Speak directly to the analyst to clarify any post sales queries you may have.
Establishing the Imperative to Secure Payment Ecosystems by Introducing Core Drivers Shaping PCI Compliance Strategies and Risk Management
Amid a proliferation of digital payment channels, organizations face mounting pressure to fortify their security posture against sophisticated threats. Payment Card Industry compliance has evolved into a foundational element of enterprise risk management, requiring a nuanced understanding of both regulatory mandates and technological imperatives. As cyber adversaries refine their tactics with advanced malware and social engineering techniques, compliance must extend beyond checklist adherence into a dynamic process that anticipates vulnerabilities before exploitation.Moreover, the convergence of mobile wallets, contactless payments and e-commerce platforms has expanded the attack surface, challenging security teams to maintain consistent controls across distributed environments. This shifting terrain demands a proactive framework where audit and assessment routines integrate seamlessly with real-time monitoring and continuous improvement cycles. Organizations must also consider the strategic value of comprehensive training programs that cultivate a security-first mindset, ensuring personnel at every level recognize and mitigate risk.
Organizations must also collaborate closely with third parties to safeguard the integrity of the payment ecosystem. As supply chain attacks rise, extending compliance requirements to vendors through risk assessments and contractual safeguards is critical. Adopting a risk-based, strategic posture enables leadership to allocate resources effectively, align security investments with organizational risk appetite, and transition from a reactive compliance model to a proactive resilience framework. This holistic foundation empowers enterprises to adapt swiftly to regulatory changes and emerging threats while maintaining customer trust and brand reputation.
Navigating Transformative Shifts in the Payment Security Landscape Fueled by Cutting Edge Technologies and Regulatory Innovations Enhancing Compliance Posture
Rapid technological innovation and shifting regulatory mandates have converged to reshape the payment security landscape over the past year. Emerging cryptographic standards, such as advanced tokenization methods and homomorphic encryption research, are driving organizations to revisit legacy solutions and adopt more agile architectures. Concurrently, the rise of artificial intelligence driven threat detection and behavior analytics offers the promise of real-time anomaly identification, enabling security teams to preempt potential breaches before they escalate.Regulators are also redefining compliance expectations, with new directives emphasizing multi factor authentication, customer identity verification and data privacy harmonization across jurisdictions. The implementation of dynamic authentication protocols is catalyzing investment in secure cloud infrastructures and unified monitoring platforms. Moreover, the maturation of open banking initiatives and API centric payment models has introduced fresh complexities, requiring security teams to collaborate more intimately with development and DevOps functions.
These transformative shifts underscore the imperative for organizations to build adaptive compliance programs that integrate continuous assessment, automation and cross functional governance. By embracing a zero trust philosophy and fostering an innovative culture, enterprises can navigate the evolving terrain with agility. Ultimately, this evolution not only bolsters defense mechanisms but also unlocks new opportunities for secure payment experiences that inspire consumer confidence.
Assessing the Cumulative Implications of United States 2025 Tariff Adjustments on Payment Security Operations and Cost Structures in Compliance Ecosystems
In 2025, adjustments to United States tariff schedules have introduced significant cost considerations for organizations procuring payment security hardware and software. Increased duties on network appliances, encryption modules and specialized security tokens have elevated procurement budgets, compelling stakeholders to reassess vendor contracts and supply chain logistics. These cost pressures can inadvertently constrain modernization initiatives, delaying critical upgrades and potentially exposing legacy systems to heightened risk.Furthermore, strained global trade dynamics have amplified lead times for essential security components, with ripple effects on deployment timelines and project planning. Enterprises are responding by diversifying sourcing strategies, negotiating volume based agreements and exploring localized manufacturing partnerships to mitigate the financial and operational impacts. This shift toward regional supply chain resilience not only addresses immediate cost challenges but also reinforces overall business continuity.
As a result, compliance leaders must integrate tariff related scenario planning into their broader risk management frameworks. By conducting comprehensive impact analyses and stress tests, teams can anticipate budgetary deviations and align procurement cycles with evolving duty structures. Leveraging flexible licensing models and cloud based security offerings provides an additional buffer against hardware cost volatility, enabling organizations to maintain robust compliance postures without overextending capital expenditures.
