Speak directly to the analyst to clarify any post sales queries you may have.
Setting the strategic context for point-of-sale security by outlining core challenges, stakeholder priorities, and the competitive environment influencing procurement and operations
This executive summary introduces a comprehensive analysis of point-of-sale security, emphasizing the practical implications for technology leaders, procurement teams, and security operations. The narrative synthesizes prevailing threat vectors, supply chain dynamics, and vendor behaviors that collectively shape how organizations plan and execute protective measures at the transaction edge. It also clarifies the relationship between product design choices and operational resilience so that decision-makers can weigh trade-offs with clarity and confidence.
Readers will find a concise framing of current challenges alongside observed industry responses, organized to support strategic decision-making. The introduction sets expectations for the remainder of the report by highlighting the diagnostic approach used to identify high-impact vulnerabilities and the operational levers available to mitigate them. In doing so, it orients stakeholders toward practical actions while maintaining a view of systemic risks that transcend individual deployments.
Throughout this section, emphasis is placed on interoperability, regulatory alignment, and lifecycle management of security technologies. These themes are threaded into discussions about procurement, service partnerships, and internal governance to ensure the recommendations that follow are grounded in organizational realities. Ultimately, this introduction positions readers to interpret subsequent insights through the lens of both immediate remediation and longer-term resilience planning.
Evaluating transformative technological and operational shifts that are reshaping point-of-sale security architectures, threat detection approaches, and procurement practices at scale
The landscape of point-of-sale security is undergoing rapid transformation driven by technological advances, evolving attacker sophistication, and shifting business models. Artificial intelligence and machine learning have moved from experimental to operational phases within fraud detection and behavioral analytics, altering how anomalies are surfaced and prioritized. At the same time, improvements in authentication hardware and biometric modalities are expanding the available options for securing endpoints, creating new pathways to reduce reliance on legacy PIN- and card-based mechanisms.
Concurrently, the architecture of deployments is shifting toward hybrid approaches that blend cloud services with on-premises controls. This hybrid trajectory supports scalability and centralized threat intelligence while preserving latency-sensitive functions locally. As a result, operational teams must reconcile the benefits of centralized analytics with the constraints of regulatory jurisdictions and data sovereignty, which frequently demand localized controls. Supply chain resilience has also become a central concern, with procurement strategies evolving to include multi-sourcing, stricter component provenance verification, and contractual security requirements for vendors.
These transformative shifts elevate the importance of integrated security roadmaps that align technology choices with governance, vendor management, and continuous monitoring. In this context, organizations that adopt modular, standards-based architectures will find it easier to adapt to emergent threats and to integrate third-party innovations without disruptive rip-and-replace cycles. The net effect is a dynamic environment in which agility, validated interoperability, and robust vendor governance determine the pace of secure innovation.
Assessing the cumulative operational and supply chain effects of United States tariffs announced in 2025 on component sourcing, procurement policies, and vendor risk frameworks
The tariff measures enacted by the United States in 2025 have introduced a new set of considerations for organizations that depend on cross-border supply chains and specialized hardware for point-of-sale security. Although tariffs are often discussed in macroeconomic terms, their operational impact crystallizes in procurement timelines, component lead times, and the relative economics of sourcing from different geographies. Procurement teams must now balance cost pressures with the need to maintain validated supply chains and to avoid introducing unvetted suppliers into sensitive security ecosystems.
In response, many organizations are accelerating supplier diversification and re-evaluating vendor contractual terms to incorporate stronger indemnities, security attestations, and audit rights. This reorientation affects not only hardware sourcing but also the delivery of installation and managed services, where labor and service delivery models may shift to regional partners to contain tariff-related cost volatility. Additionally, some vendors are revising their manufacturing footprints and component sourcing strategies to mitigate exposure, which in turn changes lead times and the availability of specific device models or security tokens.
