Speak directly to the analyst to clarify any post sales queries you may have.
Why cloud-based automated control systems have become a board-level priority for resilience, efficiency, and scalable operations
Cloud-based automated control systems are moving from a niche modernization initiative to a core operational strategy for industries that depend on uptime, quality, and energy efficiency. By shifting control logic, supervisory functions, analytics, and orchestration closer to elastic compute and managed services, organizations aim to shorten engineering cycles, improve system visibility, and scale best practices across distributed assets. This evolution is not simply a technology refresh; it is a structural rethinking of how control environments are designed, secured, operated, and governed.What distinguishes the current cycle is the convergence of industrial automation with cloud-native disciplines such as microservices, infrastructure as code, zero-trust security, and continuous integration and deployment. As a result, decision-makers are no longer debating cloud adoption in abstract terms; they are evaluating specific deployment architectures, data residency implications, and lifecycle costs under real operational constraints. At the same time, workforce realities-retirements, skills gaps, and the need for remote support-are accelerating demand for systems that are easier to manage, validate, and update.
In parallel, the risk environment has intensified. Cyber incidents affecting operational technology have expanded in frequency and sophistication, and regulators have increased scrutiny of critical infrastructure resilience. Consequently, executives are placing equal weight on operational performance and governance maturity, including auditability, change control, and vendor accountability. This executive summary frames the most important shifts reshaping the landscape, highlights the effects of 2025 tariff dynamics in the United States, and distills segmentation, regional, and competitive insights into decision-ready takeaways.
Transformative shifts redefining industrial control: software-defined architectures, governed data pipelines, and security-first operations
The landscape is being reshaped by a decisive move from device-centric automation to software-defined control architectures. Instead of viewing controllers, historians, and SCADA as discrete layers, organizations are adopting composable platforms where control applications can be deployed, updated, and scaled with greater consistency. This shift is expanding the role of virtualization, containerization, and edge-to-cloud orchestration, allowing workloads to be placed where latency, reliability, and compliance requirements are best met.At the same time, industrial data strategies are maturing from simple connectivity projects to standardized data models and governed pipelines. Modern control environments increasingly depend on contextualized data-tags, events, alarms, maintenance records, and quality attributes-integrated with IT systems and analytic services. The result is a stronger focus on interoperability, with customers favoring solutions that reduce integration friction across PLC, DCS, SCADA, MES, and enterprise platforms. Vendors that support open APIs, well-documented connectors, and predictable upgrade paths are gaining preference because they lower long-term complexity.
Security and safety expectations are also transforming buying criteria. Zero-trust principles, identity-centric access, secure remote operations, and rigorous patch management are becoming default requirements rather than differentiators. In response, suppliers are embedding security by design through hardened images, signed updates, continuous monitoring, and improved segmentation between operational networks and cloud endpoints. This is further reinforced by evolving regulatory and insurance requirements that push organizations to demonstrate governance maturity, incident preparedness, and vendor risk management.
Finally, commercial models are shifting alongside technology. Subscription licensing, outcome-oriented services, and managed offerings are changing how value is captured and how procurement evaluates total cost. Customers are increasingly seeking partners who can support multi-year modernization roadmaps, not only deliver products. As these forces converge, the market is moving toward platforms that blend deterministic control needs with cloud-native agility, enabling continuous improvement without compromising reliability.
How 2025 United States tariffs are reshaping sourcing, retrofit strategies, and deployment sequencing for cloud-enabled control programs
United States tariff dynamics in 2025 are influencing cloud-based automated control system programs through equipment cost structures, sourcing strategies, and project sequencing. While many cloud services are delivered digitally, industrial control environments still rely heavily on physical components such as controllers, industrial PCs, network switches, gateways, sensors, panels, and power-related hardware. Tariff pressure affecting industrial electronics and related inputs can raise landed costs, complicate procurement timelines, and increase the importance of supplier diversification.One immediate effect is a heightened emphasis on lifecycle extension and hybrid retrofits. When hardware refresh costs rise or delivery risk increases, organizations tend to preserve installed base assets longer, adding cloud-connected gateways, protocol converters, and secure remote access layers to achieve incremental improvements without full rip-and-replace. This favors architectures that can integrate with legacy PLC and DCS environments while progressively layering higher-level orchestration, analytics, and fleet management. In this context, vendors that provide validated compatibility, robust edge management, and clear migration paths are better positioned.