Uncovering Segmentation Insights Illuminating Service Types Deployment Modes Industries and Organizational Scales Influencing Compliance Adoption Trajectories
Segmentation analysis reveals tailored imperatives across service types and deployment modes. Audit and assessment engagements surface critical vulnerabilities, while consulting partnerships provide clarity on intricate regulatory expectations. Managed services offerings-including antivirus, database security, encryption and monitoring-deliver sustained oversight, whereas software platforms drive automated control workflows and training programs reinforce a security first culture. Deployment strategies range from on premises implementations to hybrid models that preserve existing infrastructure while tapping into private and public cloud elasticity, ensuring compliance objectives align with data residency and performance requirements.End user industries face distinct compliance landscapes. Financial institutions navigate banking, capital markets and insurance mandates, government bodies reconcile federal and local directives, healthcare providers secure hospitals, medical devices and pharmaceutical assets, and retail enterprises integrate protections for both brick and mortar displays and online marketplaces.
Organizational scale further nuances solution adoption. Tier one enterprises often opt for bespoke program designs and comprehensive managed engagements. Mid market operators seek offerings calibrated to lower or upper segments, while small business and micro enterprise segments prioritize modular, pay as you go services. These insights underscore the importance of segmentation in crafting compliance strategies that resonate with varied risk tolerances and operational capabilities.
Evaluating Regional Dynamics Across the Americas Europe Middle East Africa and Asia Pacific to Reveal Critical Trends Shaping Compliance Strategies Globally
Regional dynamics exert a profound influence on compliance imperatives across the global landscape. In the Americas, mature regulatory frameworks and a history of high profile data breaches have driven robust investments in advanced monitoring and multi factor authentication controls. Organizations in this region often lead in piloting next generation tokenization services and embracing real time threat intelligence feeds to preempt potential incursions.Meanwhile, Europe, the Middle East and Africa present a tapestry of divergent regulatory environments, from stringent data privacy directives in the European Union to emerging compliance standards in key Middle Eastern markets. This complex terrain encourages enterprises to adopt harmonized approaches that satisfy diverse legal regimes. PSD2 regulations, for example, have accelerated the shift toward open banking security measures, prompting cross border collaboration on secure APIs and consent management frameworks.
The Asia Pacific region is characterized by rapid digital payment adoption that spans well established economies and fast growing markets. Organizations in developed APAC markets prioritize cloud native compliance architectures and regional data residency mandates, while emerging economies emphasize cost effective managed services and localized support. Across all regions, the interplay between regulation, market maturity and technological adoption dictates how enterprises prioritize investments and tailor compliance architectures to regional nuances.
Highlighting Leading Industry Players Driving Innovation and Excellence in Payment Security Compliance with Strategic Alliances and Technology Advancements
Leading industry players are reshaping the payment security compliance landscape through a combination of innovation, strategic alliances and targeted acquisitions. Established consulting firms are expanding their service portfolios to integrate automated assessment platforms and artificial intelligence driven threat analytics, providing clients with predictive insights that transcend traditional audit methodologies. At the same time, specialist software vendors are partnering with cloud service providers to deliver fully managed compliance solutions that streamline deployment and maintenance across hybrid and multi cloud environments.Partnerships between hardware manufacturers and cybersecurity specialists have given rise to integrated appliances that embed advanced encryption modules and real time monitoring capabilities within a unified management console. These collaborations not only simplify control frameworks but also reduce interoperability challenges by offering end to end visibility across payment channels.
Moreover, forward thinking training institutes are aligning curriculum development with evolving compliance standards, offering on demand and interactive learning modules to upskill security teams. Investment firms have also taken notice, backing emerging startups that focus on novel approaches such as continuous compliance orchestration and decentralized ledger technologies for audit trail management.
By observing the trajectories of these leading entities, enterprises can identify best practices and potential partners to inform their own compliance roadmaps. The competitive dynamics among these organizations illustrate a broader trend toward consolidation of services and increasing emphasis on offering holistic platforms that address every phase of the compliance lifecycle.
Empowering Industry Leaders with Actionable Recommendations to Elevate Payment Security Posture and Streamline Compliance Through Strategic Investments
Industry leaders seeking to fortify their payment security frameworks should adopt a series of targeted strategies that align with both immediate risk reduction and long term resilience. First, integrating continuous monitoring tools that leverage machine learning algorithms can dramatically shorten mean time to detection and response, ensuring that anomalous patterns are flagged and investigated without delay. Complementing this with dynamic tokenization and next generation encryption protocols protects cardholder data in transit and at rest, effectively neutralizing the value of intercepted information.Leaders must also cultivate a security centric culture by embedding compliance objectives into organizational performance metrics. Regular training programs, tabletop exercises and executive briefings ensure that all stakeholders understand their roles in maintaining controls. Partnering with qualified security assessors to conduct periodic gap analyses reinforces accountability and provides an external perspective on program effectiveness.