From an operational perspective, continued emphasis on standards-based interfaces and modular designs helps mitigate disruption by allowing organizations to substitute components or suppliers with minimal integration friction. Procurement and security leaders should therefore prioritize contractual flexibility, enforceable security SLAs, and contingency planning for critical components. In sum, tariff-driven pressures are not isolated cost events; they catalyze broader shifts in supplier strategy and risk management that will shape technology roadmaps and vendor relationships going forward.
Comprehensive segmentation insights demonstrating how component, application, industry vertical, and deployment choices create differentiated security needs and procurement priorities
A clear segmentation framework is essential to understand where investments and risk mitigation will deliver the greatest returns. When analyzed by component, the market divides into hardware, services, and software. Hardware comprises biometric scanners, card readers, PIN pads, and security tokens, each presenting distinct lifecycle and supply concerns; services encompass installation services, maintenance & support, and managed services, reflecting the balance between in-house capability and outsourced expertise; and software spans access control, authentication, fraud detection, intrusion detection, and payment security, with each software domain requiring distinct integration and update cadences. Within software, access control further differentiates into badge-based and PIN-based mechanisms, authentication into biometrics and two-factor systems, fraud detection into AI-based and rule-based approaches, intrusion detection into host-based and network-based systems, and payment security into EMV, encryption, and tokenization methods, all of which interact with hardware capabilities to form complete solutions.
When the same segmentation lens is applied to applications, the focal areas mirror those component-level domains: access control, authentication, fraud detection, intrusion detection, and payment security. Access control again bifurcates into badge-based and PIN-based methods, and authentication divides into biometric and two-factor approaches. Fraud detection contrasts AI-driven analytics with rule-based engines, while intrusion detection requires consideration of host-based versus network-based tooling. Payment security remains centered on EMV, encryption, and tokenization, which are central to preserving transaction integrity.
Considering end-user industries adds critical context for prioritization and deployment nuance. Industries such as banking, financial services and insurance distinguish needs across ATMs, banks, and insurance operations; healthcare requires tailored solutions for clinics, hospitals, and pharmacies where patient privacy and clinical workflows are paramount; hospitality spans casinos, hotels, and restaurants that must balance frictionless guest experiences with theft mitigation; retail includes e-commerce platforms, specialty stores, and supermarkets where omnichannel integration is vital; and transportation covers airlines, logistics, and railways where distributed operations and high-volume transaction processing challenge traditional controls.
The deployment mode segmentation underscores trade-offs between agility and control. Cloud deployments, whether hybrid cloud, private cloud, or public cloud, offer centralized analytics and rapid updates, but they impose data residency and integration considerations. On-premises options, both custom and off-the-shelf, provide tighter operational control and lower latency, yet they require clearer internal governance and lifecycle provisioning. Across all segmentation axes, the strongest strategic outcomes arise from architectures that prioritize modularity, interoperable standards, and clear responsibilities between vendors and operators to reduce integration risk and accelerate secure feature adoption.
Key regional dynamics and nuanced market drivers across the Americas, Europe Middle East & Africa, and Asia-Pacific that shape procurement, compliance, and deployment strategies
Regional dynamics materially influence how point-of-sale security solutions are selected, deployed, and governed. In the Americas, regulatory regimes and consumer expectations emphasize strong payment security and fraud detection, driving demand for solutions that integrate EMV, tokenization, and AI-based fraud analytics while retaining flexibility for both cloud and on-premises deployments. The vendor ecosystem in this region tends to favor rapid innovation cycles supported by mature managed services and a dense partner network, which enables fast pilot-to-production pathways.
Across Europe, the Middle East & Africa, regulatory diversity and data protection frameworks shape deployment architectures, particularly where data residency and privacy are primary concerns. Organizations in these geographies frequently adopt hybrid models to maintain centralized threat intelligence while complying with local controls. Vendor selection here weighs heavily on interoperability, certification, and the ability to demonstrate compliance with varied legal regimes. In addition, emerging economies in the region prioritize cost-effective, resilient hardware and pragmatic managed service arrangements to accommodate resource constraints.
