Speak directly to the analyst to clarify any post sales queries you may have.
Why electronic key cabinet management is becoming a core pillar of physical access governance, auditability, and operational resilience
Electronic key cabinet management systems have moved from being a niche security accessory to a foundational control point for physical access governance. As organizations operate across more sites, rely on more contractors, and face tighter accountability expectations, the simple act of issuing, tracking, and returning keys has become a measurable risk surface. Lost keys, unmanaged duplicates, and informal sign-out practices can quietly undermine even the most sophisticated perimeter controls.At the same time, facilities and security teams are being asked to do more with less. They must maintain availability for legitimate users while proving that access was appropriate, time-bound, and traceable. This is where modern electronic key cabinets-paired with software that captures identity, authorization, and audit trails-deliver value beyond storage. They create an enforceable chain of custody for high-impact assets such as master keys, vehicle keys, restricted-area keys, and keys tied to safety-critical infrastructure.
In today’s environment, buyers are also thinking about user experience and operational throughput. A well-designed solution reduces bottlenecks at shift changes, supports self-service retrieval within policy, and reduces administrative overhead through automated permissions, alerts, and reporting. Consequently, executive stakeholders increasingly view these systems as part of a broader physical security ecosystem that must integrate with identity, access control, incident management, and compliance workflows.
This executive summary synthesizes the market’s most decision-relevant dynamics, focusing on how solutions are evolving, what external forces are reshaping procurement and deployment, where demand patterns differ by region, and how leading providers are positioning their offerings. The goal is to help readers translate market change into practical, near-term decisions about requirements, vendor evaluation, and implementation planning.
From locked storage to integrated access orchestration: the technology and buyer expectations reshaping key control programs worldwide
The landscape is undergoing a clear shift from “secure storage” to “policy-driven access orchestration.” Buyers increasingly expect cabinets to function as intelligent endpoints that enforce rules-who can access which key, under what conditions, and with what escalation path if a key is overdue. This shift is driven by the need to reduce reliance on manual oversight and to make accountability routine rather than episodic.Another transformative change is the tightening linkage between identity and physical key control. Instead of treating key issuance as a local facility process, organizations are connecting cabinets to centralized identity systems so that permissions follow role changes, onboarding, and offboarding. As a result, access policies can be updated quickly across locations, and risk exposure from delayed deprovisioning is reduced. This integration mindset also extends to video verification, visitor management, and incident response systems, creating a more unified security narrative.
Cloud-enabled management is also reshaping expectations. Central dashboards, remote policy updates, and fleet-wide reporting are becoming more important for multi-site operators that want standardization without constant on-site administration. That said, the shift is not uniform: regulated and critical environments often maintain strong preferences for on-premises control, segmented networks, or hybrid architectures. Vendors are responding by emphasizing configurable deployment models and clearer data governance.
Operationally, organizations are demanding systems that support high-velocity workflows. Industries with shift-based staffing and large contractor populations need fast authentication, intuitive retrieval, and clear exception handling. Consequently, usability and reliability-door actuation, power resilience, offline modes, and rapid recovery-are increasingly scrutinized alongside security features. Solutions are also being evaluated for how well they reduce friction: automated reminders, escalation for overdue keys, and reporting that fits compliance audits without excessive manual compilation.
Finally, market conversations are expanding from “keys” to “assets.” Many deployments now include the management of related items such as access cards, radios, tools, and shared equipment that require chain-of-custody accountability. This reflects a broader trend: organizations prefer platforms that can scale from a key cabinet use case to a wider secure asset management strategy without requiring a parallel system for each asset type.
How United States tariffs in 2025 are reshaping hardware sourcing, pricing discipline, and deployment timelines for electronic key cabinets
United States tariff actions taking effect in 2025 are expected to influence procurement decisions for electronic key cabinet management systems primarily through hardware cost pressure, sourcing reconsiderations, and lead-time risk management. Because cabinets combine metal enclosures, electromechanical components, sensors, embedded controllers, and sometimes specialized readers and displays, tariff exposure can appear across multiple bill-of-material categories rather than in a single easily substituted part.In response, buyers are likely to see more frequent price reviews and shorter quote validity windows, particularly for projects with phased rollouts. Even when vendors do not explicitly attribute increases to tariffs, margin protection strategies often surface as revised configuration pricing, shipping and logistics adjustments, or changes to included accessories. Therefore, procurement teams are increasingly requesting transparency on component origin, alternative configurations, and the conditions under which pricing may be revisited.
