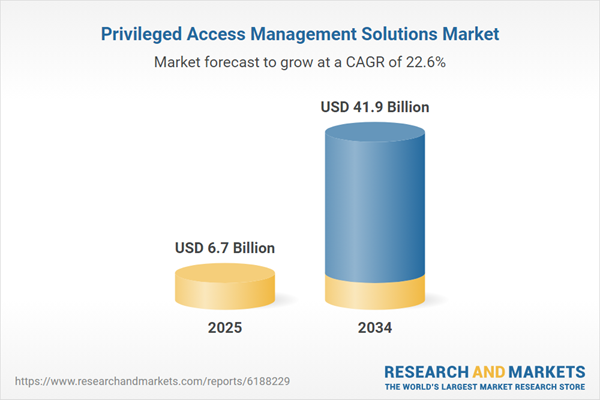
Privileged Access Management (PAM) solutions are designed to secure, control, and monitor access to critical systems, data, and applications within an organization. With the rise of cybersecurity threats and the increasing complexity of IT infrastructures, the need for robust access control systems has become a priority for enterprises. PAM solutions help mitigate risks associated with the misuse of privileged credentials by providing centralized access management, enforcing strong authentication mechanisms, and ensuring that only authorized users can access sensitive information. These solutions are essential for organizations that must comply with regulatory requirements, such as GDPR, HIPAA, and PCI-DSS, as they ensure the protection of critical assets and prevent unauthorized access. The global market for PAM solutions is growing rapidly due to increasing cyber threats, data breaches, and the adoption of cloud computing and digital transformation strategies by organizations worldwide. As businesses continue to prioritize security, PAM solutions offer organizations the ability to proactively monitor, audit, and control privileged access, thereby reducing the potential for insider threats and ensuring a more secure and compliant IT environment.
The privileged access management solutions market is expected to continue expanding, driven by the increasing sophistication of cyber threats and the rise of remote work. The shift to cloud-based environments, combined with the growing adoption of DevOps and containerization, requires enterprises to adopt advanced PAM solutions to secure privileged access across hybrid and multi-cloud infrastructures. PAM vendors are responding to this demand by integrating their solutions with advanced technologies such as artificial intelligence (AI), machine learning (ML), and behavioral analytics to provide more efficient risk detection, automated response capabilities, and improved access controls. Additionally, organizations will focus on automating their access management processes to reduce the burden on IT teams while enhancing security. Key developments in 2024 will include the integration of PAM solutions with identity and access management (IAM) systems, providing a unified platform for managing both privileged and regular user access. As the need for stronger security measures becomes more critical, the demand for comprehensive PAM solutions that cater to both on-premise and cloud environments will increase, offering businesses the flexibility to manage and monitor access across diverse infrastructures.
The privileged access management solutions market will continue to evolve, with organizations focusing on zero-trust security models, where trust is never assumed, and every request for access is verified. The implementation of zero-trust principles will drive the development of more sophisticated PAM solutions that leverage AI and ML algorithms to continuously evaluate access permissions and detect anomalous behavior in real-time. As businesses transition to fully digital operations, the need for PAM solutions that can secure an increasingly distributed workforce and manage access to a wide range of cloud-based applications will become even more critical. Vendors will focus on providing scalable PAM solutions that can meet the security needs of large enterprises and small businesses alike, offering flexibility in deployment and operation. the integration of PAM solutions with emerging technologies such as blockchain for secure credential management and automated compliance reporting will open new opportunities in the market. With an increasing focus on security and compliance, PAM will become an essential component of an organization's broader cybersecurity strategy, playing a vital role in securing privileged access in the digital age.
Key Insights: Privileged Access Management Solutions Market
- Zero-Trust Security Models: The adoption of zero-trust frameworks will continue to drive demand for PAM solutions, as organizations implement stricter access controls and continuously verify user identities.
- Cloud Security Integration: PAM solutions will increasingly be integrated with cloud platforms, enabling businesses to secure privileged access to cloud-based applications and resources.
