Speak directly to the analyst to clarify any post sales queries you may have.
Understanding Zero Trust Security's Critical Role in Reinventing Enterprise Cyber Defenses for an Era of Pervasive Cyber Threats and Dynamic IT Environments
As enterprises confront an ever-expanding landscape of cyber threats, Zero Trust Security has emerged as the defining framework for safeguarding critical assets in modern IT environments. Initially conceived to address the limitations of perimeter-based defenses, this approach mandates continuous verification of every access request, regardless of origin. By challenging the traditional notion of implicit trust for users and devices within corporate networks, Zero Trust reshapes how organizations architect their security controls and govern data protection.Building on the principle of “never trust, always verify,” Zero Trust designs integrate identity authentication, least-privilege access, microsegmentation, and real-time monitoring to create a dynamic, context-aware security posture. This shift enables enterprises to reduce risk exposure, minimize attack surfaces, and respond swiftly to emerging threats. Furthermore, the proliferation of cloud services, remote work models, and IoT devices has amplified the importance of adopting a security paradigm that extends beyond fixed network boundaries.
In today's environment, leaders across industries recognize that effective cybersecurity is no longer a standalone function but a strategic enabler of business continuity and innovation. As you delve into the insights in this summary, you will gain clarity on how Zero Trust frameworks can be tailored to address your organization's unique requirements and accelerate the journey towards resilient, future-ready defenses.
Analyzing How Emerging Threats and Technological Advances Are Driving a Paradigm Shift Toward Zero Trust Architectures Across Industries Globally
The evolution of cyber adversaries and the rapid advancement of technology have catalyzed a profound transformation in enterprise security strategies. Today's threat actors deploy increasingly sophisticated tactics, from fileless malware and supply chain attacks to deepfake-enabled social engineering. In parallel, organizations are embracing hybrid architectures, edge computing, and software-defined networks, creating a landscape of dispersed assets that defy conventional security perimeters.Consequently, security architects are pivoting away from static controls toward adaptive, identity-centric frameworks. This paradigmatic shift is underpinned by the integration of machine learning-based analytics, zero-trust network access solutions, and policy-driven orchestration platforms. Together, these innovations facilitate automated policy enforcement and real-time threat detection, dramatically accelerating incident response.
Moreover, regulatory requirements and privacy mandates are imposing stricter standards for data protection and user privacy. Enterprises that adopt Zero Trust methodologies gain a competitive advantage by demonstrating compliance with frameworks such as GDPR, CCPA, and NIST standards, while also fostering greater stakeholder trust. As this transformation unfolds, organizations that embrace Zero Trust not only mitigate current risks but also establish the agility needed to anticipate and counter future attack vectors.
Assessing the Far-Reaching Consequences of United States Tariffs Implemented in 2025 on Zero Trust Security Supply Chains and Global Market Dynamics
In 2025, the imposition of new tariffs by the United States has reverberated throughout global technology supply chains, introducing cost pressures and procurement delays that are reshaping Zero Trust deployment strategies. Hardware components, including network devices and security gateways, now face extended lead times and elevated pricing, compelling organizations to reevaluate their purchasing decisions and lifecycle management plans.Simultaneously, software vendors reliant on imported cryptographic modules and authentication hardware are adjusting licensing models and support agreements to offset increased duties. These adjustments have fueled demand for locally sourced or alternative solutions, prompting a surge in partnerships with regional manufacturers and service providers. Meanwhile, consulting firms and implementation specialists are recalibrating their engagement frameworks to account for shifting cost structures, often bundling services to deliver predictable outcomes under fixed budgets.
Despite these headwinds, enterprises remain committed to advancing Zero Trust roadmaps, recognizing that the long-term benefits of risk reduction, regulatory compliance, and operational resilience outweigh short-term financial challenges. In response, industry players are innovating around open standards and software-defined security controls, enabling organizations to pivot rapidly between vendors and deployment models, thereby mitigating the influence of tariff-induced disruptions on critical security initiatives.
