Speak directly to the analyst to clarify any post sales queries you may have.
10% Free customizationThis report comes with 10% free customization, enabling you to add data that meets your specific business needs.
For example, when a user logs into a banking website on a computer, they may receive a unique code on their mobile device via a voice call or text message to confirm their identity. This dual-channel approach enhances security by making it significantly more difficult for attackers to gain unauthorized access, as they would need to compromise both channels simultaneously.
The need for enhanced identity verification mechanisms has driven the adoption of Out of Band Authentication across multiple industries, including banking, healthcare, e-commerce, and government sectors. Cyberattacks are becoming increasingly sophisticated and frequent, often targeting sensitive personal and financial data. In response, organizations are implementing more advanced security solutions to protect users and data integrity. Furthermore, the rise in digital transformation, remote work environments, and cloud-based platforms has increased the risk surface, necessitating more robust and resilient authentication measures. Regulatory frameworks and compliance requirements in many regions also mandate strong identity protection, further fueling market growth.
Key Market Drivers
Surge in Identity Theft and Credential-Based Breaches
The rising volume of identity theft and credential-based breaches has become one of the foremost concerns for organizations globally. Cybercriminals are increasingly targeting login credentials through phishing attacks, social engineering, and brute-force methods. Once credentials are compromised, unauthorized access to accounts, financial services, and enterprise platforms becomes easy, unless there is an added layer of verification.Out of Band Authentication addresses this vulnerability by requiring users to verify their identity through a separate communication channel, which an attacker is unlikely to control simultaneously. This capability is proving essential in industries handling sensitive data like finance, healthcare, and government services. According to the U.S. Federal Trade Commission, over 1.1 million identity theft complaints were filed in 2024, a 25% increase from the previous year. This sharp rise illustrates the growing urgency for organizations to adopt secure, layered authentication mechanisms like Out of Band Authentication to prevent unauthorized access and limit the impact of stolen credentials.
As cyber threats grow in complexity, organizations are shifting from single-layer defenses to more resilient, layered approaches. The adoption of Out of Band Authentication is a strategic response to this evolving threat landscape, offering a low-friction yet highly secure verification method. It prevents bad actors from succeeding even if login credentials are leaked. Businesses are increasingly seeing it as a long-term investment in customer trust and fraud mitigation. Enterprises with large customer bases, particularly in digital banking and e-commerce, are prioritizing Out of Band Authentication in their identity and access management frameworks.
Key Market Challenges
Rising Complexity in Integration with Legacy Systems
One of the most significant barriers to the widespread adoption of Out of Band Authentication technologies is the technical complexity involved in integrating these systems with existing legacy infrastructure. Many large organizations, particularly those in finance, healthcare, and government, still operate on outdated authentication protocols and information technology stacks that were not designed to accommodate modern multi-layered security architectures.Implementing Out of Band Authentication in such environments often requires extensive reconfiguration of back-end systems, the introduction of new interfaces, and potentially disruptive changes to business processes. These changes can result in high integration costs, operational delays, and resistance from internal teams who are wary of changing established procedures. As a result, even organizations with a clear understanding of the cybersecurity benefits may be reluctant to proceed due to the risk of downtime or implementation failure.
The challenge is not just technical but also organizational. Successful deployment of Out of Band Authentication requires seamless interoperability between identity providers, access management platforms, and user-facing applications. In legacy environments, these components are often siloed, fragmented, or supported by outdated vendors. Security teams may face difficulties ensuring backward compatibility, particularly in sectors where systems are not easily altered due to regulatory oversight or certification requirements.
Furthermore, the complexity of aligning multiple departments - such as compliance, operations, and technology - around a unified authentication strategy can slow down the decision-making process. Without a standardized framework for integrating Out of Band Authentication into legacy environments, many organizations view it as a strategic challenge that requires extensive planning, specialized expertise, and considerable resource commitment. As a result, enterprises may delay or limit their deployment of such systems, restricting the overall growth trajectory of the global market.