In the Asia-Pacific region, a combination of high-volume retail ecosystems, rapid digital payments adoption, and significant manufacturing capacity influences both demand and supply. Regional suppliers and manufacturing partners play an outsized role in hardware availability and cost structures, while innovation in mobile authentication and alternative payment methods requires solutions that are adaptable to diverse consumer behaviors. Across this region, scalability and localization capabilities are critical, with organizations seeking partners that can deliver both global standards compliance and tailored integration for local payment rails and authentication norms.
Taken together, these regional distinctions underscore the importance of tailoring procurement strategies, vendor due diligence, and operational models to local regulatory landscapes, consumer expectations, and supply chain realities. Organizations that align regional deployment plans with consistent governance and adaptable architectures will be better positioned to deploy resilient and compliant point-of-sale security solutions.
Profiles of leading vendors and strategic differentiators that determine technology adoption, partnership strategies, and service delivery models across point-of-sale security
Leading vendors in the point-of-sale security space are differentiated by their ability to integrate hardware robustness, software intelligence, and service continuity into cohesive solutions. Companies that maintain strong manufacturing controls and diversified component sourcing protect customers from supply disruptions and tariff-driven cost volatility. At the same time, vendors that invest in AI-driven fraud detection and modular authentication stacks enable faster adaptation to emergent threat patterns while minimizing dependence on monolithic platforms.
Strategic partnerships between hardware manufacturers, software providers, and regional service integrators are increasingly common, enabling a layered value proposition that combines certified devices with real-time analytics and managed services. Vendors that offer clear upgrade paths, standardized APIs, and comprehensive developer support reduce integration friction for enterprise customers. Furthermore, those with transparent security testing regimes, independent certifications, and mature incident response capabilities are more likely to earn procurement trust, particularly from industries with strict compliance requirements.
From a service perspective, companies that provide bundled lifecycle services-covering installation, maintenance, and managed detection-help buyers shift operational risk while ensuring consistent patching and vulnerability management. Conversely, vendors that rely on constrained or proprietary interfaces risk slowing enterprise adoption and increasing long-term total cost of ownership. In this competitive environment, differentiation is achieved through a combination of technological leadership, proven operational support, and verifiable governance practices that meet the needs of both security teams and business stakeholders.
Actionable strategic recommendations for industry leaders to strengthen point-of-sale security, optimize supply chain resilience, and accelerate secure innovation with measurable governance
Industry leaders must adopt a pragmatic, prioritized approach to harden point-of-sale systems while preserving business continuity and customer experience. First, organizations should enforce modular architectures that allow component substitution without system-wide rework, prioritizing standardized interfaces and certified integrations. This reduces vendor lock-in risk and permits rapid response to supply chain disruptions or security advisories. Next, embedding AI-based fraud detection and robust tokenization into transaction flows can materially reduce fraud exposure, provided that these capabilities are integrated with human-in-the-loop processes and continuous model validation.
Operational controls must include enforceable vendor security requirements, contractual SLAs for incident response, and periodic third-party validation of device firmware and software. In parallel, organizations should revisit procurement strategies to include multi-sourcing, security-focused contract clauses, and inventory of critical component origins. For deployments spanning multiple jurisdictions, hybrid cloud strategies with localized processing nodes enable centralized analytics while meeting data residency obligations. Workforce readiness is also essential: investing in training for security operations teams and service partners ensures that upgrades, patching, and incident handling are performed consistently and efficiently.
Finally, leaders should adopt a measurement-centric governance model that ties security investments to defined operational KPIs such as mean time to detect and remediate, transaction fraud rates, and uptime for critical payment functions. By aligning these metrics with business objectives, organizations can make defensible investment decisions, optimize vendor relationships, and accelerate secure innovation without introducing unnecessary operational friction.