Uncovering Strategic Insights from Diverse Segmentation Criteria That Illuminate Opportunities and Challenges for Zero Trust Security Deployment and Adoption
A nuanced understanding of the Zero Trust market emerges when examining how offerings, authentication mechanisms, access types, deployment models, applications, organizational scales, and industry domains intersect. Through the lens of product portfolios, hardware components such as network devices and security gateways coexist with professional services encompassing consulting, implementation, and support. Software modules further enrich the ecosystem with solutions for data encryption and protection, identity and access management, security analytics, and threat intelligence. Transitioning from offerings to identity verification, authentication models span single-factor methods, passwordless approaches, and multi-factor schemes that integrate biometric and two-factor authentication protocols to strengthen access controls.Access modalities themselves span controls at the application layer, device level, and broader network perimeter, each demanding specific orchestration strategies. Decision-makers must also weigh deployment preferences, choosing between on-premise architectures and cloud-based infrastructures, informed by considerations around latency, scalability, and regulatory constraints. Application use cases extend from core access management to specialized domains including data security, endpoint protection, identity verification, and security operations orchestration.
Organizational size shapes requirements significantly, with large enterprises opting for deeply integrated, customized implementations while small and medium enterprises favor turnkey solutions that deliver rapid return on investment. Across industry verticals-from banking, financial services, and insurance through education, energy and utilities, government and defense, to healthcare, IT and telecommunications, manufacturing, and retail-each sector's unique risk profile and compliance environment dictates tailored Zero Trust adoption trajectories.
Illuminating Regional Dynamics and Growth Potential Across the Americas EMEA and Asia-Pacific to Guide Strategic Expansion of Zero Trust Solutions
Regional dynamics reveal that the Americas continue to drive innovation in Zero Trust adoption, supported by mature technology ecosystems and significant investments in cybersecurity initiatives. Leading organizations in North America are piloting advanced identity orchestration and microsegmentation at scale, setting benchmarks that peers across the hemisphere are increasingly adopting. As a result, the region not only pioneers new use cases but also influences technology roadmaps and standards development.Across Europe, Middle East & Africa, regulatory drivers such as GDPR and emerging data protection frameworks have intensified demand for solutions that provide granular visibility and policy enforcement. Government and defense sectors in particular are prioritizing Zero Trust frameworks to secure critical infrastructure against persistent, state-sponsored threats. Enterprise buyers in this region are also focusing on interoperability and local data sovereignty, driving robust collaboration between global vendors and regional integrators.
In Asia-Pacific, rapid digital transformation initiatives and expansive rollout of 5G networks are catalyzing interest in identity-based security controls and edge protection strategies. Organizations in this region face unique challenges related to supply chain resilience and compliance with diverse national regulations. Consequently, there is growing momentum behind cloud-native Zero Trust solutions and managed security services that offer flexible, consumption-based pricing. As these regional dynamics continue to evolve, enterprises must align their strategic priorities with local market conditions while leveraging global best practices to maximize the effectiveness of their Zero Trust implementations.
Highlighting Leading Vendors and Innovative Collaborations That Are Shaping the Competitive Landscape of Zero Trust Security Solutions
Leading vendors are differentiating their portfolios through strategic partnerships, acquisitions, and the integration of emerging technologies such as artificial intelligence and behavioral analytics. Organizations like Zscaler and Palo Alto Networks have expanded their platforms to deliver end-to-end zero-trust network access capabilities, while established giants including Cisco and Microsoft are embedding identity protections directly into their collaboration and cloud suites. New entrants focusing on niche segments-such as identity federation, threat intelligence feeds, and microsegmentation orchestration-are also gaining traction by addressing specialized enterprise requirements.Collaborative ecosystems are becoming increasingly critical, with technology alliances forming around open frameworks and interoperable APIs. Managed security service providers are capitalizing on these alliances to offer comprehensive managed detection and response services that leverage zero-trust principles. Additionally, channel partners and integrators are enhancing their value propositions by bundling advisory, implementation, and training services that accelerate deployment and foster user adoption.
Competition in this landscape is driving rapid innovation cycles, prompting vendors to publish reference architectures, open-source tooling, and developer-friendly toolkits. This collaborative approach not only reduces integration friction but also accelerates the path from proof-of-concept to full-scale production. As enterprises evaluate their security technology stacks, they increasingly prioritize vendors who demonstrate both technical leadership and the ability to support long-term strategic objectives.