- Behavioral Analytics and AI Integration: Advanced AI and ML algorithms will be incorporated into PAM solutions for real-time threat detection and automated risk response.
- Automated Access Management: Organizations will increasingly prioritize the automation of access management processes to reduce manual intervention and improve overall security.
- Compliance and Regulatory Requirements: Growing compliance requirements in industries like finance and healthcare will drive the adoption of PAM solutions to ensure regulatory adherence and secure privileged access.
- Increasing Cybersecurity Threats: The growing sophistication of cyberattacks, particularly those targeting privileged credentials, drives the demand for PAM solutions.
- Shift to Cloud and Hybrid Environments: The transition to cloud-based and hybrid IT infrastructures increases the need for effective management and security of privileged access across diverse environments.
- Regulatory Compliance: Stricter data protection regulations and industry standards (e.g., GDPR, HIPAA) are pushing organizations to adopt PAM solutions to safeguard sensitive data.
- Remote Work and Distributed Workforce: The rise of remote work requires organizations to secure privileged access across multiple locations, increasing the need for robust PAM solutions.
- Complexity of Implementation: Deploying PAM solutions can be complex, particularly in organizations with existing legacy systems and diverse IT environments, posing challenges for seamless integration.
Privileged Access Management Solutions Market Segmentation
By Offerings
- Solution
- Service
- Other Offerings
By Deployment
- Cloud
- On-Premise
By Enterprise Size
- Small and Medium Enterprises
- Large Enterprises
By Application
- Windows
- Unix and Linux
- Mac OS
- Infrastructure Devices and IoT
By End-User
- Healthcare
- BFSI
- Government
- Energy and Utilities
- Manufacturing
- Retail
- IT and Telecom
- Other End-Users
Key Companies Analysed
- Arcon Techsolutions Private Limited
- BeyondTrust Corporation
- CA Technologies Inc.
- Avatier Corporation
- CyberArk Software Ltd.
- Hitachi Ltd.
- Lieberman Software Corporation
- Zoho Corporation Pvt. Ltd.
- Onion ID Inc.
- Osirium Technologies plc
- Peritus Inc.
- Remediant Inc.
- Silverfort Ltd.
- SolarWinds Corporation
- SSH Communications Security corporation
- Systancia SA
- International Business Machines Corp.
- Micro Focus International plc
- Okta ASA
- HashiCorp Inc.
- Broadcom Inc.
- StrongDM
- Bitium Corporation
- Keeper Security Inc.
- McAfee Corp.
- Netwrix Corporation
- Quest Software Inc.
- Akamai Technologies Inc.
- ManageEngine Password Manager Pro
Privileged Access Management Solutions Market Analytics
The report employs rigorous tools, including Porter’s Five Forces, value chain mapping, and scenario-based modeling, to assess supply-demand dynamics. Cross-sector influences from parent, derived, and substitute markets are evaluated to identify risks and opportunities. Trade and pricing analytics provide an up-to-date view of international flows, including leading exporters, importers, and regional price trends.Macroeconomic indicators, policy frameworks such as carbon pricing and energy security strategies, and evolving consumer behavior are considered in forecasting scenarios. Recent deal flows, partnerships, and technology innovations are incorporated to assess their impact on future market performance.
Privileged Access Management Solutions Market Competitive Intelligence
The competitive landscape is mapped through proprietary frameworks, profiling leading companies with details on business models, product portfolios, financial performance, and strategic initiatives. Key developments such as mergers & acquisitions, technology collaborations, investment inflows, and regional expansions are analyzed for their competitive impact. The report also identifies emerging players and innovative startups contributing to market disruption.Regional insights highlight the most promising investment destinations, regulatory landscapes, and evolving partnerships across energy and industrial corridors.