Investments in cloud native security architectures, coupled with zero trust network segmentation, can streamline compliance workflows while reducing infrastructure overhead. Embracing modular, API driven solutions enables rapid updates in line with evolving standards. Furthermore, businesses should establish cross functional governance forums that include representatives from IT, legal and finance to drive holistic decision making.
Finally, scenario based planning for potential regulatory shifts and supply chain disruptions, including tariff fluctuations and vendor dependencies, prepares organizations to pivot quickly in response to external pressures. By implementing these actionable recommendations, industry leaders can elevate their compliance posture and drive sustainable security improvements across payment ecosystems.
Detailing a Rigorous Research Methodology Underpinned by Comprehensive Data Collection Analysis and Validation to Ensure Robust PCI Compliance Insights
A meticulous research methodology underlies the insights presented in this report, combining primary and secondary data collection to yield a comprehensive view of the compliance ecosystem. Primary research comprised in depth interviews with chief information security officers, qualified security assessors and payment technology architects, capturing firsthand perspectives on emerging threats, operational challenges and solution effectiveness. These interviews were complemented by structured surveys of security practitioners across a broad range of organizations, ensuring that diverse operational realities are represented.Secondary research entailed a systematic review of public regulatory texts, industry white papers and vendor documentation, excluding any proprietary sources from commercial intelligence platforms. This phase involved cross referencing data points to validate accuracy and identify trends that span multiple jurisdictions. Data triangulation techniques were employed to reconcile discrepancies between primary findings and documented policies.
Quantitative analysis of deployment patterns and service adoption rates was supported by scenario modeling to assess the potential impacts of regulatory enhancements and supply chain variables. Qualitative insights were enriched through expert panel discussions, which facilitated deep dives into specific case studies and best practice implementations. A final validation stage engaged third party compliance practitioners to vet the methodology and corroborate key conclusions. This rigorous approach ensures that the findings command confidence and deliver actionable guidance for decision makers.
Synthesizing Key Findings and Strategic Imperatives to Reinforce Payment Security Frameworks and Guide Future Compliance Efforts Amidst Evolving Threats
As the payment security landscape continues to evolve, the integration of advanced technologies, adaptive regulatory frameworks and strategic risk management emerges as the cornerstone of effective compliance programs. This report has highlighted how evolving encryption standards, real time monitoring innovations and shifting tariff environments shape procurement and deployment strategies. It has also underscored the significance of nuanced segmentation across service types, deployment modes, industries and organizational scales in crafting targeted compliance roadmaps.Regional insights reveal that global enterprises must calibrate their approaches to align with localized regulations and market maturity, while reference to leading vendors and solution providers illustrates the growing emphasis on holistic platforms that unify assessment, remediation and ongoing monitoring. Actionable recommendations emphasize the criticality of embedding compliance into corporate governance, leveraging cloud native architectures and sustaining a culture of security awareness.
Ultimately, a proactive, risk based posture that emphasizes continuous improvement and strategic partnerships will enable organizations to navigate emerging threats and regulatory shifts with agility. Decision makers can leverage these findings to reinforce their security frameworks, optimize resource allocations and maintain customer trust in an increasingly complex digital payments environment.
Market Segmentation & Coverage
This research report forecasts revenues and analyzes trends in each of the following sub-segmentations:- Service Type
- Advisory & Remediation
- Compensating Controls
- Control Implementation
- Network Segmentation Design
- Policy & Procedure Development
- Assessment & Audit
- Gap Assessment
- QSA-Led Report on Compliance (ROC)
- Readiness Assessment
- Incident Response & Forensics
- Breach Response & Remediation
- PFI Coordination
- Managed Compliance
- Compliance Reporting
- Continuous Control Monitoring
- Evidence Management
- PCI Program Management Office
- Testing Services
- Application Security Testing
- ASV Vulnerability Scanning
- External Penetration Testing
- Internal Penetration Testing
- Segmentation Testing
- Wireless Testing
- Training & Awareness
- Incident Response Tabletop
- PCI DSS Foundations
- Role-Based Training
- Advisory & Remediation
- Pricing Model
- Fixed Fee
- Outcome-Based
- Subscription
- Tiered Bundles
- Merchant Level
- Level 1
- Level 2
- Level 3
- Level 4
- Use Case
- First-Time Certification
- M&A Integration
- New Channel Launch
- PayFac Enablement
- Platform Modernization/Cloud Migration
- Post-Breach Validation
- SAQ Reduction via Segmentation
- Scope Reduction via Tokenization
- Version Upgrade to PCI DSS v4.0
- Deployment Mode
- Cloud
- Private Cloud
- Public Cloud
- Hybrid
- On Premises
- Physical Infrastructure
- Virtual Infrastructure
- Cloud
- Organization Size
- Large Enterprise
- Tier 1
- Tier 2
- Mid Market
- Lower Mid Market
- Upper Mid Market
- Small and Medium Enterprises
- Micro Business
- Small Business
- Large Enterprise
- Industry Vertical
- E-Commerce
- Education
- Financial Services
- Government & Public Sector
- Healthcare
- Hospitality
- Casinos
- Hotels
- Restaurants & QSR
- Full-Service
- Quick-Service
- Retail
- Convenience & Fuel
- Grocery
- Specialty Retail
- Americas
- North America
- United States
- Canada
- Mexico
- Latin America
- Brazil
- Argentina
- Chile
- Colombia
- Peru
- North America
- Europe, Middle East & Africa
- Europe
- United Kingdom
- Germany
- France
- Russia
- Italy
- Spain
- Netherlands
- Sweden
- Poland
- Switzerland
- Middle East
- United Arab Emirates
- Saudi Arabia
- Qatar
- Turkey
- Israel
- Africa
- South Africa
- Nigeria
- Egypt
- Kenya
- Europe
- Asia-Pacific
- China
- India
- Japan
- Australia
- South Korea
- Indonesia
- Thailand
- Malaysia
- Singapore
- Taiwan
- A-LIGN, LLC
- AT&T Inc.
