Speak directly to the analyst to clarify any post sales queries you may have.
Pioneering a Multi-Layered Security Architecture to Safeguard Critical Infrastructure and Digital Assets Across Converging Threat Vectors
In an era where cyber threats and physical vulnerabilities intertwine, multi-layered security systems have emerged as a strategic imperative for organizations seeking to protect their assets, data, and reputation. This introduction provides a panoramic view of how converging threat vectors-ranging from sophisticated malware campaigns to targeted physical intrusions-are compelling enterprises and public institutions to adopt integrated defense architectures. By combining perimeter controls, identity management, application safeguards, and data protection measures, stakeholders are crafting resilient environments that can detect, deter, and respond to rapidly evolving risks.Furthermore, the modern security landscape demands a holistic approach that bridges legacy investments with emerging technologies. Organizations are no longer content with point solutions; instead, they are orchestrating cross-functional strategies that align network, endpoint, identity, application, cloud, data, and physical security into cohesive, adaptive frameworks. This report lays the groundwork for understanding how these layers interoperate to deliver greater visibility, enforcement consistency, and operational efficiency across hybrid infrastructures. Ultimately, this introduction sets the stage for an in-depth exploration of shifting market drivers, regulatory influences, segmentation nuances, and regional dynamics that define the multi-layered security systems domain.
Navigating the Emerging Paradigm Shifts in Security Posture Driven by Cloud Migration, Zero Trust Adoption, and Advanced Persistent Threat Evolutions
The security landscape is undergoing transformative shifts driven by the proliferation of cloud services, the widespread adoption of zero trust principles, and the escalating complexity of advanced persistent threats. Traditional network perimeters are dissolving as remote workforces connect through public and private clouds, necessitating adaptive architectures capable of enforcing policies across dispersed endpoints. At the same time, threat actors are increasingly exploiting lateral movement opportunities, prompting cybersecurity leaders to reevaluate legacy firewalls in favor of dynamic micro-segmentation and continuous authentication mechanisms.Moreover, the integration of artificial intelligence and machine learning into threat detection platforms is ushering in a new paradigm of proactive defense. Behavioral analytics engines now enable real-time anomaly detection that can isolate suspicious activities before they escalate into full-blown incidents. Concurrently, regulatory frameworks around data privacy and critical infrastructure protection are becoming more stringent, compelling organizations to harmonize compliance obligations with strategic security investments. As these transformative currents converge, stakeholders must navigate a rapidly evolving matrix of technological innovations, threat actor methodologies, and governance imperatives to maintain resilience and foster stakeholder confidence.
Assessing the Far-Reaching Consequences of the 2025 United States Tariff Measures on Multi-Layered Security Component Supply Chains and Procurement Costs
The introduction of new tariff measures by the United States in 2025 has reverberated across the multi-layered security systems supply chain, affecting the procurement and deployment of both hardware and software components. Leading network security appliances, encryption modules, and specialized semiconductors are now subject to revised duties, which have, in turn, influenced sourcing strategies and vendor negotiations. As a result, some enterprises have accelerated their shift toward regional suppliers or alternative manufacturers to mitigate cost pressures and potential logistics delays.Consequently, the revised trade environment has prompted a reevaluation of total cost of ownership calculations, with procurement teams factoring in lead-time variability and potential duty reclassifications. In addition, service providers are adapting by revising support contracts, adjusting maintenance fees, and bundling complementary services to preserve margin structures. The dynamic regulatory context has also catalyzed closer collaboration between security architects and procurement specialists, ensuring that system designs remain robust without compromising budgetary constraints. Therefore, understanding these tariff-induced ripples is essential for decision-makers aiming to align operational resilience with prudent financial stewardship.
Unveiling Deep Dive Insights into Network, Endpoint, Identity, Application, Data, Cloud, and Physical Security Segments Shaping the Market Dynamics
Analyzing the market through defined security segments reveals a nuanced interplay of capabilities and investment priorities. Within network security, the study spans next-generation firewalls and unified threat management solutions, complemented by host-based and network-based intrusion detection and prevention systems alongside virtual private networks. This layer underscores the importance of deep packet inspection and integrated threat intelligence to fortify perimeter defenses. Transitioning to endpoint security, the focus shifts to antivirus suites, which now leverage artificial intelligence, behavioral heuristics, and signature analysis, as well as advanced endpoint detection and response platforms that deliver comprehensive threat hunting and remediation workflows.In the realm of identity and access management, multi-factor authentication has diversified into app-based, biometric, and SMS-OTP modalities, working in concert with privileged access management and single sign-on services to streamline user journeys while maintaining rigorous governance. On the application security front, organizations are deploying API security tools, runtime application self-protection mechanisms, and web application firewalls to shield mission-critical services from zero-day exploits and injection attacks. Simultaneously, data security strategies emphasize data loss prevention frameworks and robust encryption practices, employing both asymmetric and symmetric cryptographic techniques to safeguard information at rest, in transit, and in use.
