Speak directly to the analyst to clarify any post sales queries you may have.
10% Free customizationThis report comes with 10% free customization, enabling you to add data that meets your specific business needs.
The rise of digital banking, e-commerce, and online service platforms has intensified the need for robust yet non-intrusive authentication mechanisms. With cybercrime and account takeover incidents on the rise, organizations are investing in technologies that balance security and convenience. Passive authentication allows for continuous monitoring of user behavior, offering dynamic risk assessment and real-time alerts without burdening the user. Moreover, increasing regulatory compliance requirements in sectors like finance and healthcare are driving the adoption of advanced authentication solutions to prevent fraud and protect sensitive information. The integration of AI and machine learning further strengthens the market by improving accuracy, reducing false positives, and adapting to evolving attack patterns.
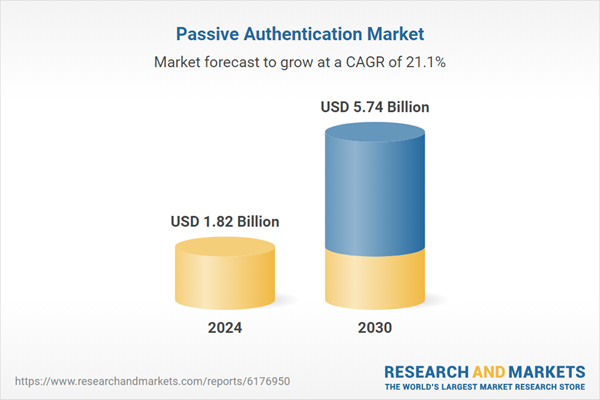
The market for passive authentication is expected to grow as digital transformation accelerates worldwide. Mobile-first ecosystems, cloud computing, and the Internet of Things (IoT) increase the complexity of authentication needs, encouraging enterprises to adopt adaptive and intelligent security systems. Companies are also recognizing that user experience is a critical differentiator, and seamless authentication can enhance customer satisfaction and retention. Vendors offering scalable, AI-driven passive authentication solutions are witnessing heightened demand across industries such as banking, retail, healthcare, and government. As organizations prioritize both cybersecurity and user convenience, the global passive authentication market is poised for significant expansion in the coming years.
Key Market Drivers
Rising Cybersecurity Threats
The increase in cybercrime, data breaches, and identity theft has become a critical concern for organizations globally. Traditional authentication methods such as passwords and one-time passcodes are no longer sufficient to protect sensitive information. Passive authentication, which continuously monitors user behavior and device patterns in real-time, offers a more secure approach. By identifying suspicious activities such as abnormal login locations, unusual device usage, or behavioral deviations, passive authentication allows organizations to proactively prevent unauthorized access. This approach minimizes risk while maintaining a seamless user experience.As businesses digitize operations and expand online services, the volume and sophistication of cyberattacks continue to grow. Organizations are increasingly adopting passive authentication systems to ensure continuous protection without disrupting user workflows. The ability to detect threats instantaneously reduces potential financial and reputational damage from security incidents. By embedding security within the user experience, organizations can address both risk mitigation and user convenience simultaneously. Organizations implementing continuous authentication methods have observed a 35% reduction in unauthorized account access incidents within the first year. By continuously monitoring behavioral and device patterns, these systems can identify suspicious activity in real-time, preventing breaches that would otherwise compromise sensitive data, financial assets, and customer trust.
Key Market Challenges
Integration Complexity Across Legacy Systems
One of the foremost challenges for the global passive authentication market is the complexity of integrating these advanced systems into existing legacy infrastructure. Many organizations, particularly in banking, healthcare, and government sectors, operate with legacy applications and hardware that were not designed to support continuous authentication methods. Implementing passive authentication in such environments requires significant customization, which can increase both time and cost. Furthermore, ensuring compatibility with older databases, software protocols, and user management systems often necessitates extensive testing and phased rollouts, creating operational delays. The technical expertise required for seamless integration is not uniformly available, particularly in small to medium enterprises, thereby limiting adoption in certain segments.Beyond technical integration, organizations must also align passive authentication solutions with existing business processes and workflows. Any misalignment can result in operational bottlenecks, user dissatisfaction, or increased error rates. Employees and end users must be educated on new security protocols without disrupting their daily activities.