Tariffs can also affect deployment timelines. If manufacturers adjust sourcing to reduce exposure-moving between regions for sheet metal fabrication, electronic subassemblies, or final assembly-qualification cycles and logistics can introduce delays. For security and facilities programs that are tied to compliance deadlines, the practical impact is that project plans need more contingency for delivery, spares availability, and service parts replenishment.
These tariff dynamics are likely to accelerate a shift toward modularity and standardization. Vendors that can offer interchangeable reader modules, flexible communication options, and cabinets that accept a range of locking mechanisms may reduce dependency on any single constrained component stream. Similarly, organizations may prioritize platforms that can start with a smaller footprint and expand incrementally, allowing them to proceed despite budget uncertainty while preserving a path to scale.
Contract structure becomes more strategic under tariff volatility. Buyers are increasingly motivated to negotiate clearer terms around price adjustments, service-level commitments for replacement components, and defined alternatives if a specified configuration becomes difficult to source. In parallel, some organizations may favor suppliers with domestic assembly, diversified supply chains, or regional distribution networks that reduce cross-border exposure and improve fulfillment predictability.
Segmentation signals that buyers are optimizing for deployment model, identity assurance, cabinet scalability, and workflow intensity - not just hardware features
Across offering types, demand patterns diverge between organizations looking for integrated solutions that bundle cabinet hardware with management software and those that want software-first control layered onto existing storage practices. This distinction often aligns with program maturity: first-time adopters tend to prefer cohesive, turnkey deployments, while mature programs focus on interoperability, standard APIs, and the ability to harmonize key control across varied sites and legacy equipment.When viewed through deployment preferences, cloud-managed approaches resonate with multi-site operators seeking centralized policy control and consolidated reporting, while on-premises deployments remain compelling in environments with strict network segmentation, data residency requirements, or low tolerance for external dependencies. Hybrid approaches, combining local control for availability with centralized visibility, are increasingly selected by organizations that need both compliance-grade audit trails and operational resilience when connectivity is constrained.
Authentication choices create another meaningful split in buying behavior. PIN-based workflows remain common in cost-sensitive and high-throughput settings, but demand is rising for stronger identity assurance using badges, smart cards, or biometric options where accountability and non-repudiation are critical. Importantly, segmentation by authentication method is less about technology preference and more about aligning assurance levels with risk-master keys, vehicle fleets, and restricted infrastructure typically justify stronger user verification.
Cabinet capacity and form factor segmentation often reflects the operational footprint of the key ecosystem. Smaller cabinets and key control points are selected for satellite sites and departmental deployments where the priority is replacing informal sign-out processes. Larger, modular, or expandable configurations appear in campus-like environments, distribution hubs, and central facilities where key volume, multi-shift access, and frequent exceptions require durable throughput and clear escalation handling.
Industry-driven segmentation highlights that use-case intensity varies widely. Sectors with high contractor turnover and frequent handoffs emphasize rapid provisioning, intuitive user interfaces, and automated overdue enforcement. Highly regulated environments prioritize tamper evidence, granular role-based access, immutable audit trails, and disciplined reporting. Meanwhile, organizations managing fleets or shared equipment often look for systems that can tie key issuance to asset status and operational readiness, bridging security and operations.
Finally, segmentation by buyer role shapes evaluation criteria. Security leadership tends to focus on policy enforcement, audit readiness, and integration with broader access governance. Facilities and operations teams emphasize uptime, ease of administration, and workflow speed. IT stakeholders prioritize identity integration, network security posture, and maintainability. Winning solutions typically demonstrate credible value across these stakeholder priorities rather than optimizing for a single lens.
Regional adoption patterns reflect differences in compliance pressure, infrastructure investment, and multi-site operational complexity across major geographies
In the Americas, adoption is strongly influenced by enterprise standardization initiatives and multi-site operational models, particularly where fleets, distributed facilities, and contractor-heavy maintenance activities make key accountability a recurring challenge. Organizations often prioritize integration with established badge ecosystems and seek solutions that can be rolled out consistently across sites while still accommodating local exceptions and varied facility layouts.Across Europe, the emphasis frequently centers on demonstrable compliance, privacy-aware identity practices, and disciplined auditability. Buyers commonly expect strong role-based controls, detailed reporting, and clear data handling safeguards. In addition, regional diversity in languages, procurement frameworks, and facility types increases the value of configurable platforms that can support standardized governance without forcing uniform workflows that conflict with local operational realities.
