Speak directly to the analyst to clarify any post sales queries you may have.
Understanding the critical convergence of technological innovation and regulatory pressures driving the account takeover software landscape
The landscape of digital authentication has reached a critical juncture as organizations strive to protect user credentials against ever more innovative account takeover techniques. Digital transformation initiatives have accelerated enterprise reliance on cloud services, mobile access, and interconnected platforms, heightening exposure to credential-based intrusions. As adversaries deploy automated bots, credential stuffing, and phishing schemes with unprecedented scale and precision, businesses face mounting pressure to adopt robust defensive strategies that can anticipate, detect, and neutralize these incursions in real time.Simultaneously, regulatory bodies worldwide have intensified requirements around identity verification and data protection, underscoring the imperative for comprehensive account theft prevention frameworks. This confluence of technological advancement and compliance mandates has elevated account takeover software from a specialized niche to an essential component of any cybersecurity program. Decision-makers now demand solutions that seamlessly integrate risk-based authentication, machine learning-driven anomaly detection, and frictionless user experience-all while maintaining agility to adapt to emerging threat shades.
Against this backdrop, this executive summary distills the critical drivers, market dynamics, and strategic imperatives shaping the account takeover software environment. By unpacking transformative shifts, tariff impacts, segmentation nuances, regional contrasts, and leading provider strategies, we aim to furnish executives with the clarity needed to navigate an increasingly complex security ecosystem. The following sections outline key insights that inform technology investments, partner selections, and proactive defenses for fortifying digital identities.
Exploring the rapid evolution of threat tactics, deployment architectures, and strategic partnerships redefining account takeover defenses
Recent years have witnessed a dramatic acceleration in the sophistication of account takeover tactics, propelled by advances in artificial intelligence, automation, and the dark web economy. Automated credential stuffing campaigns now leverage large-scale botnets to rapidly test millions of compromised credentials, while deep learning-enhanced phishing schemes craft hyper-personalized messages that evade conventional detection. In response, leading solution providers have embraced adaptive authentication techniques that dynamically adjust challenge levels based on contextual risk signals such as device fingerprinting, geolocation anomalies, and behavioral biometrics.Concurrently, the shift toward cloud-native architectures has redefined deployment and operational paradigms. Software vendors increasingly offer hybrid and multi-cloud models that balance scalability with on-premises control, reflecting a growing recognition that flexible deployment is essential for addressing diverse security postures. Furthermore, the transition from static rule-based engines to continuous, AI-driven monitoring represents a paradigm shift toward predictive threat intelligence, enabling organizations to preemptively thwart account compromise attempts before they escalate into full-scale breaches.
This transformative evolution extends beyond technology to encompass a broad spectrum of ecosystem collaborations. Strategic alliances between identity providers, managed security service firms, and telecommunication carriers have given rise to integrated offerings that streamline implementation and enhance situational awareness. Taken together, these shifts underscore an industry in flux-one where agility, intelligence, and strategic partnerships define the battleground for safeguarding digital identities.
Assessing the aggregated effects of the 2025 U.S. trade tariffs on both hardware dependencies and cloud-native account takeover security models
The imposition of new tariffs by the United States government in 2025 has introduced a multifaceted impact on the global supply chains and pricing structures underlying account takeover software solutions. Hardware dependencies, such as biometric scanners and on-premises security appliances, have experienced fluctuating import costs, compelling vendors to reevaluate sourcing strategies and localize manufacturing where feasible. As a result, organizations reliant on high-performance hardware for on-device authentication have encountered temporary lead time extensions and budgetary pressures that demand careful procurement planning.Beyond hardware, software licensing models have also felt the ripple effects of increased cross-border trade levies. Vendors that rely on international development teams and offshore support centers have been prompted to reassess service delivery structures, sometimes passing incremental costs onto end users. At the same time, the tariffs have catalyzed a renewed focus on cloud-native, subscription-based offerings that minimize reliance on physical infrastructure. This trend aligns with a broader migration toward software-as-a-service deployments, where the vendor shoulders infrastructure overhead and can absorb tariff-induced cost shifts more effectively.
Moreover, these trade policy adjustments have accelerated strategic consolidation within the industry. Smaller regional players facing margin compression have sought partnerships or acquisition by larger firms with diversified geographic footprints and broader capital reserves. Collectively, the 2025 tariff regime has underscored the importance of supply chain resilience and cost-optimization, urging both vendors and adopters to develop contingency plans that mitigate geopolitical uncertainties.