Tariffs also affect where value is allocated within modernization budgets. As physical bill-of-materials costs increase, executives may shift investment toward software and services that deliver faster operational returns-such as alarm rationalization, predictive maintenance enablement, and energy optimization-provided they can be deployed with minimal disruption. Meanwhile, system integrators and OEMs may need to reprice projects, renegotiate contracts, or adopt more modular designs to control risk. Procurement organizations are responding by tightening supplier qualification criteria and requiring clearer commitments on availability, lead times, and substitution options.
Over time, tariff-related uncertainty can accelerate strategic localization and dual-sourcing. Organizations with multi-site footprints may standardize on a smaller set of approved components to improve negotiating leverage, yet they may also qualify alternate suppliers to reduce single-country exposure. This creates a premium for platforms that remain hardware-agnostic and that support configurable, standards-based connectivity. Taken together, 2025 tariffs are less about slowing cloud adoption and more about reshaping the pathways to it-pushing the industry toward pragmatic hybrid deployments, resilient supply strategies, and designs that decouple software innovation from hardware volatility.
Segmentation insights that explain who adopts which cloud control capabilities first, and why architecture choices differ by use case
Segmentation reveals that adoption patterns differ sharply depending on the component of the control stack being modernized and the operational constraints of the end user. Across solutions spanning programmable logic controllers, distributed control systems, supervisory control and data acquisition, human-machine interfaces, manufacturing execution systems, and industrial internet of things platforms, buyers are seeking clearer boundaries between real-time control and higher-level optimization. PLC and DCS environments remain anchored in deterministic performance and validated reliability, so cloud enablement often appears first through centralized engineering workflows, standardized configuration management, and secure remote operations rather than relocating core control logic.In contrast, SCADA, HMI, and historian-adjacent capabilities are being redesigned to exploit cloud scalability, especially for multi-site visibility and analytics. Organizations managing fleets of assets-such as pumping stations, substations, or remote production lines-are adopting cloud-hosted supervisory layers that unify alarms, events, and performance indicators across geographies. This segmentation also highlights a growing preference for thin-client visualization and role-based access, which reduces local maintenance burdens and improves consistency of operator experiences.
When examined through deployment mode-public cloud, private cloud, and hybrid cloud-the strongest strategic emphasis is on hybrid, because it reconciles latency sensitivity, safety requirements, and data governance with the flexibility of cloud services. Public cloud is frequently chosen for non-critical analytics, cross-site benchmarking, and application lifecycle tooling, while private cloud is favored where strict compliance, deterministic performance, or air-gapped requirements dominate. The segmentation underscores that successful programs define which workloads can move, which must remain local, and how synchronization and failover are managed.
Enterprise size segmentation-small and medium enterprises versus large enterprises-shows differences in capability and risk tolerance. SMEs tend to value packaged solutions, rapid deployment, and managed services that reduce the need for specialized OT cyber and cloud engineering talent. Large enterprises prioritize standardization across sites, integration with enterprise identity and governance tooling, and vendor roadmaps that support long-term scalability. Finally, industry vertical segmentation across manufacturing, oil and gas, chemicals, energy and utilities, building automation, food and beverage, pharmaceuticals, automotive, and water and wastewater illustrates that regulatory burden, batch versus discrete processes, and criticality of uptime shape technology choices. Highly regulated or safety-critical environments typically demand stronger validation, documentation, and change control, while discrete manufacturing often pushes faster toward cloud-connected optimization and data-driven continuous improvement.
Regional insights showing how regulation, infrastructure maturity, and industrial priorities shape cloud-based control adoption worldwide
Regional dynamics show that cloud-based automated control initiatives are strongly shaped by industrial composition, regulatory expectations, and the maturity of digital infrastructure. In North America, modernization is frequently driven by the need to secure remote access, address aging infrastructure, and standardize operations across multi-site enterprises. Buyers in this region often prioritize cybersecurity assurance, integration with existing control assets, and clear vendor accountability, reflecting both threat realities and governance expectations.In Europe, the conversation is closely tied to energy efficiency, sustainability reporting, and stringent data protection and safety norms. Many organizations pursue cloud-connected control architectures to support energy optimization, emissions measurement, and audit-ready operational documentation. Consequently, solutions that provide granular access control, strong data governance, and support for compliance-aligned operational workflows tend to resonate. Cross-border operations also encourage standardized platforms that can be replicated while meeting local requirements.
Asia-Pacific presents a wide spectrum of adoption patterns, from advanced smart manufacturing and high-density electronics production to rapidly expanding industrial bases seeking scalable automation. In faster-growing industrial corridors, the focus often lands on speed of deployment, operational consistency, and workforce augmentation through remote support and guided operations. Cloud-enabled supervisory systems and IIoT platforms are frequently leveraged to connect new lines quickly and to build data foundations for performance improvement.