Formulating Actionable Strategic Recommendations to Empower Industry Leaders in Accelerating Adoption of Robust and Scalable Zero Trust Architectures
Industry leaders must prioritize continuous visibility across their ecosystems by integrating telemetry from endpoints, networks, applications, and cloud environments into unified analytics platforms. By adopting identity-driven controls and enforcing least-privilege access policies at every transaction, organizations can minimize their attack surface while maintaining operational agility. Furthermore, embedding microsegmentation within both traditional networks and cloud-native environments will prevent lateral movement of threats, even after initial compromise.To accelerate adoption, executives should forge strong alliances with technology partners that offer co-development opportunities and pre-validated reference implementations. Training and change management are equally critical; personnel must be upskilled on both the technical and procedural aspects of Zero Trust protocols. In parallel, security teams should refine governance frameworks to oversee policy lifecycle management, ensuring that controls evolve in lockstep with business priorities.
Finally, fostering a culture of continuous improvement-reinforced by regular threat hunting exercises, red team assessments, and tabletop simulations-will strengthen organizational resilience. By translating insights from these activities into iterative refinements of their Zero Trust roadmaps, leaders can sustain momentum and ensure that their security posture adapts proactively to emerging threats and business initiatives.
Detailing Rigorous Multistage Research Methodology Combining Qualitative and Quantitative Approaches to Validate Zero Trust Security Market Insights
This study combines primary interviews with CISOs, security architects, and IT leaders alongside quantitative surveys of technology buyers and implementers. In-depth qualitative discussions provided nuanced perspectives on deployment challenges, vendor evaluations, and strategic roadmaps. These insights were supplemented by the analysis of financial reports, vendor whitepapers, product datasheets, and industry conference findings to ensure comprehensive coverage.Data triangulation was applied to reconcile discrepancies across sources, enabling robust validation of emerging trends and vendor capabilities. The research also incorporated structured case studies of cross-industry Zero Trust deployments, highlighting best practices and common pitfalls. Expert review panels, constituted of independent analysts and academic researchers, assessed the methodology and findings to guarantee objectivity and methodological rigor.
Finally, the synthesized insights underwent iterative peer reviews, ensuring that the conclusions accurately reflect the current state of Zero Trust adoption and anticipate future developments. This rigorous approach underpins the credibility of the recommendations and strategic insights presented throughout this executive summary.
Synthesis of Key Findings and Strategic Implications Underscoring the Critical Value of Zero Trust Security in Evolving Threat Landscapes
As digital infrastructures continue to fragment across cloud, on-premise, and edge environments, the Zero Trust paradigm stands out as a unifying strategy to safeguard data and identities. The convergence of identity-based access controls, microsegmentation, and continuous monitoring forms a resilient foundation that adapts dynamically to evolving threat landscapes. From the strain of tariffs on hardware supply chains to the differentiation of offerings across segmentation axes, this summary has traced the multifaceted drivers shaping Zero Trust adoption.Regional insights illustrate that while the Americas maintain leadership through innovation and investment, Europe, the Middle East, and Africa focus on regulatory compliance and sovereignty, and Asia-Pacific leverages cloud-native architectures and managed services to overcome resource constraints. Vendor dynamics reveal a competitive environment driven by ecosystem partnerships and technical differentiation, while actionable recommendations underscore the importance of orchestration, training, and iterative refinement.
Ultimately, Zero Trust is not a one-time project but an ongoing journey that demands strategic alignment, cross-functional collaboration, and a commitment to continuous improvement. Organizations that embrace this mindset will achieve greater resilience, regulatory alignment, and the agility needed to seize emerging digital opportunities.
