Global Cryptojacking Solutions Market - Key Trends & Drivers Summarized
Why Is Cryptojacking Becoming a Pervasive Cybersecurity Threat Across Sectors?
Cryptojacking - unauthorized use of an individual's or organization's computing resources to mine cryptocurrency - is emerging as one of the most widespread and stealthy cyber threats in the digital era. Unlike traditional forms of cyberattacks that aim to steal data or ransom files, cryptojacking silently hijacks processing power, often going unnoticed for long periods while degrading system performance, increasing energy costs, and posing long-term infrastructure risks. It can be executed through malicious email attachments, infected websites, browser-based scripts, or compromised cloud environments. As cryptocurrencies gain mainstream acceptance and remain volatile yet lucrative, cybercriminals are increasingly turning to cryptojacking due to its lower risk and minimal user interaction. This method allows attackers to monetize access without triggering alarms, making it particularly difficult to detect. The growing reliance on cloud computing, IoT devices, and remote work setups has expanded the attack surface exponentially, offering new vectors for threat actors. From enterprise servers and networked printers to personal laptops and smartphones, any internet-connected device with processing power is a potential target. Cryptojacking not only impacts IT performance but also contributes to broader operational inefficiencies, especially in industries dependent on computational resources like finance, manufacturing, and healthcare. As a result, the demand for robust, proactive cryptojacking detection and mitigation solutions is surging across public and private sectors.How Are Cybersecurity Platforms Evolving to Address the Challenges of Cryptojacking Detection and Prevention?
To combat the elusive and evolving nature of cryptojacking, cybersecurity providers are rapidly innovating their technologies, integrating advanced detection engines and behavioral analysis tools into endpoint security and network defense systems. Traditional antivirus solutions are often insufficient, as many cryptojacking scripts are fileless and reside in memory, evading conventional signature-based detection. As a result, modern cryptojacking solutions increasingly rely on real-time anomaly detection powered by machine learning algorithms that can monitor CPU usage patterns, flag abnormal spikes, and correlate these with user activity and system logs. Endpoint Detection and Response (EDR) tools, combined with cloud security posture management (CSPM), are playing a crucial role in identifying malicious mining activity, particularly in cloud and hybrid environments where visibility is often limited. Browser-based defenses such as anti-cryptomining extensions, DNS filtering, and JavaScript blockers are also gaining popularity as first-line protections. On the enterprise side, Security Information and Event Management (SIEM) platforms are being enhanced with specific rules and threat intelligence feeds that include cryptomining indicators of compromise (IOCs). Managed Security Service Providers (MSSPs) are offering specialized services to continuously monitor for signs of unauthorized mining activity across large IT infrastructures. Together, these tools form a layered defense strategy that focuses not just on blocking cryptojacking attempts, but on early detection, incident response, and ongoing system hardening.What Operational, Financial, and Environmental Risks Are Associated with Cryptojacking Attacks?
The risks posed by cryptojacking extend far beyond mere IT nuisance, affecting organizations across operational, financial, and even environmental dimensions. Operationally, cryptojacking can significantly degrade system performance by overutilizing CPU and GPU resources, leading to slower processing times, application crashes, and reduced service availability. In high-performance computing environments - such as data centers, research labs, and financial institutions - this resource drain can severely disrupt workflows, affect productivity, and delay critical operations. Financially, the hidden cost of cryptojacking is substantial: increased electricity consumption, accelerated hardware degradation, and the diversion of IT personnel to address performance issues all contribute to increased operating expenses. For organizations managing hundreds or thousands of endpoints, these costs can escalate rapidly if the attack goes undetected. Cryptojacking also presents a reputational risk - especially for cloud service providers and managed IT firms - if clients suffer service degradation or discover security lapses. On a broader scale, the environmental impact of unauthorized cryptomining is non-trivial; the energy-intensive nature of mining increases the carbon footprint of affected systems, undermining corporate sustainability efforts. In regulated industries, failure to detect and remediate cryptojacking may result in non-compliance with cybersecurity and data protection standards, potentially leading to legal and financial penalties. These compounding risks underscore the necessity for organizations to invest in comprehensive cryptojacking protection as part of their core cybersecurity strategy.What Are the Key Drivers Fueling the Growth of the Cryptojacking Solutions Market Globally?