In the Middle East, automation investments commonly align with national industrial diversification agendas and large-scale infrastructure projects. Reliability in harsh environments, operational continuity, and centralized oversight across distributed assets are recurring themes. Cloud-connected monitoring and asset performance management often serve as stepping stones toward deeper control modernization.
In Africa and South America, adoption is shaped by a combination of infrastructure variability, the need for resilient operations, and a strong return-on-effort mindset. Organizations frequently prioritize solutions that can tolerate intermittent connectivity, simplify maintenance, and provide measurable operational benefits without extensive reengineering. Across these regions, architectures that blend edge autonomy with periodic cloud synchronization can be especially practical, enabling modernization even where network conditions or capital constraints limit more aggressive migration paths.
Key company insights on competition: platform cohesion, partner ecosystems, lifecycle services, and the rising premium on trust
Competitive positioning in cloud-based automated control systems increasingly depends on a vendor’s ability to unify OT reliability with IT-grade scalability and governance. Leading companies differentiate through platform coherence-how well their control, visualization, data management, and analytics components operate together-and through the clarity of their reference architectures for edge, hybrid, and cloud deployments. Buyers are rewarding vendors that can demonstrate proven patterns for high availability, deterministic performance at the edge, and controlled change management across distributed sites.Another major axis of differentiation is ecosystem strength. Because most customers operate heterogeneous environments, vendor claims matter less than integration reality. Companies that maintain strong partnerships with hyperscale cloud providers, industrial PC and gateway suppliers, and system integrators are better able to deliver end-to-end outcomes. Equally important is the quality of developer tooling, documentation, and support for open standards, which reduces integration cost and accelerates time to value.
Services capability has become inseparable from product competitiveness. Organizations want assistance with OT cybersecurity assessments, network segmentation, identity integration, migration planning, and validation procedures. Vendors that offer packaged modernization roadmaps, managed services, and lifecycle support can reduce operational risk for customers that lack deep in-house expertise. In addition, solution providers that help customers build governance-role-based access, audit trails, backup and recovery, and incident response playbooks-are increasingly favored in regulated and critical environments.
Finally, trust is emerging as a hard competitive advantage. Buyers are scrutinizing software supply-chain practices, vulnerability disclosure policies, and the cadence and safety of updates. Vendors that can provide transparent security posture, clear commitments around support lifecycles, and practical guidance for patching in OT environments are strengthening their position. As procurement becomes more risk-aware, companies that align technology innovation with operational assurance are best placed to win and retain long-term control platform relationships.
Actionable recommendations to modernize control safely: workload placement rules, zero-trust operations, interoperability, and lifecycle-ready procurement
Industry leaders can strengthen outcomes by treating cloud-based control as a program, not a product. The first priority is to define workload placement principles that explicitly separate deterministic control requirements from supervisory, analytic, and engineering workflows. By documenting latency tolerance, safety impact, and availability targets per function, organizations can align teams on what can move to the cloud, what must remain at the edge, and what should stay on-premises under stricter governance.Next, leaders should operationalize security and change control early. Implement identity-centric access with least privilege, enforce strong segmentation between OT networks and cloud entry points, and standardize secure remote access patterns that are auditable by default. In parallel, adopt versioned configuration management and controlled release processes for control applications and supervisory software so that improvements do not introduce unplanned downtime. This approach reduces friction between engineering teams who need agility and operations teams who require stability.
A third recommendation is to invest in interoperability and data quality rather than one-off connectivity. Standardize tag naming, asset models, and event taxonomies to make cross-site analytics and benchmarking meaningful. Where possible, select solutions that provide open APIs and well-supported connectors, and ensure that data pipelines preserve context from the control layer through to enterprise systems. This makes modernization durable and reduces dependence on custom integration.
Finally, leaders should align procurement and operating models with the new lifecycle reality. Cloud-connected environments evolve continuously, so contracts should clarify responsibilities for patching, vulnerability handling, support timelines, and service-level expectations. Build internal capability through targeted training for OT engineers on cloud concepts and for IT teams on control constraints. By combining clear architecture rules, security discipline, data governance, and lifecycle-ready commercial structures, organizations can modernize faster while protecting safety, quality, and uptime.
