries and Digital Transformation Journeys
Enterprises across industries are navigating an increasingly complex digital terrain, where vast volumes of sensitive information traverse cloud, mobile, and edge environments daily. Encryption-as-a-service emerges as an essential solution that enables organizations to safeguard data without diverting extensive internal resources to design, deploy, and maintain cryptographic systems. By leveraging managed encryption offerings delivered through cloud-native platforms and on-premise appliances alike, firms foster a robust security posture while maintaining agility in their digital transformation initiatives.This service model capitalizes on centralized key management, dynamic tokenization, and adaptable encryption methods tailored to diverse use cases. Organizations are able to encrypt data at rest, in transit, and in use, fulfilling regulatory mandates and elevating customer trust. Furthermore, the shift toward service-based architectures accelerates time to value, as specialized providers bring deep domain expertise, continuous feature enhancements, and automated compliance updates. These advantages underline the strategic imperative for stakeholders to integrate encryption-as-a-service capabilities into their broader cybersecurity frameworks, creating a resilient digital environment that supports both growth and governance objectives.
Exploring the Key Technological and Regulatory Shifts That Are Redefining the Encryption-as-a-Service Market and Enterprise Security Posture
The encryption-as-a-service landscape is undergoing profound transformation driven by technical innovation and evolving regulatory demands. Advances in machine learning and hardware acceleration are optimizing encryption performance, reducing latency and computational overhead for real-time applications. Simultaneously, the convergence of zero-trust principles and data-centric security philosophies has spurred demand for more granular and dynamic encryption controls that adapt to contextual risk assessments.Regulatory bodies worldwide are introducing stringent data protection standards that elevate the importance of standardized encryption frameworks. This dual momentum of technological sophistication and compliance rigor is reshaping procurement and vendor evaluation processes. Enterprises now require solutions capable of integrating seamlessly with container orchestration platforms, multi-cloud environments, and hybrid architectures, while automating policy enforcement across disparate systems. As a result, the market is pivoting toward fully managed, API-driven encryption services that not only protect data assets but also deliver actionable insights into usage patterns and threat indicators, driving continuous improvement in security operations.
Assessing How Recent United States Tariffs in 2025 Are Influencing Cost Structures Strategic Decisions and Innovation Trajectories in Encryption Services
The introduction of new United States tariffs in 2025 has introduced both cost pressures and strategic recalibrations across the encryption-as-a-service sector. Hardware-dependent functions such as key management modules and hardware security modules have experienced elevated import duties, leading providers to re-evaluate supply chains and seek alternative component sourcing. Concurrently, software-centric offerings have redirected development focus toward cloud-native deployments that minimize reliance on tariff-impacted physical assets.Enterprises are responding by embracing hybrid encryption models that leverage local cryptographic acceleration for mission-critical workloads alongside cloud-based services for routine encryption tasks. This reconfiguration optimizes operational budgets while preserving service levels and compliance. Moreover, service providers are investing in domestic manufacturing partnerships and edge-computing integrations to offset tariff-induced cost escalations. These strategic responses to tariff changes underscore the market's resilience and its capacity to maintain innovation trajectories despite evolving trade dynamics.
Identifying Distinct Market Dynamics by Service Model Deployment Type Organization Scale and End-User Verticals That Shape Encryption Service Adoption Trends
The encryption-as-a-service market can be dissected through multiple lenses that illuminate unique growth pathways. By service type, the spectrum ranges from application-level encryption offerings that embed directly into software development pipelines to data encryption suites designed for bulk storage protection, complemented by specialized email encryption functionality that addresses secure messaging requirements. Equally integral are key management services that ensure robust lifecycle handling and tokenization services that obfuscate sensitive data fields while preserving utility for analytics.Organizational scale also shapes solution preferences, with global corporations typically favoring subscription-based models that provide predictable cost structures and enterprise-grade support, while small and medium enterprises often gravitate toward pay-as-you-go frameworks enabling scalable consumption. Encryption method type further differentiates the landscape, as symmetric encryption remains dominant for high-throughput scenarios, asymmetric encryption underpins secure key exchanges, and hybrid encryption bridges performance with security assurances.
Deployment options reflect diverse operational mandates: cloud-based solutions facilitate rapid onboarding and seamless updates, and on-premise installations cater to entities with stringent data residency or latency requirements. Finally, adoption across verticals such as aerospace and defense, banking and insurance, government services, healthcare systems, telecommunications networks, and retail and eCommerce platforms underscores the universal imperative for advanced cryptographic protections tailored to sector-specific threat environments.