Uncovering how component, deployment mode, organizational size, authentication modalities, and vertical demands shape solution differentiation in account takeover software
The account takeover software market reveals a complex tapestry of component, deployment, organizational, authentication, and vertical considerations, each influencing solution design and buyer preferences. On the component front, software modules for anomaly detection and risk scoring coexist alongside services that encompass managed surveillance and professional consultation. Within services, implementation engagements ensure seamless integration with existing identity and access management ecosystems, while ongoing integration tasks maintain synchronization as enterprises evolve. Training offerings round out professional services by empowering security teams with the expertise needed to interpret alerts and refine policies.Transitioning to deployment modes, public cloud solutions deliver rapid provisioning and elastic scalability, private cloud options furnish heightened control and data sovereignty, and hybrid cloud approaches blend these advantages to meet stringent compliance needs. Enterprises often navigate between these models based on workload sensitivity, regulatory obligations, and internal IT capabilities. The freedom to pivot across deployment configurations has become a hallmark of leading solutions, allowing organizations to optimize cost structures without compromising protection.
Organization size plays a pivotal role in shaping requirements, with large enterprises demanding comprehensive policy orchestration, centralized dashboards, and global incident response support, whereas small to medium businesses prioritize ease of use, rapid time to value, and bundled functionality. Furthermore, authentication modalities reflect a spectrum of risk tolerances and user experience considerations. Biometric mechanisms employ facial, fingerprint, and iris recognition to validate identity with minimal friction, while multi-factor authentication introduces layered safeguards such as one-time passwords delivered via email or SMS, push notifications, and token-based credentials. Hardware tokens and software tokens similarly offer discrete advantages, balancing portability against integration effort. Traditional password strategies remain ubiquitous for their familiarity, yet they increasingly serve as one element within a broader, adaptive framework.
Finally, industry verticals such as banking, financial services, and insurance demand rigorous audit trails and regulatory alignment, e-commerce platforms seek seamless customer journeys that deter fraud without impeding conversions, government agencies impose stringent access controls for classified data, and healthcare entities focus on safeguarding electronic health records while maintaining clinician workflow efficiency. These vertical-specific drivers shape feature roadmaps, partnership models, and compliance roadmaps, ultimately defining the competitive landscape.
Exploring how distinct regulatory demands, threat landscapes, and technological infrastructures drive adoption variations across the Americas, EMEA, and Asia-Pacific
Regionally, market dynamics diverge as enterprises react to unique regulatory regimes, threat environments, and technology infrastructures. In the Americas, the emphasis on consumer data protection laws and heightened fraud monitoring has driven widespread adoption of multi-factor authentication and managed service offerings. Organizations in this region benefit from robust cloud ecosystems that support rapid innovation, yet they also contend with sophisticated adversaries that exploit social engineering and credential resale marketplaces.Across Europe, the Middle East & Africa, regulatory frameworks such as data privacy statutes and cross-border data transfer rules have compelled solution providers to enhance data residency controls and transparency features. Localized threat intelligence feeds and regional integration partnerships further bolster defense mechanisms, while the push for digital inclusion has prompted scalable, user-friendly authentication alternatives that accommodate diverse user populations. In contrast, Asia-Pacific markets exhibit a strong appetite for mobile-first account protection strategies, driven by high smartphone penetration and burgeoning digital economies. Here, biometric authentication has gained rapid traction, underpinned by consumer familiarity with facial and fingerprint recognition in financial and e-commerce applications.
These regional distinctions underscore the necessity for vendors to tailor offerings to local market nuances, forging alliances with regional integrators, and aligning roadmaps with evolving data sovereignty policies. As a result, enterprises benefit from more contextualized threat intelligence and culturally attuned user journeys, bolstering adoption and resilience across diverse global footprints.
Examining how innovation leadership, strategic alliances, and service models define the competitive edge among top account takeover solution providers
Leading providers in the account takeover space distinguish themselves through a combination of technological innovation, strategic partnerships, and service excellence. Some have emerged as pioneers in behavioral biometric engines that analyze keystroke patterns and mouse movements to detect anomalies with remarkable accuracy. Others focus on integrating threat intelligence from dark web monitoring and real-time fraud signal exchanges to elevate their detection capabilities. Meanwhile, partnerships between software vendors and managed security service firms have given birth to unified solutions that streamline both proactive threat hunting and reactive incident response workflows.Beyond core technology, a subset of companies has carved out a niche by offering vertical-focused templates that accelerate compliance alignment for sectors such as banking and healthcare. These preconfigured frameworks drastically reduce deployment time and ensure adherence to industry-specific regulations. In parallel, a wave of consolidation has seen large incumbents acquire specialized startups, broadening their product portfolios to include advanced bot management, biometric authentication, and identity orchestration platforms. This consolidation trend reflects the growing buyer preference for single-vendor ecosystems that simplify procurement and vendor management.
