Speak directly to the analyst to clarify any post sales queries you may have.
Healthcare data security is a top concern for industry leaders, as mounting risks and complex regulatory demands make safeguarding patient information a strategic imperative. As digital health adoption rises, organizations must strengthen their approaches to protect sensitive data and maintain compliance with evolving frameworks.
Market Snapshot: Healthcare Data Security Market Size and Growth
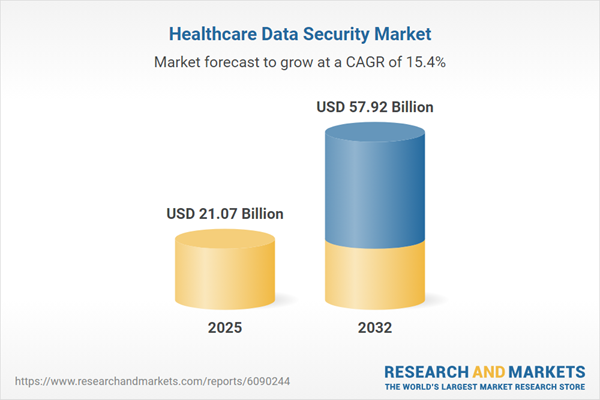
The healthcare data security market grew from USD 18.38 billion in 2024 to USD 21.07 billion in 2025, with expectations of continued expansion at a CAGR of 15.42% and a projected market value of USD 57.92 billion by 2032. This upward trend is fueled by rapid digital transformation, increasing frequency of cyberattacks, and the escalating complexity of compliance mandates. Market participants—including providers, payers, and solution vendors—are recalibrating their strategies to address the heightened risks inherent in interconnected healthcare environments.
Scope & Segmentation: Comprehensive Insights into Offerings, Threats, and Regions
This report delivers an in-depth analysis of healthcare data security, spanning the following segments and regional markets:
- Offerings: Services, including Consulting, Managed Security, and Training & Support; Solutions across Antivirus & Antimalware, DDoS Mitigation, Identity & Access Management, Intrusion Detection/Prevention, Risk & Compliance Management, and Security Information & Event Management.
- Types of Threat: Advanced Persistent Threats, Distributed Denial-of-Service (DDoS), Lost or Stolen Devices, Malware, Spyware.
- Security Types: Application Security, Cloud Security Solutions, Endpoint & IoT Security, Network Security.
- End-User Verticals: Clinics & Physician Practices, Diagnostic & Imaging Centers, Hospitals & Healthcare Systems, Life Sciences Organizations & Research Institutes, Payers & Insurance Companies.
- Deployment Models: Cloud-Based and On-Premises approaches to data protection.
- Regions Covered: Americas (including North America and Latin America), Europe, Middle East & Africa (EMEA), and Asia-Pacific, with country-level analysis for both established and emerging markets.
- Key Companies Analyzed: Fortinet, IBM, Broadcom, Cisco, CrowdStrike, Dell, ExtraHop, McAfee, Microsoft, among others.
Key Takeaways for Enterprise Decision-Makers
- Growing network complexity and proliferation of digital health modalities increase vulnerability, making advanced solutions and robust governance necessary foundations for risk reduction.
- Strategic investments balance cutting-edge tools (such as zero-trust architectures and real-time analytics) with workforce training and cross-functional governance to build long-term resilience.
- Managed security partnerships and the integration of AI-driven threat intelligence are becoming essential for early detection and incident response throughout healthcare delivery organizations.
- Variation in regulatory regimes across regions drives distinct adoption patterns, with mature markets leaning on unified risk platforms and emerging regions adopting end-to-end managed services.
- The evolving threat landscape has prompted providers and payers to implement proactive risk assessment and continuous monitoring as core elements of security planning.
Tariff Impact: Navigating Cost Pressures and Supply Chain Adjustments
Recent tariffs imposed by the United States in 2025 add complexity to the procurement and deployment of healthcare data security infrastructure. Organizations face elevated costs for imported hardware, compelling them to adopt alternative sourcing, local manufacturing, or regional vendor partnerships. Shifts in software licensing and more flexible deployment models have arisen as suppliers respond to buyer cost constraints. These factors are influencing competitive dynamics, with consolidation and new entrants reshaping the provider landscape.
Methodology & Data Sources for Healthcare Data Security Market Research
This report leverages a robust methodology, combining expert interviews with senior security architects and healthcare IT leaders, comprehensive secondary data from regulatory filings and vendor sources, and triangulated validation insights. Analytical frameworks were peer-reviewed for consistency and contextual accuracy, ensuring actionable, empirically grounded findings.
Why This Report Matters: Actionable Guidance for Healthcare Security Leadership
- Enables strategic planning across budgeting, procurement, and compliance by presenting segmented views of vendors, regions, and technologies relevant to healthcare data security.
- Identifies impending regulatory and threat landscape changes, supporting well-informed investment and risk management decisions.
- Highlights partnership models and operational tactics that drive improved organizational resilience and data protection.
Conclusion
The healthcare data security market is advancing rapidly, underscored by evolving threats, regulatory changes, and shifting sourcing patterns. Senior leaders benefit from using these insights to reinforce their organization’s security strategies and strengthen patient trust amid ongoing digital transformation.
Table of Contents
3. Executive Summary
4. Market Overview
7. Cumulative Impact of Artificial Intelligence 2025
Companies Mentioned
The companies profiled in this Healthcare Data Security Market report include:- Fortinet, Inc.
- International Business Machines Corporation
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- Dell Inc.
- ExtraHop Networks, Inc.
- F5 Networks, Inc.
- FireEye, Inc.
- Imperva, Inc.
- Imprivata, Inc.
- LogRhythm, Inc.
- McAfee, LLC
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- Rapid7, Inc.
- Sophos Group plc
- Trend Micro Incorporated
- Varonis Systems, Inc.
- Zscaler, Inc.
- Viseven Europe OÜ
- Oracle Corporation
- Syteca Inc.
- Rubrik, Inc.
- Qualysec
- Microsoft Corporation
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 186 |
| Published | October 2025 |
| Forecast Period | 2025 - 2032 |
| Estimated Market Value ( USD | $ 21.07 Billion |
| Forecasted Market Value ( USD | $ 57.92 Billion |
| Compound Annual Growth Rate | 15.4% |
| Regions Covered | Global |
| No. of Companies Mentioned | 28 |