In the Middle East, investment in large-scale infrastructure, commercial developments, and high-visibility venues supports demand for strong physical security programs where key control is treated as part of an integrated security posture. Buyers often seek systems that combine robust hardware, reliable operation in demanding environments, and alignment with broader security modernization efforts that include access control, surveillance, and centralized command capabilities.
Across Africa, implementation priorities frequently balance security needs with practical constraints such as distributed geographies, variable connectivity, and maintenance logistics. Solutions that offer resilient local operation, straightforward administration, and durable construction can be advantageous, especially when service coverage and parts availability influence total program reliability as much as feature depth.
In Asia-Pacific, growth in industrial capacity, logistics networks, and dense urban facilities supports broad interest in scalable key control. Many organizations value centralized visibility for multi-site operations, but they also weigh cost, deployment speed, and interoperability with local security infrastructure. As a result, demand can span from pragmatic, fast-to-deploy cabinets for high-throughput sites to advanced identity-integrated deployments in highly regulated or high-risk environments.
Overall, regional differences are less about whether key control is needed and more about how programs are implemented: integration depth, deployment architecture, and the operational maturity of security governance determine which solution profiles resonate most strongly.
Competitive differentiation is moving beyond cabinet build quality toward integration depth, service reach, modular platforms, and cybersecurity credibility
The competitive environment is shaped by providers that differentiate through hardware durability, software sophistication, and the breadth of integration options. Some companies lead with robust cabinet engineering-prioritizing physical resilience, reliable locking mechanisms, and high availability-while others focus on software-led governance, emphasizing policy configuration, reporting depth, and centralized administration across many cabinets and locations.A growing point of differentiation is integration readiness. Vendors that offer mature connectors or well-documented APIs for identity providers, access control platforms, and security operations workflows are better positioned for enterprise deployments. This matters because electronic key cabinet management systems increasingly need to participate in broader governance processes such as role changes, credential lifecycle management, incident review, and compliance audits.
Service and deployment capability also separates strong contenders from feature-rich but operationally constrained offerings. Buyers scrutinize implementation support, training quality, and the ability to sustain deployments over time through firmware updates, security patching, and replacement part logistics. For global or distributed programs, partner ecosystems and regional service coverage can be as decisive as the product itself.
Product strategy is also evolving toward modularity and platform extensibility. Many providers are aligning cabinets, software, and authentication options into configurable families rather than one-size-fits-all products. This helps customers start with a targeted use case-such as a fleet depot or a secure maintenance shop-and then expand to additional sites, higher assurance authentication, or adjacent asset-control scenarios without replatforming.
Finally, vendors are increasingly expected to demonstrate cybersecurity discipline. As cabinets become networked endpoints, buyers evaluate secure authentication, encryption practices, update mechanisms, logging integrity, and administrative controls. Providers that can clearly explain their security model and support risk assessments tend to progress more smoothly through enterprise procurement and IT review.
Leadership actions that turn key control into measurable governance: policy-first design, integration-driven selection, and resilience-by-default deployment
Industry leaders can strengthen outcomes by treating key control as a governance program rather than a device purchase. That begins with mapping key-related risk scenarios-overdue keys, shared credentials, contractor access, and emergency overrides-and translating them into explicit policies that the system can enforce. When policies are defined first, technology selection becomes clearer and stakeholder alignment improves.Procurement and security teams should prioritize integration requirements early. Aligning the cabinet system with identity management, badge credentials, and access control platforms reduces manual administration and improves audit consistency. In parallel, organizations should define reporting needs in the language of audits and investigations, ensuring the system can produce time-stamped, user-linked events, exception logs, and evidence trails without extensive manual reconciliation.
Operational success depends on designing for the realities of shift changes and high-throughput environments. Leaders should validate retrieval and return workflows under peak conditions, including how the system handles exceptions such as overdue keys, lost keys, or urgent access requests. Establishing escalation paths-notifications, supervisor approvals, or temporary access windows-helps maintain availability while keeping accountability intact.
Resilience planning should be explicit in any deployment decision. Leaders should evaluate power backup options, offline operation behavior, and recovery procedures, then stock appropriate spares for high-impact sites. Additionally, a structured rollout approach-pilot, refine policies, train, and then scale-reduces user friction and increases compliance. Training should emphasize not only “how to use the cabinet,” but also why chain-of-custody discipline matters to safety, security, and operational continuity.