Service delivery models also vary, with some market leaders emphasizing self-service portals and API-driven integrations aimed at DevOps teams, while others maintain dedicated client success units that provide hands-on support, custom policy tuning, and ongoing threat modeling. As a result, enterprises can select vendors that align with their internal capabilities and strategic security objectives, whether they prioritize rapid deployment or deep collaborative engagement.
Implementing strategic imperatives that blend adaptive technology, managed services, and cross-functional governance to elevate account takeover resilience
To fortify defenses against account compromise, industry leaders should adopt a multi-pronged strategy that balances cutting-edge technology with process optimization and stakeholder alignment. First, integrating adaptive authentication engines that leverage continuous risk assessment can significantly reduce false positives while maintaining frictionless user experiences. By correlating device telemetry, behavioral signals, and threat intelligence feeds, organizations can dynamically calibrate challenge requirements and focus resources on high-risk events.Second, embedding managed detection and response capabilities within the broader identity security program enhances threat visibility and accelerates incident resolution. Outsourcing 24/7 monitoring to specialized teams allows internal staff to concentrate on strategic initiatives, such as refining access policies and conducting red team exercises. This hybrid operating model fosters resilience by combining vendor expertise with in-house governance frameworks.
Third, organizations must establish cross-functional incident response playbooks that align IT, security operations, legal, and customer service teams. Well-defined protocols for communication, evidence preservation, and remediation expedite recovery and minimize reputational damage. Regular tabletop exercises and post-incident reviews help identify gaps in technology configurations and escalation channels, leading to continuous improvement.
Lastly, cultivating executive sponsorship and budgetary commitment for identity-focused initiatives is crucial. Presenting data-driven business cases that quantify risk reduction, compliance alignment, and customer trust gains ensures sustained investment. By positioning account takeover prevention as a strategic differentiator rather than a compliance checkbox, security leaders can secure the necessary resources to deploy advanced solutions and maintain a proactive security posture.
Detailing the structured research approach that integrates primary interviews, secondary analysis, and rigorous validation to ensure insights accuracy
This research employs a rigorous methodology combining primary and secondary sources, ensuring a comprehensive view of the account takeover software market. Primary insights were obtained through interviews with cybersecurity decision-makers, solution architects, and threat intelligence analysts across various industries. These conversations provided firsthand perspectives on pain points, deployment challenges, and desired feature enhancements. Complementing this qualitative data, vendor briefings, investor presentations, and technical white papers offered an in-depth understanding of technology roadmaps and strategic priorities.Secondary research encompassed analysis of relevant industry reports, regulatory publications, and academic studies focusing on identity management and fraud prevention. Publicly available financial disclosures and patent filings were reviewed to validate market positioning and innovation trajectories of key providers. Additionally, data from open-source intelligence platforms and dark web monitoring tools enriched the threat landscape overview, highlighting emerging attack patterns and actor motivations.
Analytical frameworks such as SWOT assessments, competitive benchmarking, and vendor capability matrices were applied to distill critical differentiators and identify market gaps. All findings underwent validation through cross-referencing with subject matter experts and triangulation across multiple data points. This structured approach ensures that the insights and recommendations presented reflect current industry realities and anticipate near-term developments.
Synthesizing essential market findings to emphasize the necessity of adaptive, intelligence-driven account takeover defenses for enterprise resilience
The aggregate insights presented in this summary underscore the escalating imperative for robust account takeover prevention strategies. Technological advancements in artificial intelligence and biometric verification are redefining the capabilities of modern solutions, while evolving threat vectors demand continuous innovation and strategic agility. Regional nuances, tariff dynamics, and segmentation complexities further highlight the necessity for tailored deployments and resilient supply chain planning.Strategic partnerships and consolidation trends are reshaping competitive dynamics, increasing the appeal of unified platforms that combine detection, response, and identity governance. Meanwhile, actionable recommendations emphasize the importance of adaptive authentication, managed detection services, and cross-functional governance to strengthen security postures. Executives tasked with safeguarding digital identities must prioritize sustainable investment and executive sponsorship to maintain momentum amid an increasingly hostile threat environment.
