Speak directly to the analyst to clarify any post sales queries you may have.
An authoritative introduction to software-defined security framing policy-driven controls as a strategic enabler for resilient and agile digital operations
Software-defined security reframes traditional perimeter and point-product approaches by decoupling policy, control, and orchestration from underlying hardware. This paradigm shift enables organizations to apply consistent, context-aware protections across dynamic workloads and heterogeneous environments. As enterprises adopt cloud-native application architectures, distributed endpoints, and interconnected supply chains, security must evolve from static appliances to programmable, policy-driven services that operate at software speed.
Adopters benefit from rapid policy iteration, centralized visibility, and automated enforcement that reduce mean time to respond while improving operational efficiency. However, realizing those benefits requires coherent governance, rigorous identity controls, and an integration mindset that treats security as an enabler of business outcomes rather than a siloed cost center. In practice, successful implementations combine automation with human oversight to balance velocity and control, supported by telemetry that enables continuous improvement.
This introduction establishes the foundational premise that software-defined security is not merely a set of technologies but a design principle. It emphasizes the importance of aligning technical choices with organizational risk appetite and operational maturity. By framing the problem this way, leaders can prioritize investments that yield measurable improvements in resilience, agility, and compliance without introducing excessive complexity.
How evolving architectures, adversary techniques, and regulatory pressures are reshaping enterprise defense models toward programmable and composable security
The security landscape is undergoing transformative shifts driven by changes in architecture, threat sophistication, and regulatory expectations. Cloud-native architectures and microservices have proliferated, creating ephemeral attack surfaces that challenge legacy inspection and control approaches. Simultaneously, adversaries are leveraging automated tooling, supply chain exploits, and identity-based attacks that require defensive strategies focused on signal enrichment, behavioral analytics, and identity-first controls.
In response, organizations are adopting a layered approach where orchestration, telemetry, and policy are centralized but enforcement points remain distributed. This hybrid posture allows for consistent policy intent while enabling localized, latency-sensitive enforcement. Vendor ecosystems are evolving as well, with interoperability and open standards gaining importance, enabling best-of-breed integration across application security, cloud posture management, and workload protection.
Organizational change management is equally critical: security teams must upskill in software engineering practices and collaborate closely with development and operations counterparts. Over time, these shifts favor architectures that embed security into the development lifecycle, leverage automation for repetitive hygiene tasks, and apply composable controls that can be tuned to specific environments. The net effect is a move away from monolithic defenses toward more granular, context-aware security that scales with modern infrastructures.
Assessing how recent tariff adjustments have accelerated the transition to software-first security solutions and reshaped supply chain and procurement strategies for resilience
The cumulative impact of U.S. tariff changes announced in 2025 has introduced new considerations for security operations, procurement, and global supply chain risk management. Increased tariffs on certain hardware components have accelerated the shift toward software-centric solutions and cloud-hosted services, prompting organizations to evaluate the total cost and resilience trade-offs of hardware-dependent appliances versus virtualized or managed services.
Procurement cycles are being re-evaluated as organizations weigh the operational benefits of on-premises equipment against the agility of cloud-delivered controls. For multinational enterprises, tariff-driven cost pressures underscore the importance of diversified supplier relationships and software portability. At the same time, security teams must account for potential delays in hardware refresh programs and the implications for lifecycle management and vendor support timelines.
Regulatory scrutiny of supply chain integrity has intensified in parallel, requiring enhanced third-party risk assessments, code provenance validation, and firmware attestation practices. Consequently, security architectures have begun to prioritize modularity and vendor-agnostic interoperability to mitigate exposure from single-source dependencies. In short, tariffs have acted as an accelerant for existing trends favoring software-defined controls and supply-chain-aware procurement strategies, reinforcing the need for flexible security architectures that can adapt as commercial and geopolitical conditions evolve.
Detailed segmentation-driven insights that map security types, deployment choices, industry-specific risks, and organizational scale to practical implementation priorities
Segmentation analysis reveals nuanced requirements across different technology layers, deployment models, end users, and organizational scales, each shaping adoption pathways and integration needs. Based on Security Type, offerings span Application Security with controls such as Dynamic Application Security Testing, Runtime Application Self-Protection, Static Application Security Testing, and Web Application Firewall; Cloud Security provided through Cloud Access Security Broker, Cloud Security Posture Management, and Cloud Workload Protection Platform; Data Security that includes Data Loss Prevention, Database Activity Monitoring, Encryption, and Tokenization; Endpoint Security composed of Antivirus & Antimalware, Endpoint Detection & Response, and Mobile Security; Identity & Access Management encompassing Identity Governance, Multi-Factor Authentication, Privileged Access Management, and Single Sign-On; and Network Security implementing DDoS Mitigation, Intrusion Prevention System, Next-Generation Firewall, Secure Web Gateway, and VPN.