Countries Covered
- North America - Privileged Access Management Solutions market data and outlook to 2034
- United States
- Canada
- Mexico
- Europe - Privileged Access Management Solutions market data and outlook to 2034
- Germany
- United Kingdom
- France
- Italy
- Spain
- BeNeLux
- Russia
- Sweden
- Asia-Pacific - Privileged Access Management Solutions market data and outlook to 2034
- China
- Japan
- India
- South Korea
- Australia
- Indonesia
- Malaysia
- Vietnam
- Middle East and Africa - Privileged Access Management Solutions market data and outlook to 2034
- Saudi Arabia
- South Africa
- Iran
- UAE
- Egypt
- South and Central America - Privileged Access Management Solutions market data and outlook to 2034
- Brazil
- Argentina
- Chile
- Peru
Research Methodology
This study combines primary inputs from industry experts across the Privileged Access Management Solutions value chain with secondary data from associations, government publications, trade databases, and company disclosures. Proprietary modeling techniques, including data triangulation, statistical correlation, and scenario planning, are applied to deliver reliable market sizing and forecasting.Key Questions Addressed
- What is the current and forecast market size of the Privileged Access Management Solutions industry at global, regional, and country levels?
- Which types, applications, and technologies present the highest growth potential?
- How are supply chains adapting to geopolitical and economic shocks?
- What role do policy frameworks, trade flows, and sustainability targets play in shaping demand?
- Who are the leading players, and how are their strategies evolving in the face of global uncertainty?
- Which regional “hotspots” and customer segments will outpace the market, and what go-to-market and partnership models best support entry and expansion?
- Where are the most investable opportunities - across technology roadmaps, sustainability-linked innovation, and M&A - and what is the best segment to invest over the next 3-5 years?
Your Key Takeaways from the Privileged Access Management Solutions Market Report
- Global Privileged Access Management Solutions market size and growth projections (CAGR), 2024-2034
- Impact of Russia-Ukraine, Israel-Palestine, and Hamas conflicts on Privileged Access Management Solutions trade, costs, and supply chains
- Privileged Access Management Solutions market size, share, and outlook across 5 regions and 27 countries, 2023-2034
- Privileged Access Management Solutions market size, CAGR, and market share of key products, applications, and end-user verticals, 2023-2034
- Short- and long-term Privileged Access Management Solutions market trends, drivers, restraints, and opportunities
- Porter’s Five Forces analysis, technological developments, and Privileged Access Management Solutions supply chain analysis
- Privileged Access Management Solutions trade analysis, Privileged Access Management Solutions market price analysis, and Privileged Access Management Solutions supply/demand dynamics
- Profiles of 5 leading companies - overview, key strategies, financials, and products
- Latest Privileged Access Management Solutions market news and developments
Additional Support
With the purchase of this report, you will receive:- An updated PDF report and an MS Excel data workbook containing all market tables and figures for easy analysis.
- 7-day post-sale analyst support for clarifications and in-scope supplementary data, ensuring the deliverable aligns precisely with your requirements.
- Complimentary report update to incorporate the latest available data and the impact of recent market developments.
This product will be delivered within 1-3 business days.
Table of Contents
Companies Mentioned
- Arcon Techsolutions Private Limited
- BeyondTrust Corporation
- CA Technologies Inc.
- Avatier Corporation
- CyberArk Software Ltd.
- Hitachi Ltd.
- Lieberman Software Corporation
- Zoho Corporation Pvt. Ltd.
- Onion ID Inc.
- Osirium Technologies PLC
- Peritus Inc.
- Remediant Inc.
- Silverfort Ltd.
- SolarWinds Corporation
- SSH Communications Security corporation
- Systancia SA
- International Business Machines Corp.
- Micro Focus International PLC
- Okta ASA
- HashiCorp Inc.
- Broadcom Inc.
- StrongDM
- Bitium Corporation
- Keeper Security Inc.
- McAfee Corp.
- Netwrix Corporation
- Quest Software Inc.
- Akamai Technologies Inc.
- ManageEngine Password Manager Pro
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 160 |
| Published | October 2025 |
| Forecast Period | 2025 - 2034 |
| Estimated Market Value ( USD | $ 6.7 Billion |
| Forecasted Market Value ( USD | $ 41.9 Billion |
| Compound Annual Growth Rate | 22.6% |
| Regions Covered | Global |
| No. of Companies Mentioned | 29 |