Speak directly to the analyst to clarify any post sales queries you may have.
The CMMC consulting service market is rapidly evolving as organizations in the defense sector prioritize structured compliance and cyber maturity to secure sensitive data and sustain government partnerships. Senior leaders can leverage in-depth market intelligence to align compliance strategies with broader business and regulatory objectives.
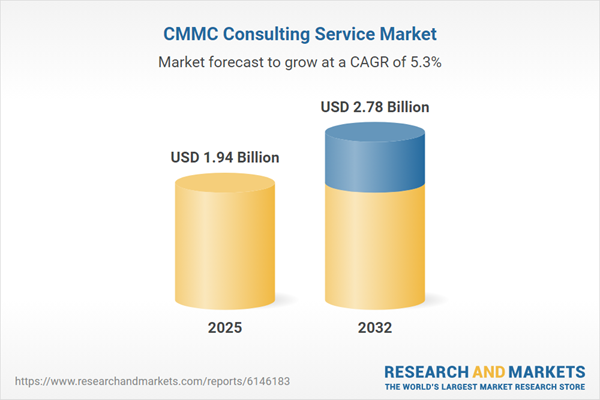
Market Snapshot: CMMC Consulting Service Market Size and Growth
The CMMC consulting service market grew from USD 1.84 billion in 2024 to USD 1.94 billion in 2025. With a projected CAGR of 5.27%, it is expected to reach USD 2.78 billion by 2032. This momentum reflects increasing adoption across defense contractors and related verticals, underscoring the sector’s strategic importance for long-term regulatory compliance and supply chain resilience.
Scope & Segmentation of the CMMC Consulting Service Market
This comprehensive analysis covers a wide array of CMMC consulting service offerings, pricing frameworks, deployment options, and industries served. The research delves into segmentation by region and business size, providing actionable insight into the market’s diversity and complexity.
- Service Offerings: Certification support and audit preparation, compliance roadmapping, gap analysis and readiness assessment, managed ongoing compliance, remediation and implementation support, training, and awareness programs.
- Pricing Models: Fixed fee, milestone-based, and subscription pricing structures.
- Compliance Levels: Levels 1, 2, and 3 based on NIST and DoD benchmarks.
- Deployment Models: Cloud—including both private and public cloud—alongside on-premise options for enhanced data control.
- End Users: Aerospace and defense, critical infrastructure, healthcare and biomedical, IT and telecommunications, and research and educational institutions.
- Organization Sizes: Large, medium, and small enterprises, each requiring distinct consulting engagement models.
- Regional Coverage: Americas (North America, Latin America), Europe, Middle East & Africa, and Asia-Pacific, with further breakdowns by major economies such as the United States, Germany, China, and India.
- Leading Companies: Includes Aethon Security Consulting, BAE Systems, Deloitte Consulting, Booz Allen Hamilton, KPMG, and others driving adoption and innovation within the CMMC ecosystem.
Key Takeaways for Decision-Makers
- The shift toward ongoing, adaptive cybersecurity maturity models is reshaping decision frameworks for defense contractors and their suppliers.
- Innovative technology integration—such as zero trust architecture and automated compliance tooling—remains a primary differentiator among top consulting partners.
- Consulting service portfolios are expanding to address both technical security controls and strategic, executive-level compliance planning.
- Regional regulatory differences demand tailored approaches, with U.S. organizations focusing on federal mandates while EMEA and Asia-Pacific respond to local and international standards.
- Smaller enterprises are increasingly seeking scalable, cost-effective consulting models to match digital transformation efforts within budget constraints.
- Collaborative partnerships between consultants and technology vendors are improving readiness and shortening certification cycles across all organization sizes.
Tariff Impact on CMMC Consulting Services
Recent U.S. tariff changes are influencing technology and service procurement strategies for defense contractors. As import duties on software and critical components rise, consulting budgets face tighter scrutiny. Organizations are adapting by reconfiguring global supply chains, shifting some operations to domestic or partner-friendly regions, and exploring cloud-based architectures to manage compliance efficiently. This shift further emphasizes due diligence in vendor selection and the requirement for robust scenario planning in consulting engagements.
Research Methodology & Data Sources
The report integrates qualitative and quantitative research, including expert interviews, structured surveys, and review of policy documentation. Thematic content analysis, benchmarking, and scenario modeling support the accuracy and depth of findings, with data triangulation and peer review ensuring objectivity.
CMMC Consulting Service Market: Why This Report Matters
- Enables executive teams to benchmark consulting options, pricing, and service breadth for agile compliance strategy development.
- Provides detailed segmentation and regional intelligence, supporting tailored compliance initiatives in both established and emerging markets.
- Delivers clear recommendations for optimizing technology investments and navigating changing regulatory landscapes, empowering confident decision-making.
Conclusion
The CMMC consulting service market represents a critical enabler of security, contractual eligibility, and operational resilience for organizations within the defense industrial base. Strategic insights from this research equip leaders to anticipate market shifts, streamline compliance processes, and foster enduring value through proactive engagement.
Table of Contents
3. Executive Summary
4. Market Overview
7. Cumulative Impact of Artificial Intelligence 2025
Companies Mentioned
The companies profiled in this CMMC Consulting Service market report include:- Aethon Security Consulting, LLC
- C3 Integrated Solutions, LLC
- Atomus Corporation
- BAE Systems
- Beryllium InfoSec, Inc.
- Booz Allen Hamilton Inc.
- Deloitte Consulting LLP
- Ernst & Young LLP
- Guidehouse Inc.
- ISI Enterprises
- KAMIND IT, Inc.
- KPMG LLP
- KTL Solutions, Inc.
- Leidos, Inc.
- MAD Security, LLC
- Monarch ISC
- MX2 Technology, Inc.
- NeoSystems LLC
- OSIbeyond LLC
- Paragon Cyber Solutions LLC
- Peak InfoSec LLC
- Penacity, LLC
- Point North Networks
- PricewaterhouseCoopers LLP
- Protiviti Inc.
- Resilient IT
- Sentinel Blue
- SoundWay Consulting, Inc.
- TechAxia LLC
- Withum Smith+Brown, PC
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 198 |
| Published | November 2025 |
| Forecast Period | 2025 - 2032 |
| Estimated Market Value ( USD | $ 1.94 Billion |
| Forecasted Market Value ( USD | $ 2.78 Billion |
| Compound Annual Growth Rate | 5.2% |
| Regions Covered | Global |
| No. of Companies Mentioned | 31 |