The growth of the global cryptojacking solutions market is driven by a combination of rising cybercrime sophistication, increased enterprise reliance on digital infrastructure, and heightened awareness of the operational consequences of unauthorized cryptomining. One of the most important drivers is the surge in cryptocurrency value and adoption, which directly incentivizes cybercriminals to mine tokens using hijacked resources rather than investing in expensive hardware and electricity. As organizations expand their digital footprint - adopting cloud computing, IoT networks, and remote work tools - they simultaneously increase their exposure to cryptojacking threats. High-profile incidents involving government agencies, universities, and corporations have brought cryptojacking into the spotlight, elevating it from a niche concern to a mainstream cybersecurity priority. Regulatory pressure is another important factor, with data protection laws and cybersecurity standards now emphasizing the need for continuous monitoring, threat detection, and incident reporting, all of which are enabled by cryptojacking-specific tools. The emergence of AI-driven security platforms and modular cybersecurity frameworks is making it easier for organizations to integrate cryptojacking detection into broader risk management systems. Cyber insurance firms are also beginning to assess cryptojacking exposure as part of their underwriting processes, encouraging policyholders to implement more advanced security solutions. Together, these market dynamics are fueling a sustained and growing demand for cryptojacking solutions, positioning them as a critical element in the global fight against invisible, resource-draining cyber threats.Report Scope
The report analyzes the Cryptojacking Solutions market, presented in terms of market value (US$). The analysis covers the key segments and geographic regions outlined below:- Segments: Component (Anti-Cryptojacking Solution, Services, Professional Services, Consulting, Training & Education, Support & Maintenance, Managed Services); Deployment (Cloud, On-Premise); End-Use (BFSI, Retail, Government & Public Sector, Manufacturing, Healthcare, Education, Energy & Utilities, Other End-Uses).
- Geographic Regions/Countries: World; United States; Canada; Japan; China; Europe (France; Germany; Italy; United Kingdom; Spain; Russia; and Rest of Europe); Asia-Pacific (Australia; India; South Korea; and Rest of Asia-Pacific); Latin America (Argentina; Brazil; Mexico; and Rest of Latin America); Middle East (Iran; Israel; Saudi Arabia; United Arab Emirates; and Rest of Middle East); and Africa.
Key Insights:
- Market Growth: Understand the significant growth trajectory of the Anti-Cryptojacking Solution segment, which is expected to reach US$7.4 Billion by 2030 with a CAGR of a 9.3%. The Services segment is also set to grow at 9.2% CAGR over the analysis period.
- Regional Analysis: Gain insights into the U.S. market, valued at $4.7 Billion in 2024, and China, forecasted to grow at an impressive 14.5% CAGR to reach $6.5 Billion by 2030. Discover growth trends in other key regions, including Japan, Canada, Germany, and the Asia-Pacific.
Why You Should Buy This Report:
- Detailed Market Analysis: Access a thorough analysis of the Global Cryptojacking Solutions Market, covering all major geographic regions and market segments.
- Competitive Insights: Get an overview of the competitive landscape, including the market presence of major players across different geographies.
- Future Trends and Drivers: Understand the key trends and drivers shaping the future of the Global Cryptojacking Solutions Market.
- Actionable Insights: Benefit from actionable insights that can help you identify new revenue opportunities and make strategic business decisions.
Key Questions Answered:
- How is the Global Cryptojacking Solutions Market expected to evolve by 2030?
- What are the main drivers and restraints affecting the market?
- Which market segments will grow the most over the forecast period?
- How will market shares for different regions and segments change by 2030?