Extending defenses to cloud environments, cloud access security brokers, cloud workload protection platforms, and container security solutions have become indispensable for managing dynamic workloads across public, private, and hybrid clouds. Finally, physical security measures integrate biometric and card-based access control systems-leveraging facial, fingerprint, and iris recognition technologies-with both analog and IP video surveillance architectures to deliver end-to-end asset protection. By examining each segment holistically, stakeholders can pinpoint areas for consolidation, enhancement, or strategic divestment in pursuit of an optimized security posture.
Highlighting Regional Nuances and Growth Drivers Across the Americas, Europe Middle East Africa, and Asia Pacific Security Ecosystems Under Emerging Threat Landscapes
Examining regional trends reveals distinct drivers and adoption patterns across the Americas, Europe Middle East and Africa, and Asia Pacific markets. In the Americas, enterprises are capitalizing on robust regulatory enforcement and mature vendor ecosystems to integrate advanced analytics and zero trust frameworks into large-scale deployments. This region's emphasis on threat intelligence sharing and public-private partnerships has cultivated a collaborative environment that accelerates innovation and incident response coordination.Transitioning to Europe, the Middle East and Africa, organizations navigate a diverse mosaic of regulatory landscapes, from stringent data protection protocols in the European Union to rapidly developing cybersecurity infrastructures in the GCC and African markets. Consequently, localized compliance demands and infrastructure modernization efforts are driving heightened investments in identity management and cloud security, as stakeholders seek to harmonize cross-border operations with emerging governance frameworks.
In Asia Pacific, expansive digital transformation initiatives and a burgeoning startup ecosystem are fueling demand for agile, cost-effective security solutions. Enterprises across this region are prioritizing scalable cloud workload protection, container security, and intelligent video surveillance deployments to support smart city projects, e-commerce platforms, and industrial automation. As each region converges on multi-layered architectures, understanding these nuanced drivers is critical for vendors and end-users alike to tailor strategies and unlock growth opportunities.
Examining the Strategic Positioning and Innovation Leadership of Prominent Vendors Shaping the Future of Multi Layered Security Solutions
The competitive landscape is characterized by a blend of established cybersecurity powerhouses and innovative challengers, each vying to define the next frontier of multi-layered security. Leading network security specialists have expanded portfolios through strategic acquisitions and organic R&D, integrating cloud native capabilities and orchestration interfaces to enhance interoperability. Simultaneously, endpoint protection vendors are embedding threat intelligence platforms and automated response playbooks to accelerate detection and remediation cycles.Within identity access management, multi-factor authentication pioneers are collaborating with biometric hardware manufacturers to refine user experience and reinforce continuous authentication models. Application security incumbents have bolstered their offerings by embedding real-time code analysis and behavioral runtime protection into development lifecycles. Meanwhile, data security leaders are advancing homomorphic encryption and tokenization technologies to extend cryptographic safeguards into analytics and collaboration platforms.
Cloud security innovators are converging container security with service mesh instrumentation to deliver unified visibility across dynamic environments, whereas physical security integrators are weaving video analytics, AI-driven anomaly detection, and access control into holistic building management systems. Collectively, these key players are shaping the market through differentiated architectures, value-added ecosystems, and a relentless focus on streamlined orchestration and automation.
Formulating Actionable Strategic Recommendations to Drive Resilience and Competitive Advantage Amid Intensifying Cybersecurity Threats and Regulatory Complexities
To fortify defenses and maintain competitive advantage, industry leaders should embrace a set of strategic imperatives. First, adopting a zero trust architecture that verifies every transaction and user interaction can mitigate lateral threat propagation and reduce the risk of privilege escalation. Additionally, integrating artificial intelligence-driven analytics and machine learning models will enable proactive threat hunting and near-real-time anomaly detection, thus closing critical time gaps between detection and response.Moreover, organizations must prioritize supply chain resilience by diversifying supplier relationships and implementing rigorous vendor risk assessments to hedge against tariff fluctuations and component shortages. Strengthening cross-functional collaboration between security operations, IT procurement, and compliance teams will ensure that governance frameworks align with operational realities. Investing in workforce development, through continuous training and simulated attack exercises, will cultivate the human capital required to navigate evolving threat scenarios effectively.
Finally, forging strategic partnerships with managed service providers and threat intelligence consortia can extend organizational capabilities without significant capital outlay. By operationalizing these recommendations, decision-makers can construct adaptive, cost-efficient, and outcome-oriented multi-layered security ecosystems that are resilient to both current and emerging challenges.
Detailing Rigorous Research Methodology Integrating Primary Interviews, Secondary Literature Review, and Triangulation to Ensure Comprehensive Market Intelligence
The research methodology underpinning this study integrates both primary and secondary approaches to deliver comprehensive market insights. Initially, in-depth interviews were conducted with security executives, technology architects, and procurement leaders to capture firsthand perspectives on adoption drivers, deployment challenges, and emerging priorities. These qualitative inputs were complemented by a rigorous review of whitepapers, regulatory filings, vendor documentation, and peer-reviewed publications to validate and contextualize industry narratives.Subsequently, data triangulation techniques were applied to reconcile insights across multiple sources, ensuring consistency and accuracy in segment definitions, technology categorizations, and regional analyses. Quantitative data was then synthesized through scenario mapping and sensitivity analysis to test the robustness of key findings under varying regulatory and economic conditions. Throughout the process, quality controls-such as peer reviews, editorial audits, and adherence to research ethics standards-were enforced to minimize bias and uphold methodological rigor.