Robust research methodology detailing multi-method data collection, validation protocols, and analytical frameworks used to produce actionable and reliable point-of-sale security insights
The analysis underpinning this summary uses a multi-method research approach combining primary interviews, technical validation, and cross-sector comparative analysis to ensure robustness and relevance. Primary qualitative inputs were gathered from security architects, procurement leaders, and service providers to capture operational realities, vendor selection criteria, and regional deployment nuances. Technical validation included review of device interfaces, software update mechanisms, and interoperability evidence to assess practical integration challenges and upgrade pathways.
Analytical frameworks applied in the research include risk-based segmentation, supply chain resilience mapping, and vendor capability scoring across technology, services, and governance dimensions. These frameworks were used to triangulate findings and to identify high-leverage interventions for organizations across different industry verticals. Validation protocols involved cross-referencing interview insights with observable vendor documentation, third-party certification records, and public incident histories to reduce bias and ensure factual accuracy.
Throughout the research process, particular attention was paid to temporal relevance by prioritizing recent technical changes, policy shifts, and supply chain developments. This focus on currency enhances the applicability of the recommendations and supports decision-making that accounts for both immediate remediation needs and longer-term strategic investments. The methodology is designed to be transparent, repeatable, and adaptable for follow-on engagements tailored to specific organizational contexts.
Concluding perspectives on resilience, governance, and strategic priorities that organizations must adopt to effectively harden point-of-sale security and sustain business continuity
In conclusion, the point-of-sale security landscape is characterized by converging pressures: advancing threat capabilities, shifting procurement dynamics, and evolving regulatory expectations. Together, these forces demand strategic responses that emphasize modular architectures, verified vendor governance, and operational metrics that link security investments to business outcomes. Organizations that proactively adopt standards-based integration, diversify supply chains, and implement continuous detection capabilities will be better positioned to manage both immediate risks and long-term resilience.
The path forward requires coordinated action across procurement, security operations, and executive leadership. Short-term priorities should focus on addressing known vulnerabilities, enforcing vendor accountability, and ensuring that critical firmware and software update processes are robust. Medium-term efforts ought to prioritize architectural flexibility-particularly through hybrid deployment strategies and standardized APIs-while long-term success will hinge on cultivating ecosystems of certified partners and on embedding security into product lifecycles.
Ultimately, resilience in point-of-sale security is achieved by treating security as a systemic capability rather than a set of point solutions. By aligning technology choices with governance, supply chain management, and measurable operational goals, organizations can reduce exposure to both technical and economic shocks and sustain secure payment experiences for their customers.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
16. China POS Security Market
Companies Mentioned
The key companies profiled in this POS Security market report include:- Block, Inc.
- Bluefin Payment Systems LLC
- Braintree
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Clover Network, Inc.
- Elavon Inc.
- Fortinet, Inc.
- Heartland Payment Systems, Inc.
- Ingenico
- McAfee Corp.
- Palo Alto Networks, Inc.
- PAX Technology Limited
- Thales Group
- Toast, Inc.
- Verifone Systems, Inc.
- Visa Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 194 |
| Published | January 2026 |
| Forecast Period | 2026 - 2032 |
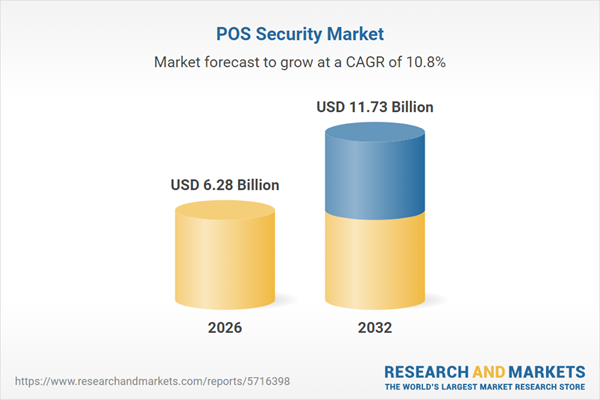
| Estimated Market Value ( USD | $ 6.28 Billion |
| Forecasted Market Value ( USD | $ 11.73 Billion |
| Compound Annual Growth Rate | 10.7% |
| Regions Covered | Global |
| No. of Companies Mentioned | 19 |