Mapping Regional Variations in Adoption Drivers and Challenges Across Americas Europe Middle East Africa and Asia-Pacific in Encryption-as-a-Service Delivery
Regional influences play a pivotal role in shaping encryption-as-a-service strategies and adoption patterns. In the Americas, robust regulatory frameworks such as state-level privacy statutes and industry-specific data security mandates drive widespread demand for cloud-based encryption offerings, while established technology ecosystems expedite integration with existing security infrastructures.Across Europe, the Middle East and Africa, organizations must navigate complex cross-border data transfer rules and a rapidly evolving compliance landscape, amplifying the need for encryption solutions that deliver unified policy enforcement and seamless auditability. This region's heightened focus on data sovereignty has spurred growth in on-premise and hybrid deployments that maintain domestic controls while offering centralized management.
In the Asia-Pacific region, digital transformation initiatives in emerging markets are accelerating adoption, underpinned by investments in cloud-native capabilities and mobile-first architectures. At the same time, mature economies in this region are exploring advanced encryption methods to support IoT deployments and secure inter-enterprise collaborations. These regional particularities underscore the importance of tailoring encryption service portfolios to local regulatory nuances, infrastructure maturity levels, and sectoral priorities.
Profiling Leading Encryption-as-a-Service Vendors to Reveal Strategic Collaborations Differentiation and Innovation Strategies Driving Market Leadership
The competitive landscape is characterized by a diverse mix of specialized cryptography providers, global cloud platforms, and traditional security vendors extending into encryption-as-a-service. Leading firms differentiate through strategic partnerships, proprietary hardware integrations, and developer-centric tooling that streamlines API adoption. Some vendors emphasize algorithmic agility, enabling rapid switching between symmetric and asymmetric methods to optimize performance and security postures.Others focus on delivering turnkey tokenization and key lifecycle management solutions with built-in compliance reporting for highly regulated sectors. Collaboration ecosystems are also expanding, with select providers forging alliances with container orchestration platforms and security orchestration, automation and response frameworks to enhance encryption visibility and incident response. These strategic maneuvers, coupled with targeted mergers and acquisitions, underscore the importance of continuous innovation and ecosystem integration for maintaining market leadership in encryption services.
Outlining Practical Strategic Initiatives and Best Practices for Industry Leaders to Capitalize on Encryption-as-a-Service Opportunities and Mitigate Emerging Risks
To capitalize on emerging encryption-as-a-service opportunities, industry leaders should prioritize the development of flexible consumption models, balancing subscription-based commitments with pay-as-you-go offerings that accommodate varying workloads. Embedding developer-friendly SDKs and APIs into continuous integration pipelines will accelerate uptake among engineering teams and reduce friction in the adoption cycle.Organizations should also foster partnerships with hardware security module manufacturers and cloud providers to establish end-to-end cryptographic infrastructures that blend local acceleration with elastic scale. Embracing open standards and participating in industry alliances can further strengthen interoperability, while rigorous compliance auditing and real-time policy enforcement safeguards protect against evolving threat vectors. By investing in comprehensive training programs and fostering a data-centric security culture, executives can enhance organizational readiness and sustain the performance of encryption initiatives over time.
Detailing the Comprehensive Mixed-Method Research Approach Including Primary and Secondary Data Collection Analytical Frameworks and Validation Protocols
This study employs a mixed-method research design, integrating qualitative insights from executive interviews with cryptography experts and quantitative validation through market participant surveys. Secondary research encompasses an extensive review of regulatory filings, industry white papers, academic journals, and technology analyst reports to establish a comprehensive view of encryption trends and vendor capabilities.Data triangulation techniques are applied to cross-validate findings, ensuring consistency between primary feedback and secondary sources. Competitive benchmarking leverages a proprietary scorecard methodology to assess provider offerings across functional criteria such as algorithmic support, deployment flexibility, developer tooling, and compliance features. Rigorous quality control processes, including peer reviews and validation checks, underpin the robustness of the research outputs, guaranteeing actionable intelligence for decision-makers.
Summarizing Critical Insights and Strategic Imperatives to Guide Decision Makers in Navigating the Evolving Encryption-as-a-Service Landscape with Confidence
This executive summary has distilled the pivotal trends, strategic shifts, and competitive dynamics defining the encryption-as-a-service market. We have explored how technological advancements, regulatory developments, and evolving trade policies converge to influence solution architectures and adoption strategies. By examining segmentation insights across service types, organizational scales, encryption methods, business models, deployment approaches, and end-use verticals, stakeholders gain a nuanced understanding of market drivers and barriers.Regional analysis highlights the importance of tailoring service portfolios to local compliance landscapes and infrastructure maturity, while competitive profiling underscores the significance of innovation, ecosystem integration, and developer enablement. Actionable recommendations equip industry leaders with a roadmap to optimize consumption models, strengthen partnerships, and embed encryption into core business processes. Together, these insights furnish a strategic blueprint for navigating the complexities of data protection and realizing the transformative potential of encryption-as-a-service.