Deployment Model choices between Cloud, Hybrid, and On-Premises dictate integration patterns, latency tolerances, and telemetry aggregation strategies. End User verticals present different threat models and compliance imperatives: BFSI covers Banking, Capital Markets, and Insurance with high regulatory demands and identity-centered risk; Energy & Utilities spans Oil & Gas, Renewable Energy, and Utilities with operational technology intersections and availability-focused risk; Government emphasizes sovereignty and classified data handling; Healthcare includes Hospitals, Medical Devices, and Pharmaceuticals with patient safety and data privacy concerns; IT & Telecom includes IT Services and Telecom Providers that require large-scale authentication and routing resilience; Manufacturing incorporates Automotive Manufacturing, Discrete, and Process Manufacturing where OT/IT convergence is prevalent; and Retail covers Brick-And-Mortar and Online Retail where payment systems and customer data are in focus. Organization Size ranges from Large Enterprise to Small And Medium Enterprise, with the latter further subdivided into Medium Business and Small Business, which influences governance velocity, procurement sophistication, and tolerance for turnkey versus customizable solutions.
Taken together, these segmentation axes underscore that successful software-defined security strategies must be contextually tailored. Integration priorities differ when protecting cloud workloads for a large financial institution compared with securing distributed retail endpoints for a small business. Therefore, architects and procurement teams should align solution selection with the combined requirements of security type, deployment model, vertical risk profile, and organizational scale to achieve durable outcomes.
How regional regulatory regimes, operational priorities, and infrastructure realities shape adoption patterns and integration strategies for software-defined security
Regional dynamics significantly influence technology selection, regulatory compliance, and supply chain strategies in software-defined security implementations. In the Americas, enterprises often prioritize rapid innovation, cloud adoption, and identity-driven controls, while navigating a complex regulatory environment that includes data protection and sector-specific compliance obligations. This region tends to favor managed service engagements and hybrid deployments that balance agility and control.
Europe, Middle East & Africa present a heterogeneous landscape where regulatory regimes, data residency requirements, and geopolitical considerations shape architecture choices. Organizations in this region place a premium on privacy-by-design, strong encryption standards, and demonstrable supply chain assurances. The need to harmonize cross-border operations and local compliance makes standardized telemetry schemas and interoperable APIs particularly valuable.
Asia-Pacific exhibits a blend of rapid cloud adoption, diverse regulatory frameworks, and strong demand for localized managed services. Regional priorities often include latency-sensitive controls, mobile security, and identity federation across varied ecosystems. Across all regions, there is a common trend toward decentralizing enforcement while centralizing policy intent, which supports consistent risk posture management while enabling local performance optimization. Ultimately, regional nuance informs vendor selection, integration patterns, and the level of customization required to meet operational and compliance demands.
Competitive vendor strategies emphasizing extensibility, partnerships, and managed operations to deliver unified control planes and specialized defensive capabilities
Leading vendors and emerging challengers are pursuing differentiated strategies that emphasize platform extensibility, ecosystem partnerships, and managed service offerings. Established vendors are integrating telemetry ingestion, analytics, and policy orchestration capabilities into broader security platforms to provide a unified control plane across endpoints, networks, and cloud workloads. At the same time, specialist providers are deepening domain expertise in areas such as runtime application self-protection, cloud workload protection, and identity governance to address high-value use cases.
Strategic partnerships between platform providers, cloud hyperscalers, and systems integrators are becoming more common as customers demand turnkey operational models and validated reference architectures. Acquisitions and technology integrations are also enabling vendors to fill capability gaps quickly, but this has increased the importance of standards-based interoperability and open APIs to avoid vendor lock-in. In parallel, managed service providers are packaging orchestration, monitoring, and response capabilities, which helps organizations that lack in-house engineering capacity to accelerate adoption.
Buyers should evaluate vendors based on their ability to support cross-domain policy consistency, provide rich telemetry for incident detection and investigation, and enable automation that reduces manual operational burden. Additionally, vendors that offer clear roadmaps for standards alignment and third-party integrations will be better positioned to support long-term, adaptable security programs.
Actionable recommendations for executives to operationalize software-defined security through identity-first controls, phased automation, and supplier resilience measures
Industry leaders should prioritize pragmatic, high-impact measures that accelerate value capture while reducing operational friction. First, establish a clear policy taxonomy that maps business-critical assets and transactions to enforceable controls; this taxonomy should drive automation rules, telemetry collection, and incident prioritization. Concurrently, invest in identity-first architectures that centralize identity governance, multi-factor authentication, and privileged access management to reduce attack surface and lateral movement risk.