Finally, cybersecurity and lifecycle management should be treated as first-class requirements. Leaders should confirm how updates are delivered, who can administer the system, how credentials are protected, and how logs are retained and reviewed. Selecting a vendor with clear lifecycle support and disciplined security practices reduces long-term risk and avoids costly retrofits as governance expectations evolve.
Methodology built for decision usefulness: practitioner validation, vendor and partner inputs, and a comparable framework across solutions and deployments
This research was developed through a structured approach designed to reflect real buyer requirements, supplier positioning, and operational deployment realities. The process began with defining the solution scope for electronic key cabinet management systems, including the functional boundaries between cabinet hardware, management software, authentication mechanisms, and integration layers that connect to broader physical security and identity ecosystems.Primary research activities focused on capturing practitioner and supplier perspectives on use cases, procurement criteria, and implementation challenges. Inputs were gathered from stakeholders spanning security leadership, facilities and operations management, and technology teams, as well as from vendors and channel partners involved in design, deployment, and ongoing service. These discussions were used to validate which capabilities most influence selection, where deployments commonly succeed or stall, and how requirements differ by environment and risk profile.
Secondary research complemented these insights by examining product documentation, regulatory and compliance themes shaping physical access governance, and publicly available information on vendor offerings and partnerships. This step helped triangulate feature claims, clarify deployment models, and understand how systems are positioned within broader security modernization initiatives.
Analysis techniques emphasized consistency and comparability across vendors and buyer segments. Solution attributes were organized into a common evaluation framework covering governance features, authentication strength, integration readiness, operational resilience, administrative experience, and lifecycle support. The findings were then synthesized to highlight practical decision points, common trade-offs, and adoption patterns across segments and regions.
Throughout, the methodology prioritized factual alignment and decision usefulness. The intent is to provide an executive-ready view that supports requirements definition, vendor shortlisting, and implementation planning without relying on speculative assumptions or unsupported conclusions.
Closing perspective: electronic key cabinet management is now a governance platform choice that links security assurance with daily operational efficiency
Electronic key cabinet management systems are increasingly central to how organizations prove and enforce physical access accountability. What was once a localized storage control is now an integrated governance mechanism that must align with identity, compliance, and operational continuity. As expectations rise, buyers are evaluating these systems not only for security features, but also for how well they fit real workflows and enterprise architectures.The market is being shaped by platform thinking, integration maturity, and the practical realities of deployment at scale. Organizations are gravitating toward solutions that can standardize policy across sites, support appropriate authentication strength, and generate audit-ready evidence without administrative strain. In parallel, supply chain and tariff pressures are encouraging procurement discipline, modular configurations, and stronger vendor commitments on parts availability and lifecycle support.
For decision-makers, the path forward is clearest when key control is treated as a program with defined policies, measurable outcomes, and cross-functional ownership. Solutions that combine enforceable access rules, resilient operation, and integration into broader security workflows are best positioned to deliver durable value. With the right approach, key control becomes a catalyst for stronger governance, reduced operational disruption, and improved confidence in physical security controls.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
16. China Electronic Key Cabinet Management System Market
Companies Mentioned
The key companies profiled in this Electronic Key Cabinet Management System market report include:- Allegion plc
- ASSA ABLOY AB
- Brivo Systems LLC
- Dormakaba Holding AG
- KeyTrak LLC
- Morse Watchmans, Inc.
- Nedap N.V.
- nVent Electric plc
- SALTO Systems S.L.
- SimonsVoss Technologies GmbH
- Traka
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 190 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
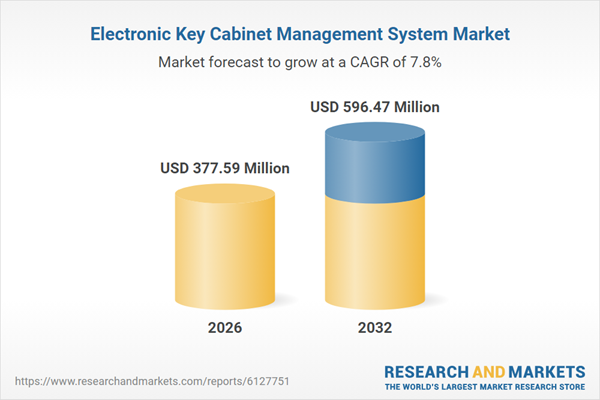
| Estimated Market Value ( USD | $ 377.59 Million |
| Forecasted Market Value ( USD | $ 596.47 Million |
| Compound Annual Growth Rate | 7.8% |
| Regions Covered | Global |
| No. of Companies Mentioned | 12 |