Market Segmentation & Coverage
This research report forecasts revenues and analyzes trends in each of the following sub-segmentations:- Service Type
- Application-level Encryption Service
- Data Encryption Services
- Email Encryption Services
- Key Management Services
- Tokenization Services
- Organization Size
- Large Enterprises
- Small & Medium Enterprises
- Encryption Method Type
- Asymmetric Encryption
- Hybrid Encryption
- Symmetric Encryption
- Business Model
- Pay-as-you-go
- Subscription-Based
- Deployment Type
- Cloud-Based
- On-Premise
- End User
- Aerospace & Defense
- Banking, Financial Services, Insurance
- Government & Public Sector
- Healthcare
- IT & Telecommunication
- Retail & eCommerce
- Americas
- North America
- United States
- Canada
- Mexico
- Latin America
- Brazil
- Argentina
- Chile
- Colombia
- Peru
- North America
- Europe, Middle East & Africa
- Europe
- United Kingdom
- Germany
- France
- Russia
- Italy
- Spain
- Netherlands
- Sweden
- Poland
- Switzerland
- Middle East
- United Arab Emirates
- Saudi Arabia
- Qatar
- Turkey
- Israel
- Africa
- South Africa
- Nigeria
- Egypt
- Kenya
- Europe
- Asia-Pacific
- China
- India
- Japan
- Australia
- South Korea
- Indonesia
- Thailand
- Malaysia
- Singapore
- Taiwan
- Akeyless Security Ltd.
- Amazon Web Services Inc.
- Box, Inc.
- Broadcom Inc.
- Cisco Systems, Inc.
- DigiCert Inc.
- Entrust Corporation
- Fortanix Inc.
- Fortinet, Inc.
- HashiCorp Inc.
- HP Inc.
- International Business Machines Corporation
- McAfee Corporation
- Microsoft Corporation
- OneSpan Inc.
- Oracle Corporation
- Orca Security
- Palo Alto Networks, Inc
- Protegrity USA, Inc.
- Sophos Limited
- Thales Group
- Trend Micro Inc.
- Utimaco Management Services GmbH
- Utimaco Safeware, Inc.
- Venafi Inc. by CyberArk Software Limited
Table of Contents
3. Executive Summary
4. Market Overview
7. Cumulative Impact of Artificial Intelligence 2025
Companies Mentioned
The companies profiled in this Encryption-as-a-Service Market report include:- Akeyless Security Ltd.
- Amazon Web Services Inc.
- Box, Inc.
- Broadcom Inc.
- Cisco Systems, Inc.
- DigiCert Inc.
- Entrust Corporation
- Fortanix Inc.
- Fortinet, Inc.
- HashiCorp Inc.
- HP Inc.
- International Business Machines Corporation
- McAfee Corporation
- Microsoft Corporation
- OneSpan Inc.
- Oracle Corporation
- Orca Security
- Palo Alto Networks, Inc
- Protegrity USA, Inc.
- Sophos Limited
- Thales Group
- Trend Micro Inc.
- Utimaco Management Services GmbH
- Utimaco Safeware, Inc.
- Venafi Inc. by CyberArk Software Limited
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 185 |
| Published | November 2025 |
| Forecast Period | 2025 - 2032 |
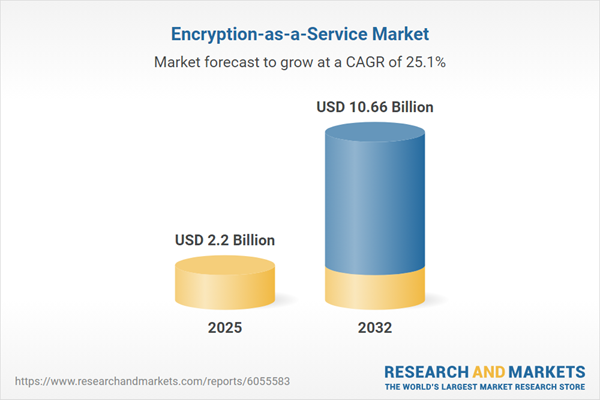
| Estimated Market Value ( USD | $ 2.2 Billion |
| Forecasted Market Value ( USD | $ 10.66 Billion |
| Compound Annual Growth Rate | 25.0% |
| Regions Covered | Global |
| No. of Companies Mentioned | 26 |