Ultimately, this blended research approach provides decision-makers with an authoritative, transparent, and reproducible foundation for strategic planning, vendor selection, and risk management in the multi-layered security domain.
Synthesizing Key Findings to Reinforce the Imperative for Holistic and Adaptive Multi Layered Security Architectures in a Rapidly Evolving Threat Environment
In conclusion, the escalating complexity of cyber threats, coupled with evolving regulatory landscapes and supply chain headwinds, underscores the imperative for holistic, multi-layered security architectures. Stakeholders must harmonize network controls, endpoint defenses, identity governance, application hardening, data protection, cloud security, and physical safeguards within a unified framework that leverages automation and real-time intelligence.As innovation accelerates and adversaries refine their tactics, resilient organizations will be those that continuously adapt their defenses, foster cross-disciplinary collaboration, and maintain strategic visibility across all environmental layers. By synthesizing the insights presented herein, security leaders can chart a clear path toward operational agility, risk mitigation, and enhanced stakeholder confidence in an increasingly unpredictable threat landscape.
Market Segmentation & Coverage
This research report forecasts the revenues and analyzes trends in each of the following sub-segmentations:- Network Security
- Firewall
- Next-Generation Firewall
- Unified Threat Management
- Intrusion Detection And Prevention
- Host-Based Intrusion Detection And Prevention
- Network-Based Intrusion Detection And Prevention
- Virtual Private Network
- Firewall
- Endpoint Security
- Antivirus
- AI-Based Antivirus
- Behavior-Based Antivirus
- Signature-Based Antivirus
- Endpoint Detection And Response
- Antivirus
- Identity Access Management
- Multi-Factor Authentication
- App-Based Authentication
- Biometric Authentication
- SMS OTP
- Privileged Access Management
- Single Sign-On
- Multi-Factor Authentication
- Application Security
- API Security
- Runtime Application Self-Protection
- Web Application Firewall
- Data Security
- Data Loss Prevention
- Encryption
- Asymmetric Encryption
- Symmetric Encryption
- Cloud Security
- Cloud Access Security Broker
- Cloud Workload Protection Platform
- Container Security
- Physical Security
- Access Control
- Biometric Access Control
- Facial Recognition
- Fingerprint Recognition
- Iris Recognition
- Card-Based Access Control
- Biometric Access Control
- Video Surveillance
- Analog Cameras
- IP Cameras
- Access Control
- Americas
- North America
- United States
- Canada
- Mexico
- Latin America
- Brazil
- Argentina
- Chile
- Colombia
- Peru
- North America
- Europe, Middle East & Africa
- Europe
- United Kingdom
- Germany
- France
- Russia
- Italy
- Spain
- Netherlands
- Sweden
- Poland
- Switzerland
- Middle East
- United Arab Emirates
- Saudi Arabia
- Qatar
- Turkey
- Israel
- Africa
- South Africa
- Nigeria
- Egypt
- Kenya
- Europe
- Asia-Pacific
- China
- India
- Japan
- Australia
- South Korea
- Indonesia
- Thailand
- Malaysia
- Singapore
- Taiwan
- Cisco Systems, Inc.
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- Check Point Software Technologies Ltd.
- International Business Machines Corporation
- VMware, Inc.
- CrowdStrike Holdings, Inc.
- Trend Micro Incorporated
- Sophos Group plc
- McAfee Corp.
Table of Contents
Companies Mentioned
The companies profiled in this Multi-Layered Security Systems Market report include:- Cisco Systems, Inc.
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- Check Point Software Technologies Ltd.
- International Business Machines Corporation
- VMware, Inc.
- CrowdStrike Holdings, Inc.
- Trend Micro Incorporated
- Sophos Group plc
- McAfee Corp.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 181 |
| Published | November 2025 |
| Forecast Period | 2025 - 2032 |
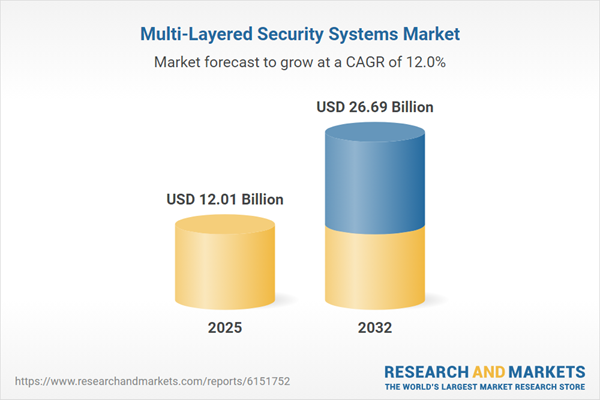
| Estimated Market Value ( USD | $ 12.01 Billion |
| Forecasted Market Value ( USD | $ 26.69 Billion |
| Compound Annual Growth Rate | 11.9% |
| Regions Covered | Global |
| No. of Companies Mentioned | 11 |