Additionally, IT teams face the challenge of maintaining continuous updates and patches to ensure security effectiveness while avoiding interruptions to ongoing services. These integration complexities can discourage investment in passive authentication systems, especially for organizations that prioritize operational continuity over security enhancements. Addressing this challenge requires solution providers to offer flexible, scalable platforms and comprehensive implementation support.
Key Market Trends
Adoption of Behavioral Biometrics
The adoption of behavioral biometrics is becoming a key trend in the global passive authentication market. Unlike traditional authentication methods that rely on static credentials such as passwords or tokens, behavioral biometrics analyzes unique user behaviors including typing rhythm, mouse movements, navigation patterns, and touchscreen gestures. This approach allows organizations to continuously verify user identity in real-time without disrupting the user experience. By integrating behavioral biometrics, companies can enhance security measures while maintaining frictionless access for end users. The ability to detect subtle deviations in user behavior makes this technology particularly effective in preventing account takeover and identity fraud.Organizations across financial services, healthcare, and e-commerce sectors are increasingly leveraging behavioral biometrics as a primary layer of passive authentication. This trend is driven by the dual need to improve security and deliver seamless digital experiences. Behavioral biometrics platforms are also becoming more cost-effective and scalable, allowing even mid-sized enterprises to adopt advanced security measures without overhauling existing infrastructure. As the sophistication of cyber threats increases, the reliance on behavioral analytics as a continuous and adaptive security mechanism is expected to grow significantly.
Key Market Players
- Thales S.A.
- IBM Corporation
- Cisco Systems, Inc.
- NEC Corporation
- OneSpan, Inc.
- Gemalto N.V.
- Entrust Corporation
- Microsoft Corporation
- Okta, Inc.
- Ping Identity Corporation
Report Scope:
In this report, the Global Passive Authentication Market has been segmented into the following categories, in addition to the industry trends which have also been detailed below:Passive Authentication Market, By Component:
- Solution
- Services
Passive Authentication Market, By Deployment:
- Cloud
- On-Premises
Passive Authentication Market, By Function:
- Compliance Management
- Marketing Management
- Risk Management
- Others
Passive Authentication Market, By Vertical:
- BFSI
- Government
- IT & Telecom
- Retail & Consumer Goods
- Healthcare
- Media & Entertainment
- Others
Passive Authentication Market, By Region:
- North America
- United States
- Canada
- Mexico
- Europe
- Germany
- France
- United Kingdom
- Italy
- Spain
- Asia Pacific
- China
- India
- Japan
- South Korea
- Australia
- Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- South America
- Brazil
- Colombia
- Argentina
Competitive Landscape
Company Profiles: Detailed analysis of the major companies present in the Global Passive Authentication Market.Available Customizations:
With the given market data, the publisher offers customizations according to a company's specific needs. The following customization options are available for the report.Company Information
- Detailed analysis and profiling of additional market players (up to five).
This product will be delivered within 1-3 business days.
Table of Contents
Companies Mentioned
- Thales S.A.
- IBM Corporation
- Cisco Systems, Inc.
- NEC Corporation
- OneSpan, Inc.
- Gemalto N.V.
- Entrust Corporation
- Microsoft Corporation
- Okta, Inc.
- Ping Identity Corporation
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 185 |
| Published | September 2025 |
| Forecast Period | 2024 - 2030 |
| Estimated Market Value ( USD | $ 1.82 Billion |
| Forecasted Market Value ( USD | $ 5.74 Billion |
| Compound Annual Growth Rate | 21.1% |
| Regions Covered | Global |
| No. of Companies Mentioned | 10 |