In conclusion, mastering account takeover defense requires a holistic approach that integrates advanced technologies, service excellence, and operational rigor. By internalizing the insights detailed herein, security leaders can make informed decisions that protect user credentials, enhance trust, and drive organizational resilience. The imperative is clear: proactive, intelligence-driven strategies are no longer optional but foundational to enduring digital security.
Market Segmentation & Coverage
This research report forecasts revenues and analyzes trends in each of the following sub-segmentations:- Component
- Services
- Managed Services
- Professional Services
- Software
- Services
- Deployment Mode
- Cloud
- Private Cloud
- Public Cloud
- On Premises
- Cloud
- Authentication Type
- Knowledge-Based Authentication (KBA)
- Multi Factor Authentication
- Passwordless Authentication
- Biometrics
- FIDO2/WebAuthn
- Two-Factor Authentication (2FA)
- Organization Size
- Large Enterprises
- Small & Medium Enterprises
- Industry Vertical
- Banking Financial Services And Insurance
- Government
- Healthcare
- IT & Telecom
- Retail & eCommerce
- Americas
- North America
- United States
- Canada
- Mexico
- Latin America
- Brazil
- Argentina
- Chile
- Colombia
- Peru
- North America
- Europe, Middle East & Africa
- Europe
- United Kingdom
- Germany
- France
- Russia
- Italy
- Spain
- Netherlands
- Sweden
- Poland
- Switzerland
- Middle East
- United Arab Emirates
- Saudi Arabia
- Qatar
- Turkey
- Israel
- Africa
- South Africa
- Nigeria
- Egypt
- Kenya
- Europe
- Asia-Pacific
- China
- India
- Japan
- Australia
- South Korea
- Indonesia
- Thailand
- Malaysia
- Singapore
- Taiwan
- Agari Data, Inc.
- Akamai Technologies, Inc.
- Barracuda Networks, Inc.
- Beyond Identity, Inc.
- Cloudflare, Inc.
- CrossClassify, Inc.
- DataDome SAS
- Equifax Inc.
- F5, Inc.
- Forter, Inc.
- GreatHorn, Inc.
- Human Security, Inc.
- Imperva, Inc.
- International Business Machines Corporation.
- Memcyco Ltd.
- Netacea Limited
- Okta, Inc.
- Proofpoint, Inc.
- Radware Ltd.
- Riskified Ltd.
- Sift Science, Inc.
- Signifyd, Inc.
- Sum and Substance Ltd.
- Telesign Corporation
- ZeroFox, Inc.
Table of Contents
3. Executive Summary
4. Market Overview
7. Cumulative Impact of Artificial Intelligence 2025
Companies Mentioned
The companies profiled in this Account Takeover Software market report include:- Agari Data, Inc.
- Akamai Technologies, Inc.
- Barracuda Networks, Inc.
- Beyond Identity, Inc.
- Cloudflare, Inc.
- CrossClassify, Inc.
- DataDome SAS
- Equifax Inc.
- F5, Inc.
- Forter, Inc.
- GreatHorn, Inc.
- Human Security, Inc.
- Imperva, Inc.
- International Business Machines Corporation.
- Memcyco Ltd.
- Netacea Limited
- Okta, Inc.
- Proofpoint, Inc.
- Radware Ltd.
- Riskified Ltd.
- Sift Science, Inc.
- Signifyd, Inc.
- Sum and Substance Ltd.
- Telesign Corporation
- ZeroFox, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 199 |
| Published | November 2025 |
| Forecast Period | 2025 - 2032 |
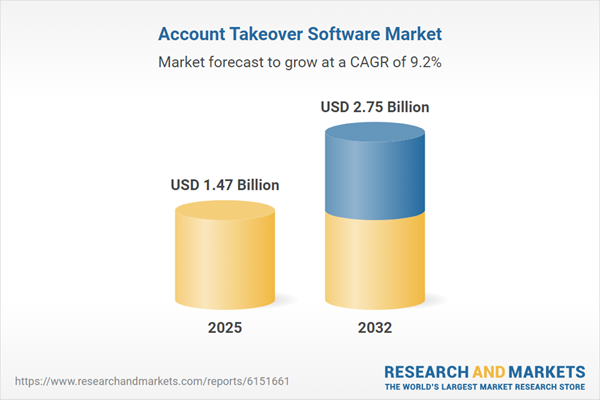
| Estimated Market Value ( USD | $ 1.47 Billion |
| Forecasted Market Value ( USD | $ 2.75 Billion |
| Compound Annual Growth Rate | 9.2% |
| Regions Covered | Global |
| No. of Companies Mentioned | 26 |