- Who are the leading players in the market, and what are their prospects?
Report Features:
- Comprehensive Market Data: Independent analysis of annual sales and market forecasts in US$ Million from 2024 to 2030.
- In-Depth Regional Analysis: Detailed insights into key markets, including the U.S., China, Japan, Canada, Europe, Asia-Pacific, Latin America, Middle East, and Africa.
- Company Profiles: Coverage of players such as Advanced Research Systems, Alcor Life Extension Foundation, American Cryonics Society, Atelerix Limited, BioLife Solutions and more.
- Complimentary Updates: Receive free report updates for one year to keep you informed of the latest market developments.
Some of the 42 companies featured in this Cryptojacking Solutions market report include:
- A10 Networks
- Acronis
- Avast
- Bitdefender
- BlackFog
- Check Point Software Technologies
- Cisco
- CrowdStrike
- ESET
- Fortinet
- Kaspersky
- Malwarebytes
- McAfee
- Palo Alto Networks
- Report URI
- SentinelOne
- SonicWall
- Sophos
- Symantec (Broadcom)
- Vali Cyber
This edition integrates the latest global trade and economic shifts into comprehensive market analysis. Key updates include:
- Tariff and Trade Impact: Insights into global tariff negotiations across 180+ countries, with analysis of supply chain turbulence, sourcing disruptions, and geographic realignment. Special focus on 2025 as a pivotal year for trade tensions, including updated perspectives on the Trump-era tariffs.
- Adjusted Forecasts and Analytics: Revised global and regional market forecasts through 2030, incorporating tariff effects, economic uncertainty, and structural changes in globalization. Includes historical analysis from 2015 to 2023.
- Strategic Market Dynamics: Evaluation of revised market prospects, regional outlooks, and key economic indicators such as population and urbanization trends.
- Innovation & Technology Trends: Latest developments in product and process innovation, emerging technologies, and key industry drivers shaping the competitive landscape.
- Competitive Intelligence: Updated global market share estimates for 2025, competitive positioning of major players (Strong/Active/Niche/Trivial), and refined focus on leading global brands and core players.
- Expert Insight & Commentary: Strategic analysis from economists, trade experts, and domain specialists to contextualize market shifts and identify emerging opportunities.
Table of Contents
Companies Mentioned (Partial List)
A selection of companies mentioned in this report includes, but is not limited to:
- A10 Networks
- Acronis
- Avast
- Bitdefender
- BlackFog
- Check Point Software Technologies
- Cisco
- CrowdStrike
- ESET
- Fortinet
- Kaspersky
- Malwarebytes
- McAfee
- Palo Alto Networks
- Report URI
- SentinelOne
- SonicWall
- Sophos
- Symantec (Broadcom)
- Vali Cyber
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 290 |
| Published | January 2026 |
| Forecast Period | 2024 - 2030 |
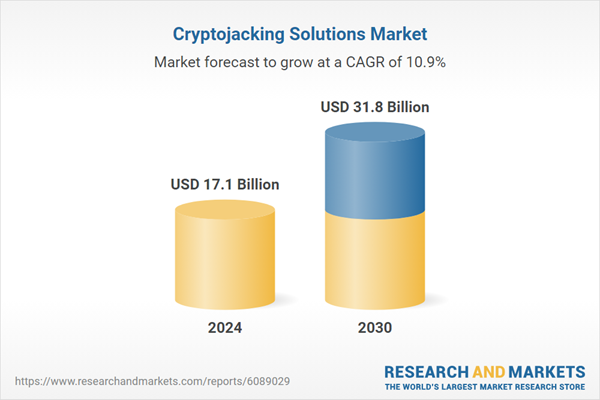
| Estimated Market Value ( USD | $ 17.1 Billion |
| Forecasted Market Value ( USD | $ 31.8 Billion |
| Compound Annual Growth Rate | 10.9% |
| Regions Covered | Global |