Key Market Trends
Shift Toward Biometric-Integrated Out of Band Authentication
Biometric technologies are rapidly becoming integral to Out of Band Authentication systems. Instead of relying solely on one-time passcodes or voice calls, organizations are integrating fingerprint, facial recognition, and voice biometrics into the second factor of authentication. This trend reflects a growing desire to reduce friction for users while enhancing the reliability and uniqueness of identity verification methods. Since biometrics are inherently difficult to replicate or steal, they provide a more secure and user-friendly experience. This is particularly valuable in mobile environments where users prefer fast, seamless interactions with minimal manual input.This shift is not limited to consumer-facing applications. Enterprises are also adopting biometric-integrated Out of Band Authentication for internal access controls and remote employee verification. By combining biometric validation with device-based push notifications or app-based challenges, organizations can ensure both possession and inherent identity factors are verified. As biometric sensors become standard in smartphones and laptops, the cost and complexity of deploying biometric-based authentication have declined, making it more accessible to companies of all sizes. This trend is reshaping how businesses approach multi-factor authentication, with a greater focus on convenience, trust, and precision in identity validation.
Key Market Players
- Broadcom Inc.
- Thales S.A.
- RSA Security LLC
- Entrust Corporation
- Ping Identity Holding Corp.
- Okta, Inc.
- Micro Focus International plc
- OneSpan Inc.
Report Scope:
In this report, the Global Out of Band Authentication Market has been segmented into the following categories, in addition to the industry trends which have also been detailed below:Out of Band Authentication Market, By Authentication Method:
- SMS-Based OTP
- Email-Based OTP
- Push Notifications
- Physical Tokens
- Biometrics
Out of Band Authentication Market, By Application:
- BFSI
- Healthcare
- E-commerce
- Government & Public Sector
- Enterprise Authentication
Out of Band Authentication Market, By Deployment Model:
- Cloud-Based
- On-Premise
- Hybrid
Out of Band Authentication Market, By Region:
- North America
- United States
- Canada
- Mexico
- Europe
- Germany
- France
- United Kingdom
- Italy
- Spain
- Asia Pacific
- China
- India
- Japan
- South Korea
- Australia
- Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- South America
- Brazil
- Colombia
- Argentina
Competitive Landscape
Company Profiles: Detailed analysis of the major companies present in the Global Out of Band Authentication Market.Available Customizations:
With the given market data, the publisher offers customizations according to a company's specific needs. The following customization options are available for the report.Company Information
- Detailed analysis and profiling of additional market players (up to five).
This product will be delivered within 1-3 business days.
Table of Contents
Companies Mentioned
- Broadcom Inc.
- Thales S.A.
- RSA Security LLC
- Entrust Corporation
- Ping Identity Holding Corp.
- Okta, Inc.
- Micro Focus International plc
- OneSpan Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 185 |
| Published | August 2025 |
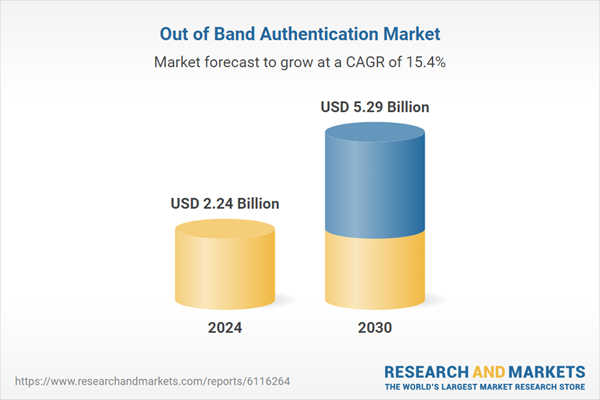
| Forecast Period | 2024 - 2030 |
| Estimated Market Value ( USD | $ 2.24 Billion |
| Forecasted Market Value ( USD | $ 5.29 Billion |
| Compound Annual Growth Rate | 15.4% |
| Regions Covered | Global |
| No. of Companies Mentioned | 8 |