- Aperia
- Blackbaud, Inc.
- Centraleyes Ltd.
- Coalfire Systems, Inc.
- ControlCase LLC
- Crowe LLP
- Drata Inc.
- Integrity360
- LRQA Group Limited
- Microminder Cybersecurity
- NCC Group plc
- Netsurion LLC
- Nord Security
- OneTrust, LLC
- Optiv Security Inc.
- PCI-PAL PLC
- Qualys, Inc.
- Rapid7 LLC
- Redscan Cyber Security Limited
- RSI Security
- Sattrix Information Security Ltd
- Schellman & Company, LLC
- ScienceSoft USA Corporation
- Scrut Automation Inc.
- SecOps Solution, Inc.
- SecurityMetrics, LLC
- SISA Information Security Pvt. Ltd.
- UL LLC
- URM Consulting Services Ltd.
- Verizon Business Network Services Inc.
- Viking Cloud, Inc.
Table of Contents
3. Executive Summary
4. Market Overview
7. Cumulative Impact of Artificial Intelligence 2025
Companies Mentioned
The companies profiled in this PCI Compliance Services market report include:- A-LIGN, LLC
- AT&T Inc.
- Aperia
- Blackbaud, Inc.
- Centraleyes Ltd.
- Coalfire Systems, Inc.
- ControlCase LLC
- Crowe LLP
- Drata Inc.
- Integrity360
- LRQA Group Limited
- Microminder Cybersecurity
- NCC Group plc
- Netsurion LLC
- Nord Security
- OneTrust, LLC
- Optiv Security Inc.
- PCI-PAL PLC
- Qualys, Inc.
- Rapid7 LLC
- Redscan Cyber Security Limited
- RSI Security
- Sattrix Information Security Ltd
- Schellman & Company, LLC
- ScienceSoft USA Corporation
- Scrut Automation Inc.
- SecOps Solution, Inc.
- SecurityMetrics, LLC
- SISA Information Security Pvt. Ltd.
- UL LLC
- URM Consulting Services Ltd.
- Verizon Business Network Services Inc.
- Viking Cloud, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 182 |
| Published | November 2025 |
| Forecast Period | 2025 - 2032 |
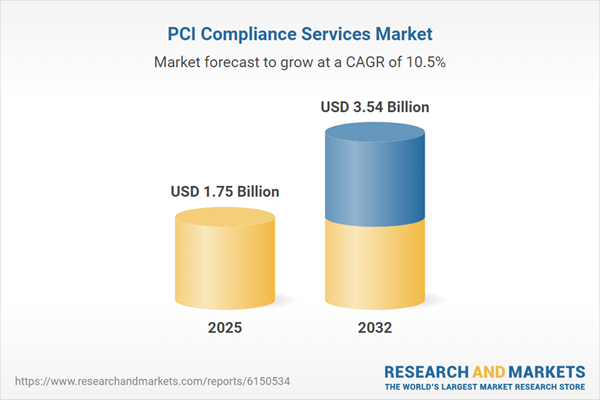
| Estimated Market Value ( USD | $ 1.75 Billion |
| Forecasted Market Value ( USD | $ 3.54 Billion |
| Compound Annual Growth Rate | 10.4% |
| Regions Covered | Global |
| No. of Companies Mentioned | 34 |