HSMs are playing a pivotal role in enabling encryption key management and securing these architectures. With the global rise of Internet-connected devices, secure communication and identity verification are becoming essential. Hardware security modules ensure the confidentiality and authenticity of data transferred across these devices by enabling cryptographic operations and safely storing sensitive keys. With over 17 billion IoT devices expected to be in use by 2024, the reliance on secure HSM infrastructures is surging, placing them at the core of digital trust frameworks across industries.
The USB-based or portable segment generated USD 494 million in 2024 and is forecasted to grow at a CAGR of 15.1% through 2034. These compact devices offer mobility and flexibility, enabling enterprises to perform cryptographic operations securely from any location. As cyber threats increase in complexity, companies require agile security solutions that can be easily integrated into their operational workflows. Portable HSMs address this need by offering plug-and-play encryption key management and secure storage without compromising performance or compliance. Their ease of deployment and cost-effectiveness make them particularly appealing to organizations with distributed workforces and remote operational environments.
In 2024, the SSL/TLS key protection segment generated USD 244 million with a projected CAGR of 16.7%. With secure internet communications becoming more critical amid rising cyberattacks targeting digital certificates, organizations are placing greater emphasis on safeguarding SSL and TLS cryptographic keys. HSMs are being increasingly adopted to ensure strong encryption, reliable certificate handling, and secure lifecycle management of private keys. These modules offer tamper-resistant protection and help reduce the attack surface by isolating cryptographic operations from software vulnerabilities. As digital trust becomes a foundational element of enterprise IT systems, the role of HSMs in SSL/TLS environments continues to grow.
Germany Hardware Security Modules Market generated USD 71 million in 2024, with a robust CAGR of 15.7% through 2034. Strong enforcement of data privacy laws, reinforced by national regulations such as the Federal Data Protection Act alongside the EU’s GDPR, is pushing enterprises in the country to adopt highly secure cryptographic solutions. German institutions across sectors are investing in hardware-based encryption to fulfill compliance mandates and to safeguard personally identifiable information (PII). The culture of data security in Germany, combined with growing technological awareness and digital transformation, continues to drive HSM demand and supports the broader growth of the European HSM industry.
Key companies driving the Global Hardware Security Modules Market include Utimaco GmbH, Entrust Corporation, IBM Corporation, and Thales Group. These players are reshaping the security landscape by offering advanced encryption solutions tailored to modern enterprise needs. Leading companies in the hardware security modules space are leveraging strategic initiatives to solidify their market presence.
A key strategy involves investing in the development of cloud-native HSMs that integrate seamlessly with hybrid and multi-cloud platforms, aligning with growing enterprise cloud adoption. Companies are also focusing on expanding their global footprint through partnerships and acquisitions to tap into emerging markets. Strengthening product portfolios with tamper-resistant, FIPS-certified HSMs supports both regulatory compliance and customer trust. Several firms are enhancing interoperability through API support and SDK integration, making HSMs more accessible to developers and security teams.
Comprehensive Market Analysis and Forecast
- Industry trends, key growth drivers, challenges, future opportunities, and regulatory landscape
- Competitive landscape with Porter’s Five Forces and PESTEL analysis
- Market size, segmentation, and regional forecasts
- In-depth company profiles, business strategies, financial insights, and SWOT analysis
This product will be delivered within 2-4 business days.
Table of Contents
Companies Mentioned
- Adweb Technologies
- Amazon Web Services (AWS)
- DINAMO Networks
- ellipticSecure
- Entrust Corporation
- ETAS GmbH
- Fortanix
- Futurex
- IBM Corporation
- Infineon Technologies AG
- JISA Softech Pvt. Ltd.
- Kryptoagile Solutions Pvt. Ltd.
- Kryptus
- Lattice Semiconductor
- Microchip Technology Inc.
- Microsoft Corporation
- Nitrokey
- Securosys SA
- Spyrus
- STMicroelectronics
- Thales Group
- Utimaco GmbH
- Yubico
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 154 |
| Published | June 2025 |
| Forecast Period | 2024 - 2034 |
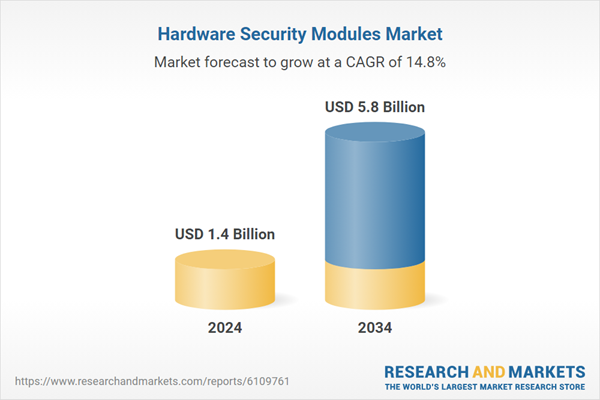
| Estimated Market Value ( USD | $ 1.4 Billion |
| Forecasted Market Value ( USD | $ 5.8 Billion |
| Compound Annual Growth Rate | 14.8% |
| Regions Covered | Global |
| No. of Companies Mentioned | 23 |