Research methodology built for decision-grade clarity: scoped taxonomy, triangulated validation, and practitioner-led synthesis across segments
The research methodology applies a structured approach to understand technology patterns, adoption drivers, and competitive positioning in cloud-based automated control systems. It begins with defining the market scope and taxonomy, ensuring consistent interpretation of what constitutes cloud-based control capabilities versus adjacent categories such as pure analytics, standalone connectivity, or traditional on-premises automation without cloud integration. This step frames the segmentation logic and ensures that subsequent analysis compares like with like.Next, the study leverages extensive secondary research to map vendor offerings, platform capabilities, partnership ecosystems, and industry-specific requirements. Publicly available technical documentation, product literature, regulatory guidance, standards publications, cybersecurity advisories, and credible industry communications are reviewed to establish an evidence-based baseline. This is complemented by continuous monitoring of product updates, acquisitions, and partnership announcements to reflect the fast-evolving nature of the space.
Primary research is then used to validate assumptions and capture practitioner perspectives. Interviews and structured discussions with stakeholders such as automation engineers, plant operations leaders, OT security specialists, system integrators, and vendor representatives help clarify real-world adoption barriers, architecture preferences, and implementation lessons. The methodology emphasizes triangulation, comparing insights across different participant roles and industries to reduce bias and ensure that findings reflect operational realities.
Finally, insights are synthesized through a segmentation and regional lens, connecting technology choices to practical constraints such as latency, compliance, skills availability, and supply-chain conditions. Quality checks are applied to maintain internal consistency, avoid unsupported claims, and ensure that conclusions remain grounded in observable industry behavior and validated stakeholder input. The result is a decision-oriented view designed to support strategy, vendor evaluation, and roadmap planning.
Conclusion that connects architecture, governance, and external pressures into a pragmatic path for cloud-based control modernization
Cloud-based automated control systems are entering a phase where architectural discipline and governance maturity matter as much as innovation speed. The most successful organizations are those that modernize in layers, preserving deterministic control at the edge while using the cloud to standardize engineering workflows, improve visibility, and scale optimization across sites. As platforms converge and ecosystems deepen, buyers are increasingly selecting solutions that reduce integration friction and provide secure, auditable operations.The operating environment in 2025 adds urgency and complexity. Tariff-driven hardware volatility, rising cyber risk, and tighter compliance expectations are pushing leaders toward hybrid architectures, resilient sourcing strategies, and lifecycle-centric procurement. Meanwhile, segmentation and regional patterns reinforce that there is no single migration path; adoption depends on criticality, regulatory burden, infrastructure maturity, and organizational capability.
Ultimately, cloud-based control is best understood as a long-term transformation of how industrial systems are built and managed. Organizations that define workload placement rules, embed zero-trust practices, invest in interoperable data foundations, and align contracts with continuous lifecycle realities will be better positioned to realize operational gains without compromising safety, quality, or reliability.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
18. China Cloud-Based Automated Control System Market
Companies Mentioned
The key companies profiled in this Cloud-Based Automated Control System market report include:- ABB Ltd.
- Advantech Co., Ltd.
- Amazon Web Services, Inc.
- Beckhoff Automation GmbH & Co. KG
- Bosch Rexroth AG
- Emerson Electric Co.
- FANUC Corporation
- General Electric Company
- Google LLC
- Honeywell International Inc.
- IBM Corporation
- Microsoft Corporation
- Mitsubishi Electric Corporation
- National Instruments Corporation
- Omron Corporation
- Rockwell Automation, Inc.
- SAP SE
- Schneider Electric SE
- Siemens AG
- Yokogawa Electric Corporation
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 195 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
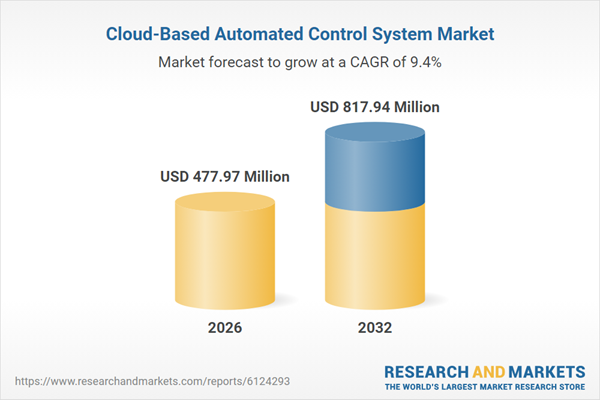
| Estimated Market Value ( USD | $ 477.97 Million |
| Forecasted Market Value ( USD | $ 817.94 Million |
| Compound Annual Growth Rate | 9.4% |
| Regions Covered | Global |
| No. of Companies Mentioned | 21 |