Speak directly to the analyst to clarify any post sales queries you may have.
Wireless network security is a critical priority for enterprises navigating an environment defined by escalating cyber threats, regulatory demands, and rapid adoption of advanced connectivity solutions. As organizations accelerate digital transformation, understanding market forces and best practices is essential for building resilient, scalable security architectures.
Market Snapshot: Wireless Network Security Market Growth and Trends
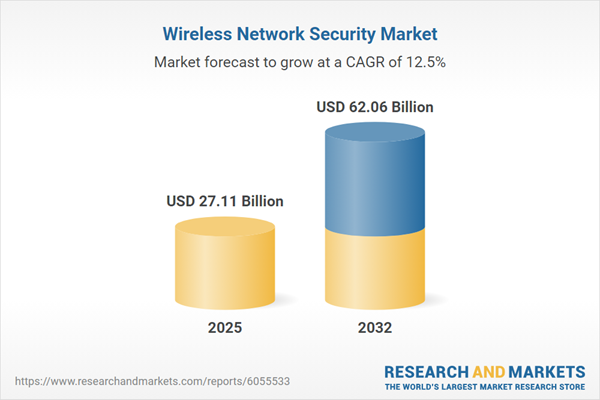
The wireless network security market is expanding, driven by ubiquitous enterprise wireless adoption, cloud migration, and regulatory pressure. From 2024 to 2025, the sector grows from USD 24.23 billion to USD 27.11 billion and continues at a 12.47% CAGR, targeting USD 62.06 billion by 2032. This reflects growing investments in advanced threat detection, cloud-based protections, and compliance-focused solutions as organizations strive to protect mission-critical data and infrastructure.
Scope & Segmentation: In-Depth Market Coverage
- Type: Hardware (including active, passive, and preventive devices), Services (managed and professional), Software (antivirus, encryption, identity and access management)
- Protocol Type: Wi-Fi Protected Access (WPA, WPA2, WPA3), Wired Equivalent Privacy (WEP)
- Deployment Mode: Cloud-based and on-premise solutions
- Organization Type: Large enterprises, small & medium enterprises
- End-User Industry: Banking and financial services, education, government & public sector, healthcare, IT & telecommunication, retail & consumer goods
- Geographic Coverage: Americas (United States, Canada, Mexico; Brazil, Argentina, Chile, Colombia, Peru), Europe, Middle East & Africa (United Kingdom, Germany, France, Russia, Italy, Spain, Netherlands, Sweden, Poland, Switzerland; UAE, Saudi Arabia, Qatar, Turkey, Israel; South Africa, Nigeria, Egypt, Kenya), Asia-Pacific (China, India, Japan, Australia, South Korea, Indonesia, Thailand, Malaysia, Singapore, Taiwan)
- Key Vendors: ALE International, AO Kaspersky Lab, ASSA ABLOY, Barracuda Networks, Broadcom, Check Point, Cisco Systems, Extreme Networks, F5, Fortinet, Hewlett Packard Enterprise, Huawei, Juniper Networks, McAfee, Musarubra US, Palo Alto Networks, Radware, RUCKUS Networks, SonicWall International, Sophos, Trend Micro, Ubiquiti, WatchGuard Technologies, Zscaler, ZTE Corporation
Key Takeaways: Insights for Senior Decision-Makers
- Heightened digital transformation and remote work adoption have expanded the wireless attack surface, requiring more sophisticated defense strategies.
- Technological advancements such as AI-powered analytics and zero trust architectures are now foundational for threat detection and response capabilities.
- Regulatory requirements are intensifying across regions, prompting enhanced compliance measures and driving demand for robust identity and access management controls.
- Industry-specific needs influence solution priorities, with finance, government, healthcare, and retail demanding tailored encryption and policy enforcement models.
- Strategic collaboration between global vendors and agile innovators is shaping product development and accelerating deployment of next-generation solutions.
- Supply chain resilience and flexible procurement are increasingly important as geopolitical factors and trade actions impact sourcing and investment decisions.
Tariff Impact: Navigating U.S. Trade Measures
Recent U.S. tariff measures have altered procurement dynamics in the wireless network security sector, motivating organizations to reconsider supplier relationships and boost domestic manufacturing. This has led to a focus on modular, locally assembled hardware, as well as greater investment in proprietary technology to reduce import dependence. Managed security service bundles and adaptive vendor strategies have emerged to help enterprises control costs without compromising security standards or performance.
Wireless Network Security: Methodology & Data Sources
This analysis employs structured secondary research, expert interviews, and data triangulation. Findings were validated through vendor reports, regulatory filings, and peer-panel reviews to ensure accuracy and practical relevance in every aspect of the wireless network security market.
Why This Report Matters
- Supports executive IT and security leaders in optimizing wireless security investments aligned with organizational priorities and compliance needs.
- Equips stakeholders with detailed market segmentation, benchmarking, and competitor analysis for informed procurement and partnership decisions.
- Delivers strategic guidance to enhance risk mitigation, operational agility, and market positioning as wireless security threats and technology evolve.
Conclusion
Senior decision-makers can use this report to develop actionable strategies that strengthen wireless security posture and address emerging technology and regulatory demands. Comprehensive analysis ensures confidence in future planning and risk management initiatives across enterprise environments.
Table of Contents
3. Executive Summary
4. Market Overview
7. Cumulative Impact of Artificial Intelligence 2025
Companies Mentioned
The companies profiled in this Wireless Network Security market report include:- ALE International
- AO Kaspersky Lab
- ASSA ABLOY
- Barracuda Networks, Inc.
- Broadcom
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Extreme Networks, Inc.
- F5, Inc.
- Fortinet, Inc.
- Hewlett Packard Enterprise Company
- Huawei Technologies Co., Ltd.
- Juniper Networks, Inc.
- McAfee LLC
- Musarubra US LLC
- Palo Alto Networks
- Radware Ltd.
- RUCKUS Networks
- SonicWall International DAC
- Sophos Limited
- Trend Micro Incorporated.
- Ubiquiti, Inc.
- WatchGuard Technologies, Inc.
- Zscaler, Inc.
- ZTE Corporation
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 188 |
| Published | November 2025 |
| Forecast Period | 2025 - 2032 |
| Estimated Market Value ( USD | $ 27.11 Billion |
| Forecasted Market Value ( USD | $ 62.06 Billion |
| Compound Annual Growth Rate | 12.4% |
| Regions Covered | Global |
| No. of Companies Mentioned | 26 |