Next, adopt a phased approach to software-defined controls that sequences low-friction wins-such as centralized visibility and posture assessment-before introducing complex runtime defenses. Integrate application security tools such as SAST, DAST, and RASP into the development pipeline to shift detection left and reduce remediation cost. For cloud and hybrid environments, prioritize cloud workload protection and cloud security posture management to ensure continuous compliance and runtime hygiene.
Operationally, augment automation with human-in-the-loop oversight for ambiguous events and retention of institutional knowledge. Strengthen supplier risk programs to include firmware attestation and software provenance checks, and design procurement contracts that incentivize interoperability and secure lifecycle management. Finally, measure program health with outcome-focused metrics tied to business impact, such as reduction in time-to-detect for critical assets and consistency of policy enforcement across environments.
A reproducible, practitioner-centered methodology leveraging direct interviews, technical validation, and secondary analysis to ensure transparent and actionable findings
The research methodology combines primary and secondary approaches to create a triangulated evidence base that supports pragmatic conclusions. Primary research includes structured interviews with security practitioners, architects, and procurement leaders across multiple industries to capture real-world implementation patterns, operational constraints, and vendor evaluation criteria. These qualitative inputs are complemented by technical validation exercises that assess integration patterns, telemetry fidelity, and enforcement latency across representative deployment scenarios.
Secondary research synthesizes regulatory documents, threat intelligence reports, vendor technical documentation, and publicly disclosed incident analyses to contextualize primary findings. Where applicable, trend analysis examines adoption patterns and technology maturation without relying on proprietary market-sizing metrics. Cross-validation techniques are applied to ensure consistency between practitioner claims and technical observations, and methodological transparency is maintained through documented assumptions and reproducible validation steps.
Ethical considerations and data privacy safeguards are integrated into the research process. Interviewee identities and organizational affiliations are anonymized in aggregated outputs, and any illustrative examples are de-identified. The methodology is designed to be repeatable and to support subsequent deep-dive engagements tailored to specific organizational contexts.
Concluding synthesis emphasizing incremental, identity-first approaches and interoperability as the foundation for resilient software-defined security programs
In conclusion, software-defined security represents a practical evolution in how organizations translate risk appetite into enforceable controls across distributed and cloud-centric environments. The combination of programmable policy, centralized intent, and distributed enforcement enables more consistent protection while preserving the performance and agility demands of modern applications. However, realizing these benefits requires intentional alignment between security, development, and operations teams, as well as procurement strategies that favor interoperability and supply chain resilience.
Regulatory shifts and commercial pressures, including tariff-driven changes in hardware economics, further emphasize the need for software-first architectures and flexible deployment models. Successful programs will prioritize identity-first controls, telemetry consolidation, and phased automation that deliver measurable improvements without overwhelming operational teams. Vendors and service providers that demonstrate open integration models, robust telemetry, and operational support will be best positioned to help organizations transition.
Ultimately, the path to durable, adaptable security is iterative: build a policy foundation, instrument for observability, automate repeatable responses, and refine controls through feedback loops. By following this sequence, organizations can strengthen their security posture while enabling the speed and innovation that modern business models demand.
Additional Product Information:
- Purchase of this report includes 1 year online access with quarterly updates.
- This report can be updated on request. Please contact our Customer Experience team using the Ask a Question widget on our website.
Table of Contents
7. Cumulative Impact of Artificial Intelligence 2025
16. China Software-Defined Security Market
Companies Mentioned
The key companies profiled in this Software-Defined Security market report include:- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Fortinet, Inc.
- IBM Corporation
- Juniper Networks, Inc.
- Palo Alto Networks, Inc.
- Trend Micro Inc.
- VMware, Inc.
- Zscaler, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 197 |
| Published | January 2026 |
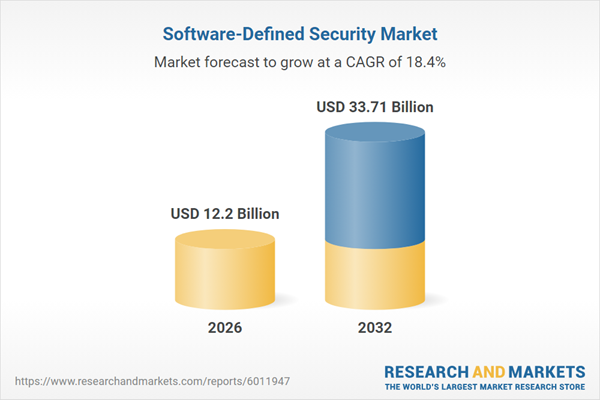
| Forecast Period | 2026 - 2032 |
| Estimated Market Value ( USD | $ 12.2 Billion |
| Forecasted Market Value ( USD | $ 33.71 Billion |
| Compound Annual Growth Rate | 18.4% |
| Regions Covered | Global |
| No. of Companies Mentioned | 11 |