Market Segmentation & Coverage
This research report forecasts revenues and analyzes trends in each of the following sub-segmentations:- Offerings
- Hardware
- Network Devices
- Security Gateways
- Services
- Consulting Service
- Implementation Service
- Support & Maintenance Service
- Software
- Data Encryption & Protection
- Identity & Access Management
- Security Analytics
- Threat Intelligence
- Hardware
- Authentication Type
- Multi-Factor Authentication
- Biometric Authentication
- Two-Factor Authentication
- Passwordless Authentication
- Single-Factor Authentication
- Multi-Factor Authentication
- Access Type
- Application Access Controls
- Device Access Controls
- Network Access Controls
- Deployment Model
- Cloud-based
- On-premise
- Applications
- Access Management
- Data Security
- Endpoint Security
- Identity Verification
- Security Operations
- Organization Size
- Large Enterprises
- Small & Medium Enterprises
- Industry Verticals
- Banking, Financial Services, & Insurance(BFSI)
- Education
- Energy & Utilities
- Government & Defense
- Healthcare
- IT & Telecommunication
- Manufacturing
- Retail
- Americas
- North America
- United States
- Canada
- Mexico
- Latin America
- Brazil
- Argentina
- Chile
- Colombia
- Peru
- North America
- Europe, Middle East & Africa
- Europe
- United Kingdom
- Germany
- France
- Russia
- Italy
- Spain
- Netherlands
- Sweden
- Poland
- Switzerland
- Middle East
- United Arab Emirates
- Saudi Arabia
- Qatar
- Turkey
- Israel
- Africa
- South Africa
- Nigeria
- Egypt
- Kenya
- Europe
- Asia-Pacific
- China
- India
- Japan
- Australia
- South Korea
- Indonesia
- Thailand
- Malaysia
- Singapore
- Taiwan
- Akamai Technologies, Inc.
- Amazon Web Services, Inc.
- BeyondTrust, Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- CrowdStrike Holdings, Inc.
- CyberArk Software Ltd.
- Duo Security, Inc.
- F5 Networks, Inc.
- Fortinet, Inc.
- Google LLC by Alphabet Inc.
- IBM Corporation
- Imperva, Inc. by Thales Group
- Juniper Networks, Inc. by HPE
- McAfee, Inc.
- Microsoft Corporation
- Netskope, Inc.
- Okta, Inc.
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- RSA Security LLC
- SentinelOne, Inc.
- Sophos Ltd.
- Zscaler, Inc.
Table of Contents
3. Executive Summary
4. Market Overview
7. Cumulative Impact of Artificial Intelligence 2025
Companies Mentioned
The companies profiled in this Zero Trust Security Vendor market report include:- Akamai Technologies, Inc.
- Amazon Web Services, Inc.
- BeyondTrust, Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- CrowdStrike Holdings, Inc.
- CyberArk Software Ltd.
- Duo Security, Inc.
- F5 Networks, Inc.
- Fortinet, Inc.
- Google LLC by Alphabet Inc.
- IBM Corporation
- Imperva, Inc. by Thales Group
- Juniper Networks, Inc. by HPE
- McAfee, Inc.
- Microsoft Corporation
- Netskope, Inc.
- Okta, Inc.
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- RSA Security LLC
- SentinelOne, Inc.
- Sophos Ltd.
- Zscaler, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 193 |
| Published | November 2025 |
| Forecast Period | 2025 - 2032 |
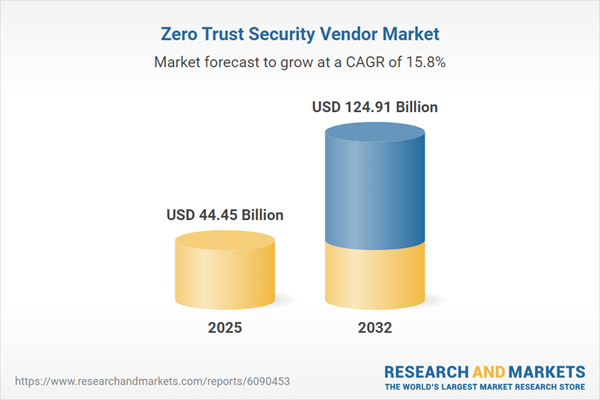
| Estimated Market Value ( USD | $ 44.45 Billion |
| Forecasted Market Value ( USD | $ 124.91 Billion |
| Compound Annual Growth Rate | 15.8% |
| Regions Covered | Global |
| No. of Companies Mentioned | 26 |